Taking advantage of all the attention this issue is attracting, the official app markets, Google Play and Apple Store, have been daily deluged with applications. Both platforms, especially Android, has already limited the publication and search of terms such as “covid” or “coronavirus”: Google has declared war against those who try to take advantage of fear to win downloads. Currently, only those belonging to official government bodies remain on Google Play.
For this rapid analysis we will use ElevenPaths’ Tacyt tool, the mobile cyberintelligence ecosystem, where its Big Data structure monitors, stores, analyses and correlates thousands of new applications every day. In addition to collate or compare information which we have access to through easy and simple queries.
One of the advantages that Tacyt offers is that we can have all applications accessible regardless of location. Since Google Play can only offer results based on our country of origin according to the availability proposed by the developer. We go to the Official Google Play repository in Spain and search for those apps related to COVID19.

Nothing to do with the amount of applications found in any unofficial market:
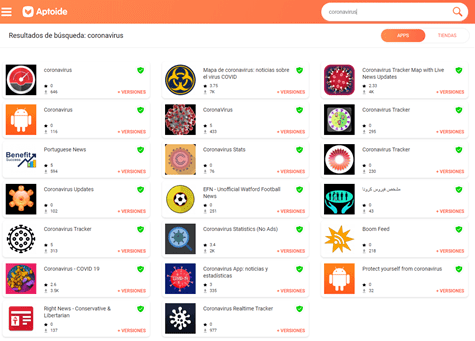
As with other markets, Aptoide, for example, does not directly download the app we have requested but the “downloader” through which the actual download will be requested. This can easily be guessed by checking that the file size is exactly the same:
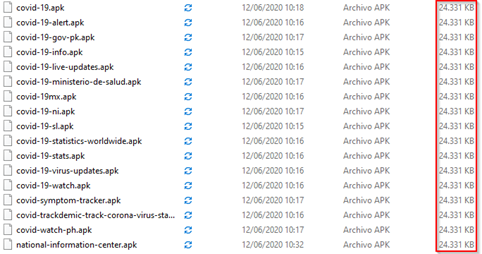
In fact, we easily check it out at Tacyt when uploading these applications. It detects them as one, with identical hash:
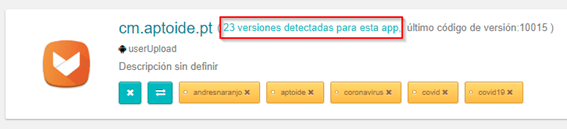
This is due to Tacyt not only including its own application discovery drivers and applications downloading, but also, using the upload function (either via web or API) the user can upload the applications to be analysed. These can be seen labelled as “userUpload” and can also be tagged with our own identification labels (as in the image: the author of the upload or the market from which it was downloaded).
This upload function can be very useful to detect altered versions of our legitimate applications in unofficial markets, for example, from a bank. Tacyt includes a button on the interface to compare applications.
In any case, we do not miss the opportunity to totally discourage the installation of applications from unofficial sources.
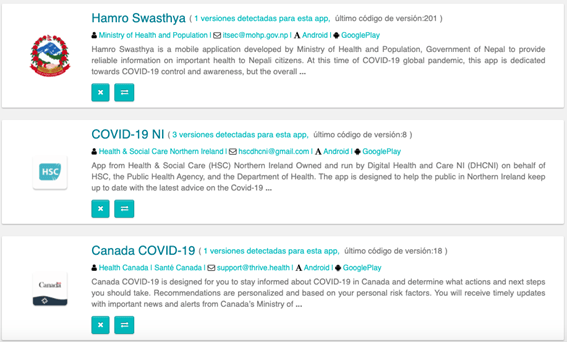
Google Play Search Using Tacyt for COVID19 Related Apps Since the Beginning of the Pandemic
We will focus the research on Google Play. The filters are used to form the next search in Tacyt. As you can see these usual composite queries (dorks) in Google search, for example, are easy to read:
((packageName:*covid19*) OR (packageName:*coronavirus*)) AND (origin:"GooglePlay") AND (createDate:"2020-03-14 00:00:00 - today")
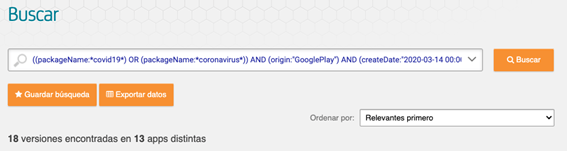
Tacyt’s respond to the previous search:
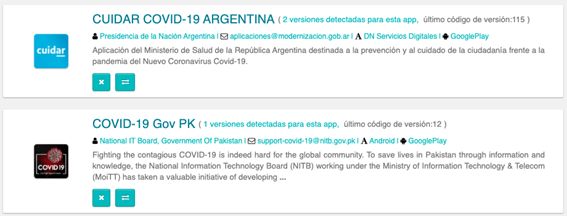
We now search for unofficial apps related to COVID19 using Tacyt from the official date of the start of the pandemic. For this task, we can use the parameter ORIGIN indicating the exclusion of all those whose origin is not the official one. For example -origin:GooglePlay.
((packageName:*covid19*) OR (packageName:*coronavirus*)) AND (-origin:GooglePlay) AND (createDate:"2020-03-14 00:00:00 - today")
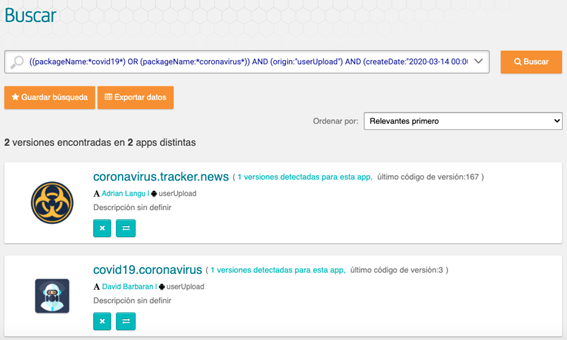
For example we have a look at the permissions of the app with “coronavirus.tracker.news” package name and do a quick scan.
The following permissions are suspicious: (we only comment on permissions different to the “normal” official apps that violate privacy or security)
- android.permission.CHANGE_WIFI_STATE: allows the APP to change the state of Wi-Fi connectivity.
- android.permission.INTERNET: allows the APP to open network connections.
- android.permission.WRITE_EXTERNAL_STORAGE: allows the APP to write in the external storage of the device.
- android.permission.READ_EXTERNAL_STORAGE: allows the APP to read on the external storage of the device.
- android.permission.WAKE_LOCK: allows you to use PowerManager WakeLocks to prevent the processor from going into sleep mode or the screen from getting dark.
For any research, we can load the apps in batches into Tacyt and then search for them using a custom label and locating, for example, as we said, suspicious permissions:
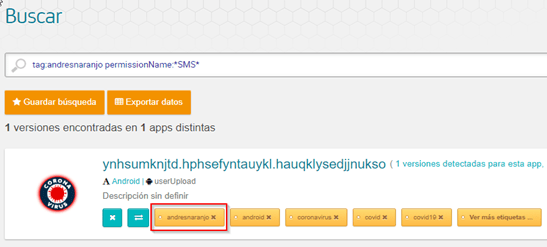
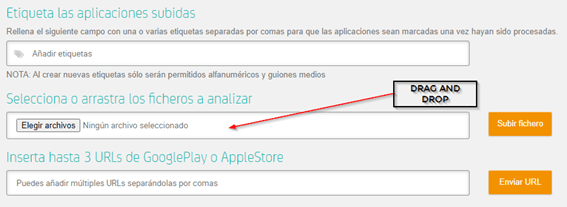
Likewise, we could have used the expiry date of the certificate (sometimes suspiciously long), apikeys, text or emails chains associated with malware, and a long etc…
We will see in the next part some more information about the findings.