
SandaS GRC
- General safety guide
- Security guide for ecosystems of services
- Security guide for device ecosystems
- Security guide for network operators



 |
| Figure 1 : Big Data anlysis is used to analyze the key variables of eSports gamers. |
 |
| Figure 2 : Telefonica entered the eSports arena in January 2017 as Movistar Riders. |
As the interest and revenues in eSports games such as League of Legends has risen, the top teams have become more professional by taking tools and methodologies from traditional sports such as football and baseball. The Riders have their own 1,000 square metre training centre in Madrid and a physiotherapist to reduce the impact of injuries. But unlike the superstar footballers who are guided to the peak of their profession from childhood, the Riders quickly go from playing games at home to competing in front of thousands of people in attendance, and sometimes millions more watching around the world.

 |
| Figure 1 : An image showing the ‘jungle’ in Calais, a refugee camp in the North of France. Source Michal Bělka |
When the refugee crisis first erupted, nobody predicted the extent of the strain that would be felt on many international borders, particularly those in Europe. ‘Frontline States’ such as Jordan, Lebanon, Turkey and Greece have felt the full force of this disaster as refugees seek temporary homes there and seek to move on to Western Europe.

 |
| Figure 1 : LUCA will be showcasing the best in Sports Analytics at the Mobile World Centre. |
The Mobile World Centre is an initiative of the Mobile World Capital Foundation and Telefonica, with the aim of showing how the mobile and internet worlds transform out lives. Motivated by this initiative and due to the influx of people who will be visiting Barcelona, it was a good moment to showcase Big Data and Artificial Intelligence with LUCA and their backing of Sports Analytics.
 |
| Figure 2 : How close could you get to Alejandro Valverde’s race metrics? |
 |
| Figure 1 : Attendees can take on the Movistar Riders at League of Legend. |

 |
| Figure 1 : Over half of teens and adolescents experience cyberbullying. |
Twitter once called itself the “free-speech wing of the free-speech party” but recent years have seen a movement towards tighter control of what is posted on the platform, and other sites have followed suit. For example, Instagram recently implanted the DeepText algorithm already used by Facebook to clamp down on cyberbullying. The machine-learning algorithm is capable of analyzing thousands of posts and comments each second in order to detect. First introduced to tackle issues of spam, Instagram later decided to use the same technology to block offensive comments.
Linked to the subject of cyberbullying is the wider topic of hate speech. In response to the 2016 US election, where hate speech became a globally talked about issue, the nonprofit newsroom Propublica decided to act. They worked alongside the Google News Lab to develop the Documenting Hate News Index, which collates all news related to hate incidents. The site uses Google’s Natural Language API (a machine learning tool) to understand the news report’s nature and its intentions. At the time of writing, the “keyword” most talked about is Jacqueline Kent Cooke, who has just been charged with an anti-Semitic assault on New Year’s Eve.

The popular fitness tracking app Strava proudly published a 2017 heat map showing activities from its users around the world, but unfortunately, the map revealed locations of the United States military bases worldwide. Strava which markets itself as a “social-networking app for athletes” publicly made available the global heat map, showing the location of all the rides, runs, swims, and downhills taken by its users, as collected by their smartphones and wearable devices like Fitbit. Since Strava has been designed to track users’ routes and locations, IUCA analyst Nathan Ruser revealed that the app might have unintentionally mapped out the location of some of the military forces around the world, especially some secret ones from the United States.
However, information from cartographic systems on facilities of interest to the defense, such as military bases, has always been available. Subject to errors or inaccuracies, but always available given the inability of governments to limit their dissemination. In this sense, this type of information has been used to perpetrate attacks, to the point that India raised in 2009 the closure of Google Earth as a measure to avoid attacks like those in Bombay.
From the point of view of privacy, Strava is not the only platform that exposes information of its users by default. Endomondo also allows to know habits, schedules and health status of its users. Or, a few years ago, with the default configuration of Twitter, you could know where the tweets of a user were published. Or, for example, with Tinder it is possible to locate our objective, knowing what area it is in, when it will work, what routes it takes or if it is in the city. This case is another demonstration of the need to evaluate the level of information exposed from an organization and more if it is about facilities of interest for the defense and to include this threat as part of the counterintelligence plans of an organization.
More information at The Hacker News

Investors who were eagerly waiting for their opportunity to join the Bee Token ICO were robbed for 100s of ETH. Scammers managed to get their hands on the Bee Token mailing list and sent out a phishing email stating that the ICO was now open, followed by an Ethereum address to send their contributions to. To try and entice people to send their ETH, the scammers also stated that they had formed a surprise partnership with Microsoft and would be giving participants a 100% bonus for all contributions in the next 6 hours. If that wasn’t a big enough red flag, the scammers guaranteed that the value of Bee Token would double within 2 months, or your would receive your Ethereum back.
More information at The Ripple Cryptocurrency

Major global technology providers SAP, Symantec and McAfee have allowed Russian authorities to hunt for vulnerabilities in software deeply embedded across the U.S. government, a Reuters investigation has found. In order to sell in the Russian market, such as the energy and financial sectors, the tech companies let a Russian defense agency scour the inner workings, or source code, of some of their products. Russian authorities say the reviews are necessary to detect flaws that could be exploited by hackers. But the Pentagon is not alone in expressing concern. Private sector cyberexperts, former U.S. security officials and some U.S. tech companies told Reuters that allowing Russia to review the source code may expose unknown vulnerabilities that could be used to undermine U.S. network defenses.
According to the alert published by the KISA, the vulnerability affects the latest Flash Player version 28.0.0.137 and earlier. The zero-day vulnerability could be exploited by an attack by tricking victims into opening a document, web page or email containing a specially crafted Flash file. According to the researcher Simon Choi the Flash Player zero-day has been exploited by North Korea since mid-November 2017. The attackers exploited the zero-day vulnerability in attacks aimed at South Korean individuals involved in research activity on North Korea.
WannaMine is a Monero cryptocurrency miner that hijacks a system’s CPU cycles to mine. This fileless malware leverages advanced tactics and techniques to maintain persistence within a network and move laterally from system to system. First, WannaMine uses credentials acquired with the credential harvester Mimikatz to attempt to propagate and move laterally with legitimate credentials. If unsuccessful, WannaMine attempts to exploit the remote system with the EternalBlue exploit used by WannaCry in early 2017.
More information at CrowdStrike
Coincheck, a Tokyo-based cryptocurrency exchange, has suffered what appears to be the biggest hack in the history of cryptocurrencies, losing $532 million in digital assets (nearly $420 million in NEM tokens and $112 in Ripples). The digital-token exchange has already reported the incident to the law enforcement authorities and to Japan’s Financial Services Agency to investigate the cause of the missing tokens.
More information at Security Affairs
More information at Bitdefender

Understanding emotions is crucial in new marketing strategies. Due to the oversaturation of products and approaches, new formulas have to be found that help the retail sector sell an increasing number of products. Knowing clients’ emotions can be a fundamental advantage in this respect. So how can we get this information? The technology associated with the Internet of Things is the key that will open the doors to a more efficient and satisfactory way of buying.
Of course, the first step in understanding what a client is feeling is to detect their emotions. This may seem like science fiction, but it is the subject of study by many behavioural specialists. Emotions are reflected in things as simple as our face, our tone of voice or our gestures. And to be able to detect patterns, the first thing we need to do is measure them.
For example, you can analyze the expression of a face or its gestures to know if a customer is surprised, pleased or bored. Facial patterns are currently an inexhaustible source of study for various topics because they provide a lot of information on the emotions we feel.
On the other hand, the voice is also an inestimable source of information. We can detect accents, tones, nuances, doubts and a host of features from it. By 2022, over 70 millionhouseholds will have at least one voice assistant in their home, and the total number of devices installed will top 175 million. According to several studies, you can also ascertain a person’s interest in a topic via their voice.
If we add this to the biometric data that can be obtained from other wearables, such as the increasingly popular wristbands that measure the heart rate or skin moisture, the amount of data we can collect on the emotions generated in a person is huge.
Once we get the right measurements from a multitude of connected devices (cameras, voice assistants, biometric wristbands), the next step is to analyze them. To do this, nothing fits the bill better than Artificial Intelligence.
The technology associated with AI allows us to analyze patterns that at first seem chaotic or too complex. Thanks to Artificial Intelligence, we can create algorithms that learn and improve with the data they process, so they collect information in an increasingly efficient way.
Big Data appears alongside Artificial Intelligence to offer the possibility of using massive amounts of data to better analyze the parameters that determine clients’ emotions. And all this, from the collection of information to its distribution and processing, is done thanks to Internet of Things.
When talking about emotions, the IoT is facing a new market niche in which marketing has a lot to gain. Yet so does Internet of Things itself, since this type of analysis will allow it to be more effective in all its tasks. With the results of these analyses, developers can generate more pleasant or efficient applications.
Designers, administrators and ultimately everyone related to a brand can also learn something. The information obtained from emotions, which are a manifestation of our desires, among other things, will make IoT applications better in all senses.
Thus, a music player could adapt its automatic song list to the user’s mood at that moment. Thanks to connectivity, the application could send a signal to a nearby business that had a beacon so it could offer information (an ad, for example) which is especially relevant to the user’s mood. And this is just one example.
All of this is not just about usability. IoT involves many aspects: colours, sounds, touch, aesthetics, lights, the combination of all of them. With this analysis of emotions, the IoT has a great deal to gain by adapting the characteristics of a product or an application to the mood of a user automatically and in real time, thanks to the connectivity offered by Internet of Things.

 |
| Figure 2 : The Beijing skyline – China is in a ‘two-way race’ with the US for AI dominance. |
Spain is tackling safe use and ethics

 |
| Figure 2 : In addition to the awards, many artists will perform their songs live at the event |

You want your organization to be cyber-resilient but you have no means?
You have advanced security solutions in place, but you lack skilled staff trained to take advantage of them?
You are unable to detect and respond to a security breach and you fear the consequences for your business of the NIS and GDPR legislation?
If you are concerned about these issues, we are also concerned, and that is why we have been working with our skilled analysts, Test Lab and Strategic Partners strive to offer our customers a Managed Detection and Response service beyond the traditional approaches.
Most information security professionals in Europe believe a cyber attack will breach critical infrastructure across multiple countries within the next two years, according to Black Hat’s annual report¹ “The Cyberthreat in Europe”. Security professionals in Europe feel they do not have the time, budget, or staff to meet the growing security challenges and the additional burdens imposed on them by regulations such as GDPR and NIS Directive:
A traditional Security Operations Center (SOC), using blocking, monitoring and vulnerability management techniques, can mitigate up to 90% of attacks. The remaining 10% of attacks, caused by sophisticated attacks aimed directly at the organization, is the main concern for 48% of security professionals, according to the Black Hat report.
Threat hunting helps with threats that bypass both preventative and detective controls, and enables organizations to uncover threats that would otherwise remain hidden. According to Gartner’s threat hunting report², hunting success relies on a mature security operations center (SOC) and cyberincident response team (CIRT) functions. In the same way concluded McAfee³ at the end of July, with his new interesting report “Disrupting the Disruptors, Art or Science?”, by investigating the role of cyberthreat hunting and the evolution of the security operations center (SOC).
The study found that 71% of SOCs with a level 4 maturity closed incident investigations in less than a week because of the context provided by skilled threat hunters.
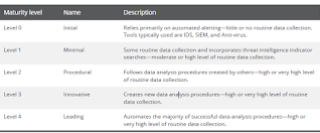 These organizations were twice as likely to automate parts of the attack investigation process, and they devote 50% more time to actual hunting.
These organizations were twice as likely to automate parts of the attack investigation process, and they devote 50% more time to actual hunting.
Perhaps the SOC of your organization may effectively cover SIEM, IDP, vulnerability management and other areas. However, the next phase of maturity is to build the APT Threat Hunting capability. Gartner⁴ has called Managed Detection and Response Services (MDR) those new security service providers that are focused on detecting previously undetected threats that have breached an organization’s perimeter and are moving laterally through the IT environment. Gartner recommends to augment existing security monitoring capabilities to address gaps in advanced threat detection and incident response, and anticipates that by 2020, 15% of midsize and enterprise organizations will be using services like MDR, up from less than 1% today.
According to last SANS Insitute’s report⁵ about effective threat hunting, the chances are very high that hidden threats are already in your organizations networks. Organizations internally realize the discovery of the security breach only in 53% of the cases, compared to 47% that are communicated to the organization by an external third party, according to last FireEye’s M-Trends 2017 report⁶. The median dwell time (the duration a threat actor has in an environment before they are detected) of EMEA organisations is 106 days.
When do you have proof in your organization that you have a security breach? Can you detect it by yourself, or by third parties? You may need to accelerate your advanced threat detection capabilities through an MDR service.
As of May 2018, NIS Directive identified operators of essential services (OESs) and digital service providers (DSPs), and GDPR identified controllers and data processors, will have to take appropriate security measures and to notify serious incidents to the relevant national authority. In the case of the NIS Directive, breach notifications must be done by “without undue delay⁷”, and in the case of GDPR also “without undue delay and, where feasible, not later than 72 hours after having become aware of it⁸”.
What can constitute an undue delay? What happens if your organization has been breached, but is not aware of this fact due to lack of care? The regulation is deliberately vague to allow a wide range of possible eventualities, and this is where having a complete process of detection and response shows its value, because all this information must be explained to the competent authority or the CSIRT.
In relation to the security measures to be adopted according to the NIS Directive and GDPR, it is indicated that “having regard to the state of the art¹⁰” or “taking into account the state of the art” respectively, these measures will guarantee a level of security of networks and information systems (NIS) and data protection (GDPR). Artificial Intelligence (AI), automated threat detection and proactive threat hunting are powerful tools that need to be leveraged by businesses if they are going to stand a chance of meeting the new requirements set out by NIS Directive and GDPR. And if you do not have your own means, there are already MDR services available in the market that offer specific experience to support organizations that seek to improve their threat detection and response capabilities.
ElevePaths’ Managed Detection & Response
Organizations can’t afford to believe that their security measures are perfect and impenetrable, no matter how thorough their security precautions might be. Having a perimeter and defending it are not enough because the perimeter has faded away as new technologies and interconnected devices have emerged.
The objective should therefore be to reduce the window of exposure to a potential security breach and reduce those tasks that require a lot of time to allow rapid detection and action, and conveniently manage risks (cyber-resilience). Companies need to reduce threat identification and response processes from years, months and weeks, to just hours and minutes.
As part of our Cybersecurity Services, we offer our Customers our Managed Detection & Response services, based on skilled and specialized security analysts focused on Endpoint Detection & Response (EDR) for advanced malware and targeted attacks, and high value Indicators of Compromise (IoCs) for early identification of sophisticated threats.
ElevenPaths is an Affiliate Member of the Cyber Threat Alliance to contribute to the development of a new, automated threat intelligence-sharing platform to exchange actionable threat data, and also an Associate Partner of the No More Ransomware initiative, to disrupt cybercriminal businesses with ransomware connections. Please stay tuned to discover soon what new solutions and alliances with the state-of-the-art Partners we add to our Managed Detection & Response services.
¹ “The Cyberthreat in Europe” – The 2017 Black Hat Europe Survey
² “How to Hunt for Security Threats”, Gartner – April 6, 2017
³ “Disrupting the Disruptors, Art or Science?”, McAfee – July 2017
⁴ “Market Guide for Managed Detection and Response Services”, Gartner – 10 May 2016
⁵ SANS Institute, “The Who, What, Where, When, Why and How of Effective Threat Hunting”, Last Updated: August 29th, 2017
⁶ “Mandiant® M-Trends® 2017 report”, FireEye – March 14, 2017
⁷ Article 14.3 NIS Directive
⁸ Article 33 GDPR
⁹ Arts. 14.1 and 16.1 NIS Directive
¹⁰ Arts. 25.1 and 32.1 GDPR