We already have a winner of TheTHE‘s plugin contest.
What is TheTHE? This is our collaborative IoC analysis and research all-in-one tool. TheTHE is a simple, shareable, expandable and team-focused Threat Hunting environment. Anyone can develop a plugin to increase the capabilities of this tool, and now we have more and better plugins thanks to those who took part in our #EquinoxRoom111 contest.
What is TheTHE for? A given IoC comes to your hands, for instance a hash, URL, IP or suspicious domain. You need to find out some basic information: Is it malware? Is it in any repository? Since when? Whois? Source country? Is it in pastebin?
You start to open tabs, enter passwords in the different services and launch queries. Hopefully, you have an API shared with a co-worker and, after checking several systems, you open a TXT to recopy the data to the intelligence platform. Your co-worker, who you share those APIs and passwords with but who is on your computer elsewhere in the world, does the same because the same IoC has also reached his or her hands. This is over with TheTHE.
Contest Winner
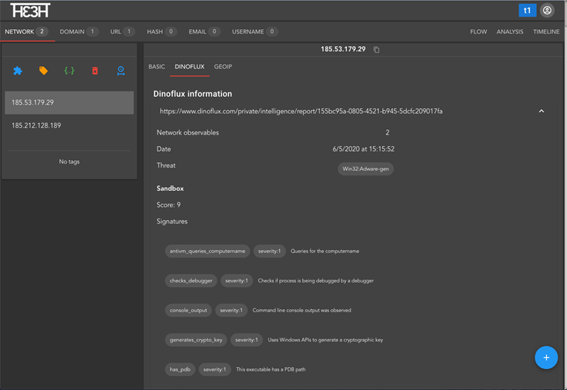
The winner is Santiago Rocha, who has developed a plugin for TheTHE that connects to our sandbox and intelligence service Dinoflux. The information added by Dinoflux to any IoC is very rich, since it is based on the detonation and cross enrichment of the samples. Thanks to Santiago’s plugin we will be able to gather more and better information about the analyses performed on the binaries. Although it is also possible to apply any type of IoC, such as an IP address, and check if it is connected to any malware.
Congrats, Santiago!
As we already posted, all the other plugins received will be included in TheTHE’s GitHub. Thank you all very much for your participation.