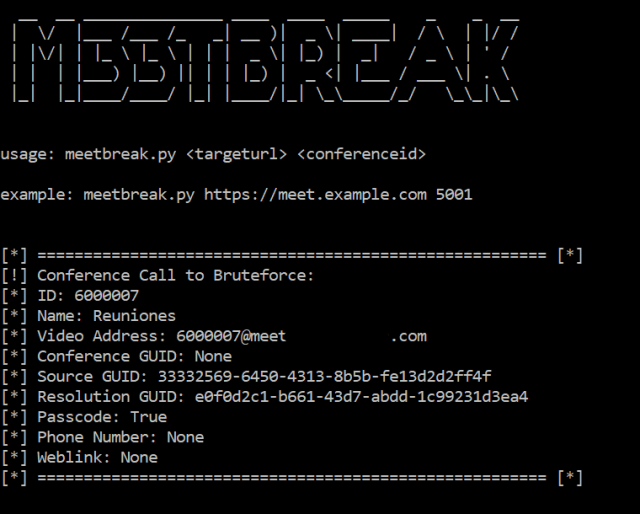
- If you choose program A, you will be able to protect 200 positions.
- If you choose program B, there is a 1/3 chance to protect the 600 positions and a 2/3 chance of not protecting anyone.
- If you choose program A’, 400 positions will be compromised.
- If you choose program B’, there is a 1/3 chance of not compromising any position, and a 2/3 chance to compromise the 600 positions.
- Choice positivity (income) or negativity (loss)
- The order followed to present the choices
- The context within choices are presented
- The type of language (semantics) used to formulate the choices
- Additional information included or left out when formulating the choices
- It provides protection aainst 99,9 % of the attacks
- Only 0,1 % of the attacks are succeeful
- With the new Security Plan, we will save 350,000 € next year
- With the new Security Plan, we will avoid a loss of 350,000 € next year
- You present three potential budgets: 500 K€, 1 M€ and 2 M€
- You present three potential budgets: 250 K€, 500 K€ and 1 M€
- Mum! My girlfriend is pregnant!
- Mum! You are going to be a granma!
- An essential protection layer
- A basic survival mechanism
- The engine driver was on the phone
- The engine driver was answering a call from a RENFE controller
- Plan A will save 1,000 computers from the first unit having 5,000 workers from the same country, where most infections occurred, that is, you will save 1/5 computers, 20% of the computers of that country, the most affected by the malware.
- Plan B will save 2,000 computers, but from the whole organization, that is 100,000 workers, in other words: you will save 1/50 computers, 2% of the computers.
- Plan A will save 1,000 computers
- Plan B will save 2,000 computers