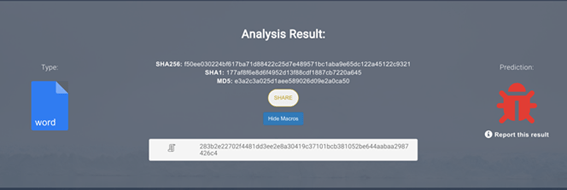
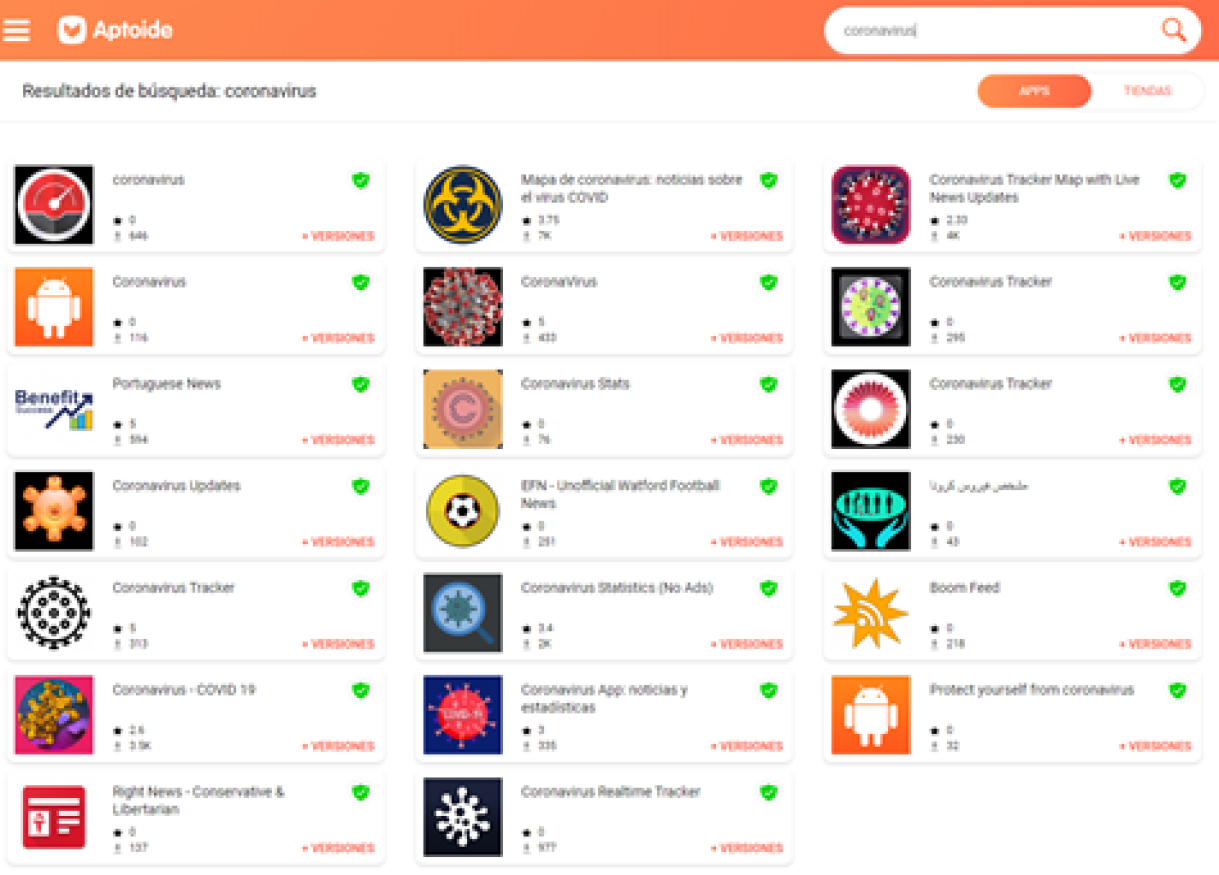
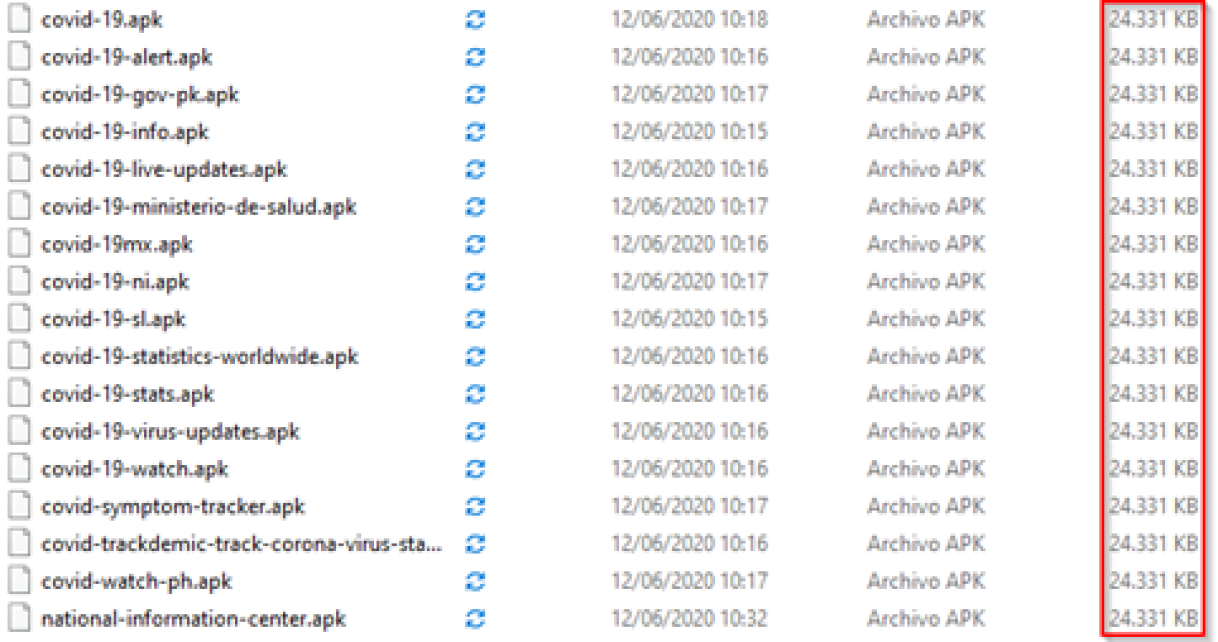
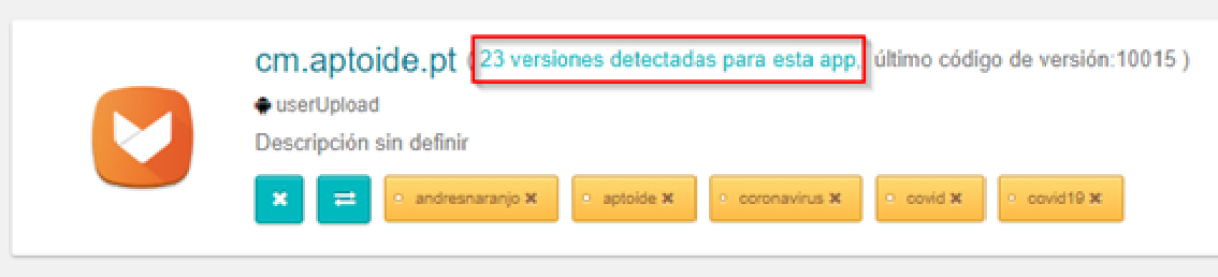
New attack vector for vulnerability in Citrix Workspace
Pen Test Partners security researcher Ceri Coburn has discovered a new attack vector for the CVE-2020-8207 vulnerability in Citrix Workspace corrected in July this year. The problem lies in a command line remote injection vulnerability that would allow attackers evade Citrix signed MSI installers by means of a malicious MSI transformation. These MSI transformations allow the database of the MSI file to be altered before it is installed. By being able to control the command arguments that are passed to msiexec, the path could be inserted in a malicious transformation, but using a legitimate Citrix MSI. An update has been published by Citrix to correct this new case study.
More details: https://www.pentestpartners.com/security-blog/the-return-of-raining-system-shells-with-citrix-workspace-app/
Exploits for Zerologon vulnerability used in attacks
Microsoft has warned in a number of Tweets that attackers would be actively using the Windows Server vulnerability listed as CVE-2020-1472 in attacks and advises all Windows administrators to install the necessary security updates. This vulnerability was named ‘Zerologon’ after the cybersecurity firm Secura and, when exploited, allows attackers to elevate their privileges to a domain administrator and take control of a domain. These tweets include three examples that, according to Microsoft, were used in attacks to exploit the privilege elevation vulnerability Netlogon CVE-2020-1472. The examples are .NET executables with the file name ‘SharpZeroLogon.exe’ and can be found at VirusTotal. All Windows Server administrators are strongly recommended to install the security update for the CVE-2020-1472 following the instructions in the Microsoft support newsletter.
All the info: https://www.bleepingcomputer.com/news/microsoft/microsoft-hackers-using-zerologon-exploits-in-attacks-patch-now/
Firefox flaw allows hijacking of browsers via WiFi
Mozilla has fixed a flaw in the Firefox browser for Android devices that would allow to hijack all vulnerable browsers on the same WiFi network and force users to access malicious websites. The vulnerability lies in the implementation of Firefox’s Simple Service Discovery Protocol (SSDP), which allows other devices on the same network to be found in order to share or receive content. In vulnerable versions of Firefox, this protocol could be exploited to send malicious commands to the victim’s browser. The flaw was fixed in Firefox 79, so it is recommended to update the browser as soon as possible.
More information: https://gitlab.com/gitlab-com/gl-security/security-operations/gl-redteam/red-team-tech-notes/-/tree/master/firefox-android-2020
Increase in LokiBot malware activity
The US Cybersecurity and Infrastructure Security Agency (CISA) has warned both government institutions and the private sector about an increase in LokiBot malware activity. The increase in detections related to this malware began last July, in campaigns where LokiBot is used for its functionalities such as: exfiltering credentials, obtaining data, keylogger and screen capture. It also has the ability to function as a backdoor, allowing threat agents to run other types of malware. The entry vector is usually compromise by sending emails, malicious executables or through torrent files. CISA warns users and/or system administrators to take the corresponding mitigating measures proposed by the organisation in order to minimise the risks of possible infection.
More: https://us-cert.cisa.gov/ncas/alerts/aa20-266a
Alien, the malware heir to Cerberus
Researchers at Threat Fabric have identified a new malware close to Cerberus as responsible for the latest campaigns this year that had been attributed to this malware. Alien, as the banking Trojan that attacks Android devices has been called, has an advanced ability to circumvent dual-factor authentication security measures to steal credentials. According to the research carried out, Alien would be capable of stealing passwords from 226 mobile applications, including those of Spanish banks such as BBVA, Bankia, UnicajaMovil and Kutxabank, among others, as well as other applications such as Telegram, Netflix, Intagram and Twitter. According to the research carried out, the main target country would be Spain, followed by Turkey, Germany, the USA, Italy and France. It is also expected that Cerberus-based malware variants will continue to appear during the rest of the year, as it happened with Alien.
All the details: https://www.threatfabric.com/blogs/alien_the_story_of_cerberus_demise.html