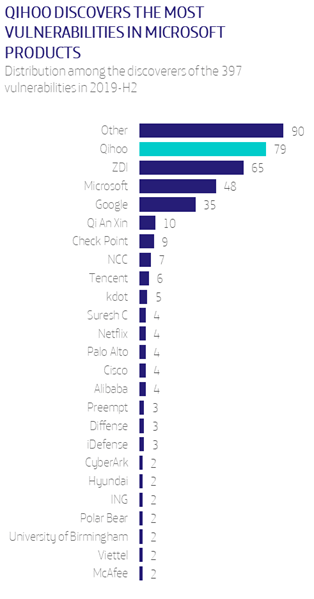
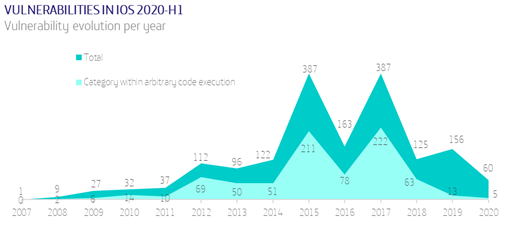
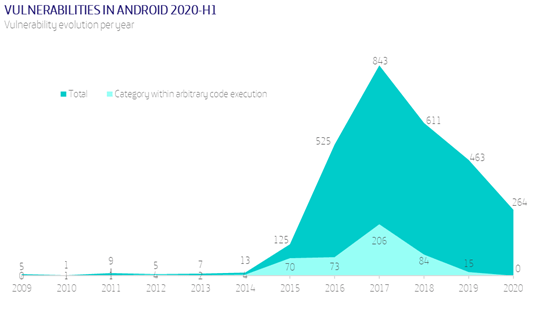
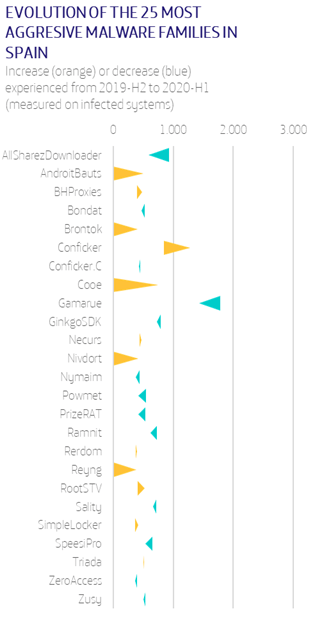
It is increasingly common to see companies that offer their workers the possibility of working from home, combining it with work from the office, and even companies that are born with that vocation and only offer the option of homeworking to their employees.
Unfortunately, during these past months in which the coronavirus has dominated practically all aspects of our daily lives, many companies have been forced to leave their offices. This has a number of information security implications that must be taken into account, both for companies and employees. It is very important to ensure that the handling of connections, backups and data from home does not generate information leaks or allow phishing attacks to succeed.
For this reason, in this new episode of ElevenPaths Radio, our CSA Diego Espitia reviews several events in which these measures were not taken into account and what consequences it caused to employees and companies.
Second episode of ElevenPaths Radio English now available
Discover more episodes of ElevenPaths Radio English: