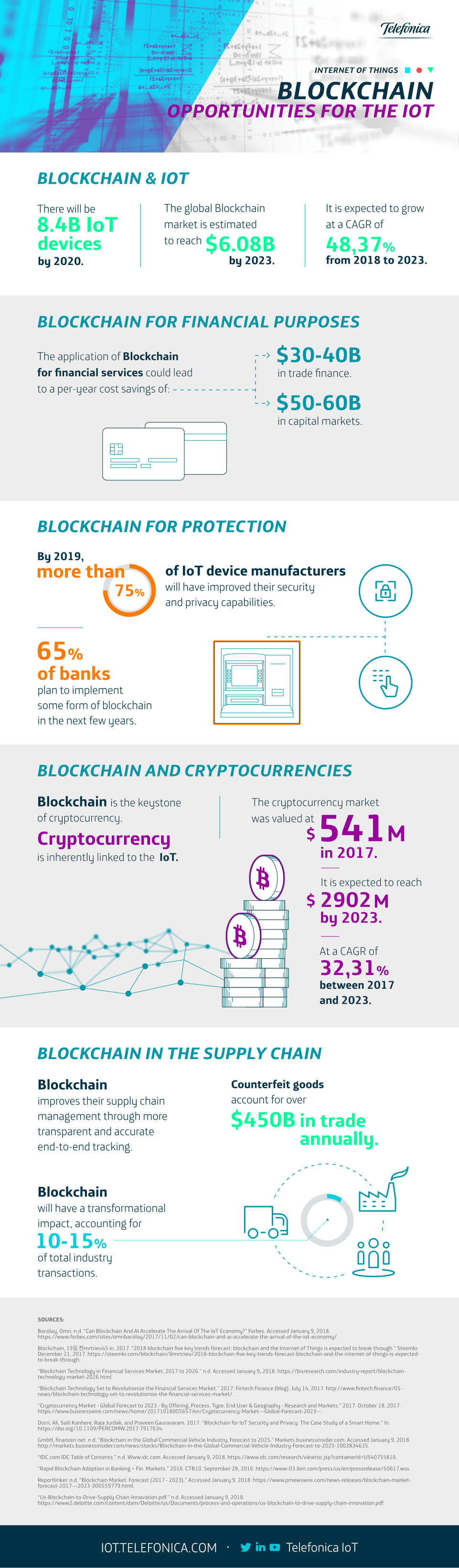
From taking the metro, to choosing a film that best fits your tastes, the presence of data is undeniable in many areas of our lives. However, there are some professions that you never would have associated with the use of data. Have a read of this list of 5 jobs that use Data Science, had you thought of them before?
1. Professional Sports
 |
| Figure 1 : Movistar Team use Big Data to analyze, predict and strategize their races. |
2. Movie Stars
3. Security
 |
| Figure 2 : Police forces can use data science to map high and low risk areas in their cities. |
4. Journalists
5. Medical Professionals
 |
| Figure 3 : Data science helps doctors make more accurate diagnoses. |