The Kantar Millward study demonstrates the effectiveness of the Mobile Advertising platform Data Rewards.
The objective of the Brand Lift study is to measure the effectiveness of an advertising campaign, identify whether it aids brand awareness, assess whether it is memorable and communicates the most relevant associations of the brand and finally determine whether the campaign shows an intent to purchase.
Movistar Ads Mexico decided to conduct the Brand Lift Insight Study together with one of the best known toast brands in Mexico, Milpa Real of Grupo Bimbo. Using the the winning formula of LUCA Advertising Data Rewards in a video format, the aim was to gain a better understanding of Mexican Toast culture.
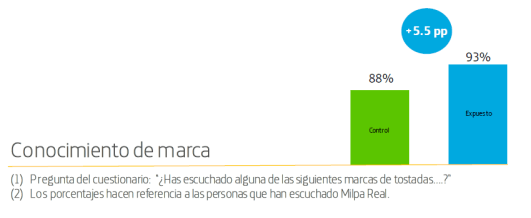
The results produced by Kantar Millward Brown regarding the variable of brand awareness were really amazing: the surveyed group, who were exposed to the campaign through Data Rewards scored 5.5 per person above the control group that did not see the campaign, which means that the surveyed group had a greater awareness of the brand.
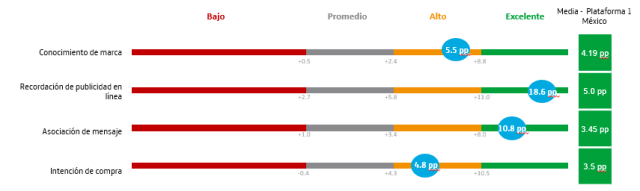
One of the indicators that most interested the brand was the association of the campaign/product message with Aztec culture. The result was excellent: the surveyed group scored almost 11 p.p. higher than the control group that did not see the toast campaign.

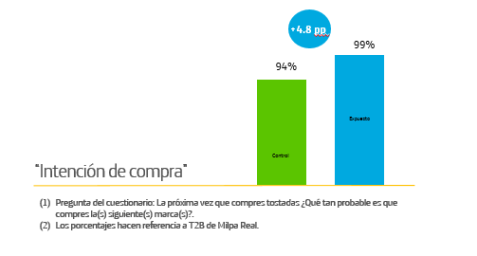
Kantar Millward Brown stated in the study that Milpa Real’s ability to increase Brand Awareness through the campaign resulted in a higher intent to buy, which was reflected in the score of 4.8 p.p. higher than the control group.
Finally, it is worth mentioning the effectiveness of the Data Rewards campaign compared to other major digital platforms that have a bigger presence in the advertising market. In this case, the results were again favourable for the Data Rewards campaign.
In campaigns launched on one of these important platforms, the difference between the surveyed groups and control is much smaller (a difference of 2.8 p.p. in the message association variable) compared to the analysis conducted by Data Rewards (10.8 p.p. in the message association variable).
To conclude, after analysing all the data presented in the study, it can be stated that LUCA Data Rewards is the mobile advertising platform that ensures 100% of a chosen audience not only understand the brand message but remember it also.
To stay up to date with LUCA, visit our Webpage, contact us and follow us on Twitter, LinkedIn and YouTube.