One of the factors that indicates the maturity of some branches of technology is the incorporation of improvements as this technology evolves, which are different from those considered at the beginning. Thus, for example, the beginning of the evolution of microprocessors was based on gross power and a progressive, and slow, miniaturisation (mainly due to heat generation and cost issues). As the technology matured, other improvements were introduced, such as the use of several cores within the same processor, power segmentation, reduction in consumption, more effort in miniaturisation… This indicator of maturity in the wireless connectivity of the mobile network has been the 5G standard: the commitment to other improvements with an impact above the usual increase in speed typical of each evolution.
However, this post will not analyse the benefits of 5G connectivity. For that we already have some great articles on our blog. In this one we are going to talk about how this maturity impacts on the industry 4.0 environment.
As we discussed in our previous article, in which we spoke about the approach to cyber security in Industry 4.0, in recent years industry has undergone an intense process of transformation that has been called the “fourth industrial revolution” or “Industry 4.0”. This process of digitalisation and development of new technologies seeks to implement improvements such as real time access to data and business intelligence, which will transform the current perspective in which production processes are carried out, moving one step further towards the so-called “Smart Factories”.
Embracing Industry
The new 5G standard proposes improvements in access to and communication between industrial processes, as well as in the creation of new models and use cases. According to ABI Research, these improvements could reduce maintenance costs by a 30% and increase overall efficiency by a 7%. This is not by chance. As can be seen in the image below, the 5G protocol stands on 3 basic pillars, which offer solutions to the great challenges and advances that the fourth industrial revolution poses.
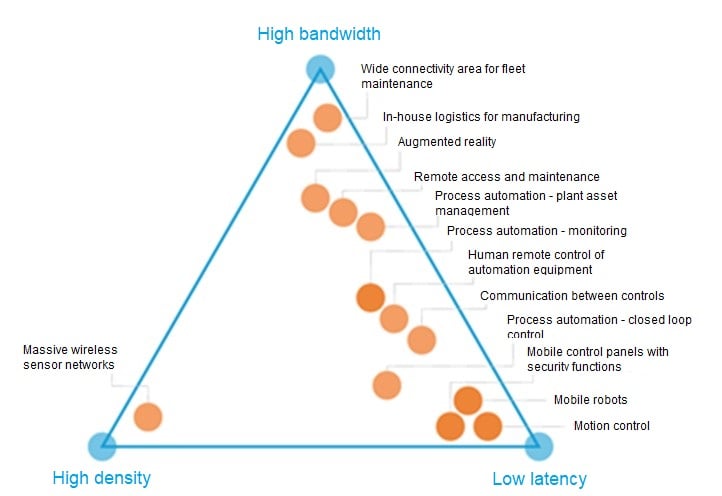
What technologies do they apply in each pillar and what do they consist of? Let’s get into it:
- High bandwidth: eMMB (evolved Mobile Broadband Communications), which enables high transmission speeds. It means that there are no bottlenecks in the transmission of large amounts of information.
- Low latency: URLLC (Ultra Reliable Low Latency Communications), which allows for low latency connections of less than 1 millisecond and high reliability, with a percentage of at least 5 nines (99.999%), equating in performance to connections only attainable through wiring. This is especially relevant in M2M environments, since it minimises the possibility of two machines working in synchronisation being blocked due to latency in the transmission of information or because the connection is not stable.
- High density: mMTC (massive Machine-Type Communications), which allows a high number of devices to be connected simultaneously. In cases where many devices requiring connection are deployed (e.g. sensors) this technology allows the control of the devices at the same time, without causing disconnections or exclusions of any of them.
What About Security?
The heterogeneity of the OT ecosystem means that classic practices such as fault patching or network segmentation (restricting internet access to some of these segments) sometimes become ineffective or directly impossible in the face of the diversity of proprietary devices and protocols, or simply due to the peculiarities of each industrial process.
In addition, a “Smart Factory” requires communication protocols ready to integrate IT, OT and IOT devices. This implies the implementation of different communication networks, both wired and wireless, with their own vulnerabilities and security challenges in an environment (once very isolated) that is not prepared to assume the sudden entry of several devices from other fields.
However, 5G is the enabling technology for this hybridisation that will allow key communications in industry 4.0 to be unified. The great advantage of this generation, in addition to its adoption by all the areas involved, is the implementation of security from the design, as a fundamental point of this standard. Likewise, 5G security not only focuses on individual solutions, but also considers the main risks and environmental threats, analysing the scope of each threat and the cost of its mitigation and remediation.
Some of the most relevant features implemented by 5G are the following:
- Radio interface: in order to prevent manipulation of user data, adaptive protection of user data integrity has been designed, in addition to end-to-end encryption.
- User privacy: unlike 4G, user identification information, such as IMSI (International Mobile Subscriber Identity), is not transmitted in plain text, but encrypted on the radio interface.
- Authentication: the 5G access authentication process is designed to support the Extensible Authentication Protocol (EAP) specified by the IETF, through a new version of the “Authentication and Key Agreement” (AKA) already used in other previous standards.
- Roaming Security: 5G’s service-based architecture defines the security edge protection proxy to implement E2E (end-to-end) security protection for inter-carrier signalling at the transport and application layers. This prevents third-party operator devices from accessing sensitive data.
Such practices are very important, but even more important is that 5G service providers are committed to maintaining a chain of reliability that strengthens the security embedded in the 5G standard. In this sense, Telefónica declares in its Digital Manifesto that security is primary. Its executive president, José María Álvarez-Pallete, declared regarding the “Clean Network” initiative that “Telefónica is proud to be a company with a clean 5G access route”. Currently, both Telefónica España and O2 (United Kingdom) are totally clean networks, while Telefónica Deutschland (Germany) and Vivo (Brazil) will soon be so. This implies that suppliers throughout the supply chain will be reliable, thus minimising a common problem in the area of cyber security.
To Sum Up…
5G connectivity is the necessary element to lead the “fourth industrial revolution”. It is a strategic, well-planned standard that implements the necessary steps to demonstrate that it is a mature technology that is willing to facilitate that leap that makes the use of the technology transparent to the user. In this way, the paradigm of ubiquity in technology, of which Mark Weiser is the creator, will be fulfilled: “the most entrenched technologies are those that disappear”.
We are on track…