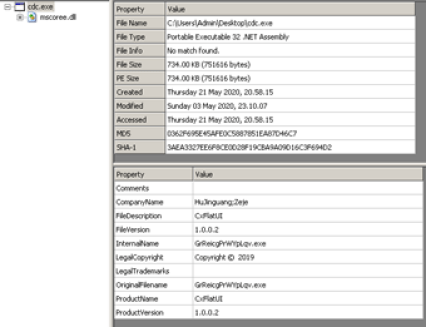
ElevenPaths and Fortinet partner to improve cybersecurity in infrastructure and industrial processes by delivering comprehensive OT, IT and IoT solutions to its customers
ElevenPaths, the cybersecurity company of Telefónica Tech, and Fortinet, a global leader in broad, integrated and automated cybersecurity solutions, announced today the expansion of their collaboration to offer new managed security services for industrial sector customers to provide advanced security for their operation technology (OT), information technology (IT) and Internet of Things (IoT) environments.
Through this expanded partnership, ElevenPaths is leveraging the Fortinet Security Fabric’s solutions for industrial controls systems to meet organizations’ growing demand for managed security services to ensure OT and IT environment are protected and compliant. ElevenPaths will offer its customers Fortinet’s OT security solutions with best-of-breed threat protection for corporate IT environments that extend from the data center, to the cloud, to the network perimeter, combined with the global reach and extensive experience of Telefónica’s security professionals to provide the best service to different industrial sectors.
“Many of our clients are undergoing digital transformations where OT and IoT technologies play a leading role. Although there are significant benefits to these technologies, they also introduce greater exposure to security risks that must be properly managed and addressed. Fortinet’s technology is an integral part of our cybersecurity offerings and strategy to ensure we’re addressing our customers’ new and growing security risks,” said Alberto Sempere, Director of Product and Marketing at ElevenPaths.
Fortinet has the most comprehensive suite of solutions for the protection of industrial environments in the cybersecurity market. As an established leader in OT security and safety, Fortinet is able to address a wide range of challenges from siloed IT and OT environments, providing instant protection of vulnerabilities and secure remote access, thus addressing the cybersecurity, safety and reliability challenges being faced by the OT industry.
“Fortinet and ElevenPaths have a longstanding partnership, working together to help our customers secure their rapidly evolving digital innovations. We’re thrilled to further expand our collaboration to combine ElevenPaths security services with Fortinet’s broad, integrated and automated Security Fabric capabilities to provide advanced security to OT networks and critical infrastructures,” said John Maddison, Executive Vice President of Products and CMO at Fortinet.
ElevenPaths is positioned as a leader in cybersecurity for industrial environments, bringing the knowledge of its multidisciplinary teams of experts, the capacity of its intelligent MSSPs that offer global managed services, as well as its experience as a critical communications operator and a provider of physical security services to offer a differentiating digital security proposal to its customers worldwide.
“The challenge of digitalization in the industrial sector is a reality in Latin America markets. Despite being a sector that is more resistant to change and evolving at a slower technological pace, the words savings, optimization, acceleration, and improvement are starting to be among the main concerns of OT and IT leaders. A partner, like ElevenPaths, that can reach the market, is key to supporting industrial sectors with Fortinet solutions to minimize cybersecurity risks, allowing organizations to take advantage of the visibility and added value delivered by new technologies to monitor and optimize real-time production processes, making them safer, simpler, more efficient and profitable,” said Joao Horta, Vice President of Sales to Service Providers at Fortinet for Latin America and the Caribbean.
Fortinet and ElevenPaths have been working together for several years, and in June 2016 they strengthened their collaboration by incorporating Fortinet’s Security Fabric platform into ElevenPaths’ managed security services. Now ElevenPaths will be leveraging Fortinet’s IT, OT and IoT security solutions, further expanding their strategic partnership. ElevenPaths is an MSSP Expert Partner working together in Europe and Latin America to strengthen the security of mutual customers.
ElevenPaths is also a Fabric-Ready technology alliance partner in Fortinet’s Open Fabric Ecosystem. The Fortinet Open Fabric Ecosystem is one of the largest in the cybersecurity industry with over 360 technology integrations, and extends the benefits of the Security Fabric to mutual customers, and enables them to attain advanced and comprehensive security across their infrastructure.
Cybersecurity is one of the digital services offered by Telefónica that has recently been integrated, together with cloud and IoT/Big Data, into Telefónica Tech, a new unit that brings together these three businesses with high growth potential, focused on supporting its customers with their digital transformation.