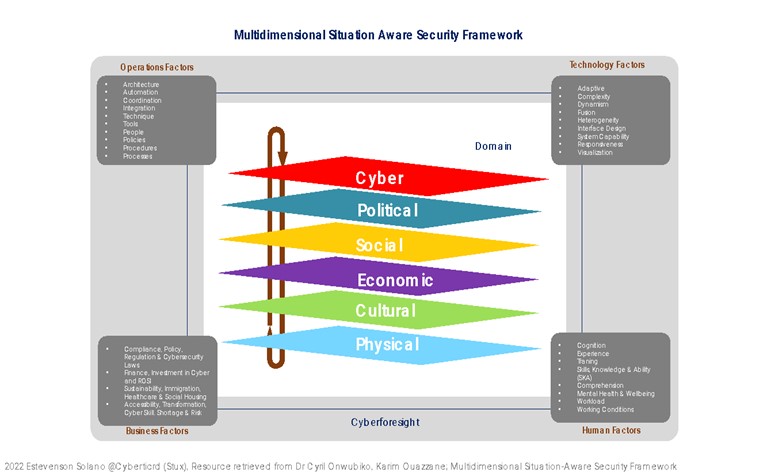
The human factors in Cybersecurity refer to the situations when the human error results in a successful data or security breach; they are the weakest component for the security of any ICT infrastructure and imply the greatest risks and threats for a company or organization.
New Markets’ team at Telefónica Tech Cyber Security & Cloud has developed a report aimed at fighting disinformation and raising awareness.
In terms of cybersecurity, spreading these concepts and highlighting common mistakes and good practices can help keep families and businesses more protected daily.
Some key figures to know the extent of cyber threats
- Human error is the leading cause of cybersecurity breaches. In 2021, found to be responsible for 95% of these breaches according to the “IBM Cyber Security Intelligence Index Report”. This means that, if the human factors were mitigated, only 1 out of 20 security breaches would take place.
- This human error is usually caused by the misinformation of users and workers. People can endanger their company and their personal data because of a lack of awareness. In a company, this can lead to a large breach or security incident with an economic impact of millions of dollars. In the day-to-day, it can mean the theft of credit cards or compromise of users’ personal files and data.
During this time of the pandemic, cybercriminals have adapted to take advantage of this issue and launch massive attacks related to Covid-19.
- A study conducted by Interpol showed that, during the first four-month period of 2021 (January to April), cyberattacks increased greatly: 907,000 spam messages, 737 incidents related to the malware and, 48,000 malicious URLs.
- According to feedback from Interpol, 59% of the main Covid-19 related cyber threats involved phishing, scam and fraud; 36% of attacks included malware; 22% contained malicious domains; and 14% involved fake news. These figures are alarming: a phishing attack costs large companies nearly $15 million a year on average. The cost of phishing in 2021 is more than three times its cost in 2015 (Ponemon Cost of Phishing Study, 2021).
Cyber attackers are taking advantage of lockdowns, working from home, and online studies to steal information by posing as companies, public entities, and universities. Cybercriminals know how to take advantage by attacking the lowest hanging fruit.
But… who poses a threat and why do they do it?
It is very important to know the attacker to protect yourself effectively. The motive behind these crimes is not the same for all types of attackers: money, information, theft, elimination of competition, or having fun, are among the most frequent reasons.
This report includes a list of the most common adversaries, including cybercriminals, hackers, hacktivists, organized crime, etc, and their reasons for posing threats.
Key concepts we all should learn to avoid attacks
It is also crucial to fight disinformation to learn which are the most common attacks, the characteristics found throughout them that can help not to be deceived and, the best ways to recognize each one.
Data Exposure & Common Mistakes
Cybercriminals use user information to select their victims. They obtain such valuable information on the Internet through Digital footprint and social media. It is the responsibility of users to be aware of the information they publish and to be aware of the most common cybersecurity mistakes that users continue to make.
Good Practices & Recommendations
But it is not only necessary to know the cybersecurity risks, attacks and mistakes already mentioned, there are best Cybersecurity practices designed to help you prevent fraud and scams and surf the internet as safely as possible that should always be considered.
Cybersecurity awareness training, keeping software updated and, keeping good practices in mind are still the best solutions against misinformation.
🔵 Read the full report to keep your organization and yourself cyber safe: Download here