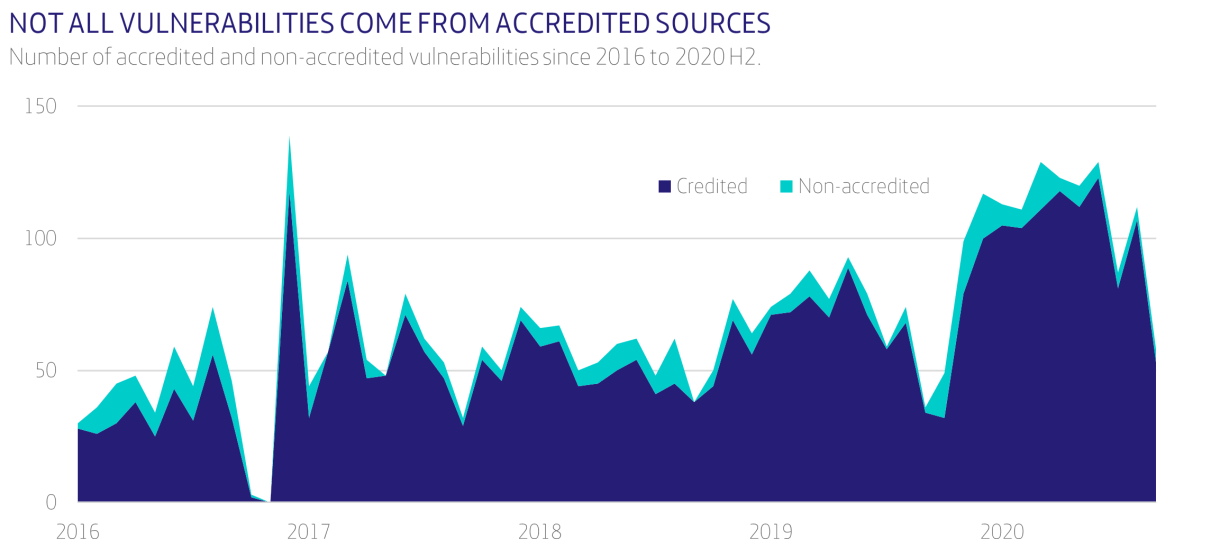
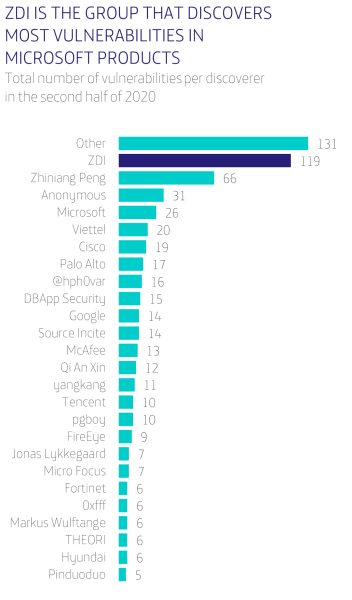
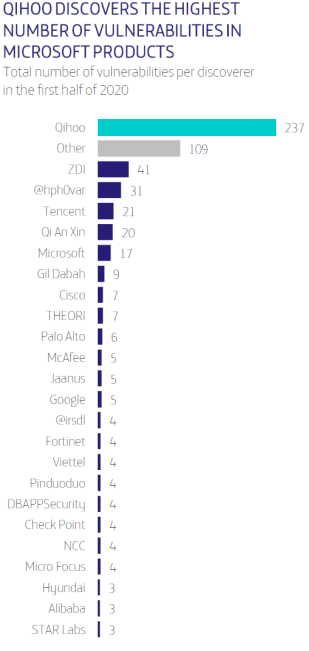
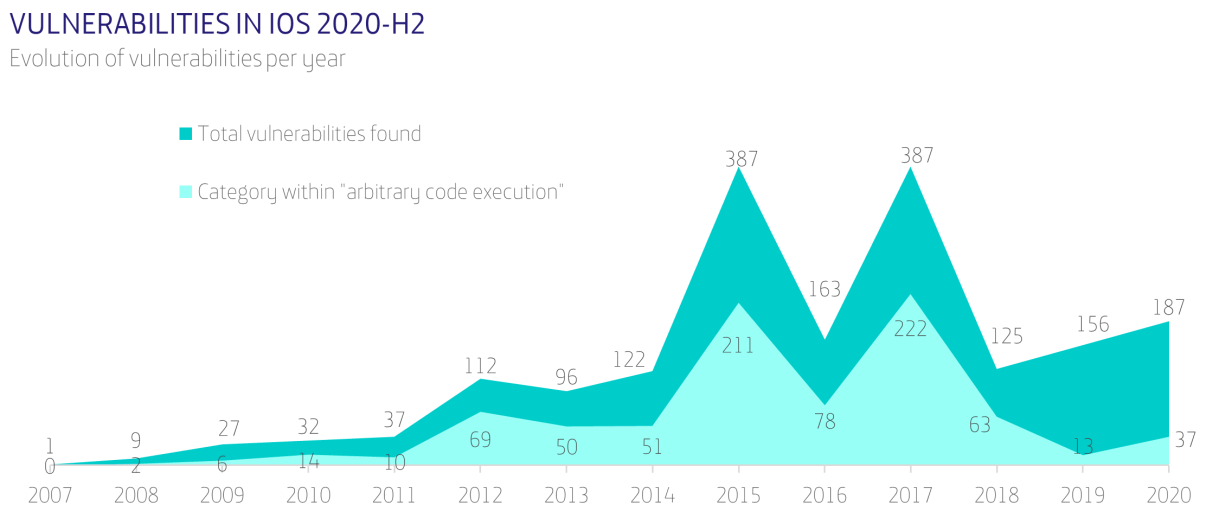
With an estimated current global market value surpassing 406 billion USD, the fashion industry is one of the most significant yet vulnerable industries out there. In an ever-worsening socio-economic climate, analysts predict a grave year for fashion retailers, expecting consumer expenditure on fashion to fall by between 27% and 30% globally throughout 2021 as the world continues to battle through the COVID-19 pandemic.
With this in mind, today, we bring you an insight into how technologies based in Big Data and Artificial Intelligence (AI) are giving many fashion retailers the edge, helping them stay afloat where others have gone under.
Data Driven Supply Chain Management
Inditex, a leading Spanish multinational fashion retailer with over 7,200 stores globally, has, for many years, been leveraging AI both in store and on the e-commerce side to shape product decisions.
A data driven supply chain management system is used across all Inditex brands to support the ‘fast fashion’ model which underlines their business strategy.
Upon releasing a new season of clothing, Inditex will send only a small quantity of each product to their stores and e-commerce channels in order to first gauge the customer response to each item before placing any significant order with the manufactures.
Sales figures of each item are then recorded and internally processed. Machine Learning algorithms then automatically instruct systems to only order an appropriate amount of stock for each item at each individual location. In this way, the manufacturing process can be dynamically adjusted to only produce what is likely to sell, optimising revenue and minimising product waste.
What’s Next in Fashion?
Internal processes such as the fast fashion model described above, are not, by themselves sufficient to remain competitive in the cutthroat world of high street retailing.
Predictive analytics based on competitor and market behaviour are becoming increasingly important to retailers as they dynamically make decisions on all aspects of their business, from pricing to product launch dates. Data firms partner with major brands, to offer insights into the state of the market, future demand and competitor behaviour patterns.
Through compiling data on the top selling products of the moment across a variety of brands, algorithms can suggest which styles are likely to be successful going into the future, for example, the algorithm may suggest that a striped bathing suit is likely to be more successful this summer than a dotty one, based on consumer behaviour leading up to this point.
Furthermore, by comparing pricing data with demand patterns for individual products or collections, algorithms can predict at which price point a certain collection is likely to be successful for each individual brand.
These insights allows designers and retailers to stay ahead of the curve and plan future collections based on hard data insights.
Final Thoughts
Data driven decisions are becoming increasingly valuable as fashion retailers are tasked with understanding their consumer’s wants at a time of rapid socio-economic change and uncertainty. AI technology allows for a more dynamic design and manufacturing process and insights allow brands to identify and take advantage of relevant trends.
To keep up to date with LUCA visit our website, subscribe to LUCA Data Speaks or follow us on Twitter, LinkedIn or YouTube .