
When cyberattacks occur in large organizations, it is crucial to remember where duplicate files are stored, as this information is also subject to infection by a malware virus or more importantly in this case, by ransomware. Best practice involves first tracking where the information is located and then starting the data clean up, both for Wannacry and other future incidents:
- Files that are not encrypted were not affected by the malware because the malware did not have time to affect them. There are ways to partially recover files affected by Wannacry, which will be shown throughout the course of this article.
- It is important to always have backups and security copies that are available offline.
- Information surrounding the shared units and the cloud units.
- Information from Office365 email and the data units.
- Information from removable devices, i.e. Pen drives.
- Temporary Office files (Word, Excel, PowerPoint). If the infection was present when a document was open, a temporary file will also have been generated. These files will not be on the radar of Wannacry, meaning these files will not become encrypted. Once the files have been cleaned up, Office files can be recovered to the point they were at when Wannacry started. Once the system has been cleaned up, the temporary files generated at the time of infection can be restored.
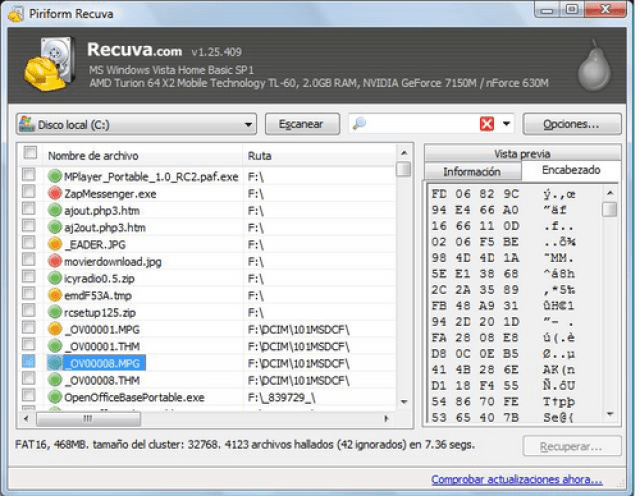
Not all files are moved by the ransomware as it is a random process in which the temporary and encrypted files are created. Due to this, not all files can be recovered.
In the second instance, the malware identifies two data partitions in each system. The malware then creates a second partition at the root of a file named $RECYCLE, which should not be confused with $RECYCLE.BIN. The $RECYCLE file follows the same pattern as before in which files are moved across with the aim of encrypting them. When a file is categorized under the WNCRYT extension, the content has not been lost as it has not been encrypted. As soon as Wannacry encrypts the archive as WNCRYT and it has been converted to the WNCRY format it is officially encrypted.
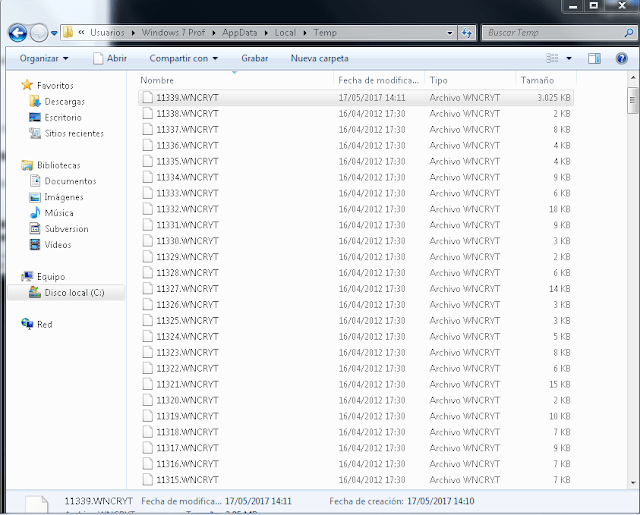
Unfortunately, it is not always possible to find this sort of file. When Wannacry encrypts a file, the corresponding temporary file is deleted, which means that the information is lost. However, if the user turned off or hibernated their system before the process of encryption or infection, the process would be prevented. This would prevent all the temporary WNCRYT files from being encrypted and the previously eliminated files would then be retrievable. These temporary files that are kept under the %userprofile%appdatalocaltemp or $RECYCLE will be available depending on the previously discussed conditions. They will simply have a different file extension.
However, if the ransomware finishes the encryption process for the archives, there would be no temporary files left, which would then stop this recovery process. On the other hand, if the ransomware does not complete the encryption process or the computer is turned off or on sleep mode, this would allow for partial retrieval of information.
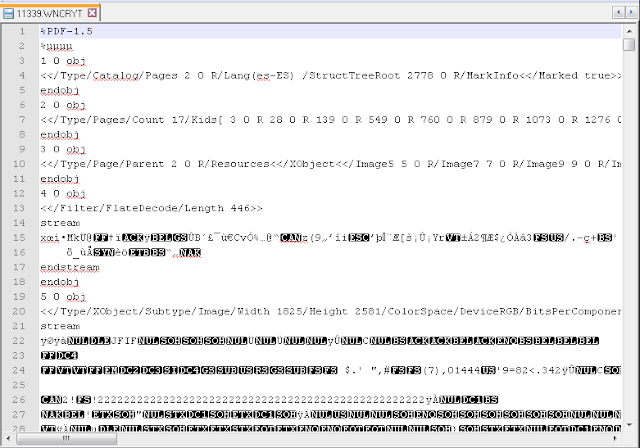
For example, the previous image shows a large amount of temporary files that Wannacry was unable to encrypt. These files would be opened as a PDF file with a heading.

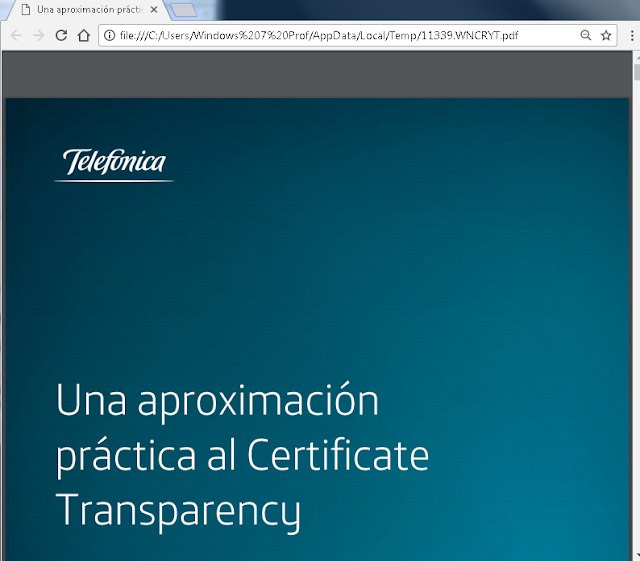
With this background information, here is a useful Telefónica WannaCry File Restorer script to use. This was developed in the labs of Telefónica with the objective of being able to retrieve and restore corrupted files.
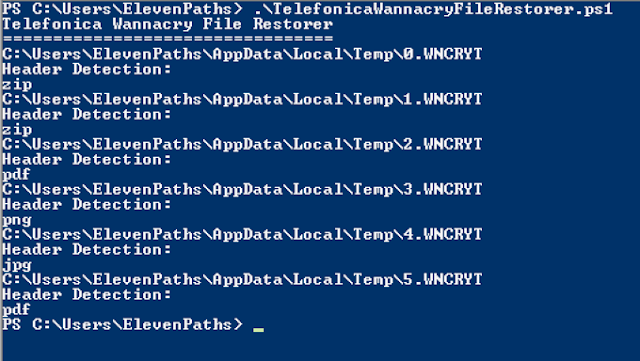
» Telefónica WannaCry File Restorer on GitHub (desktop version)
Latch Antiransomware instalation and configuration
Latch ARW: an AntiRansomware TOOL
WannaCry WITH Latch AntiRansomware






