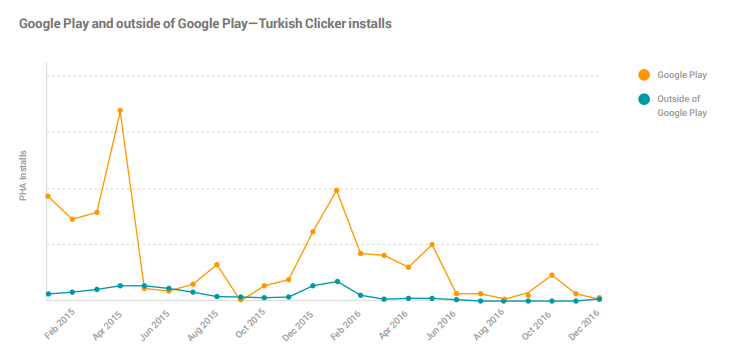
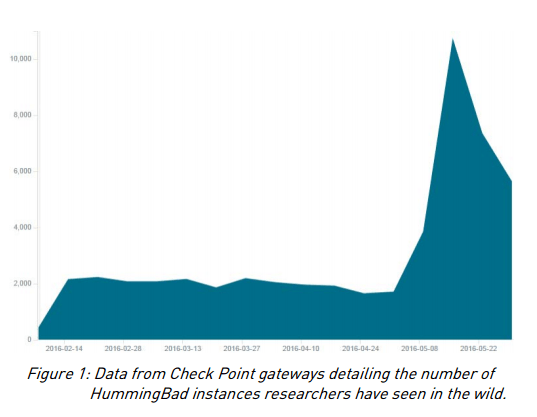
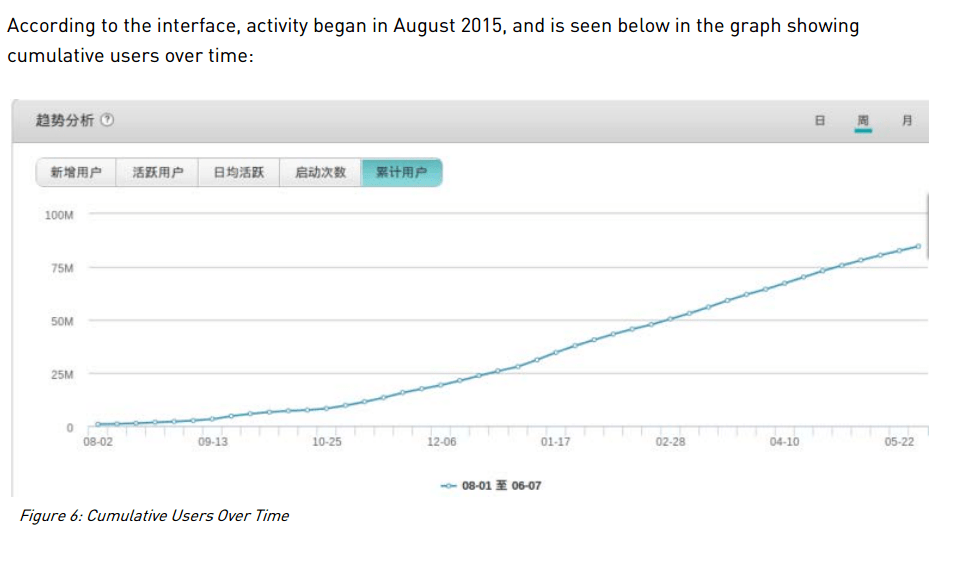
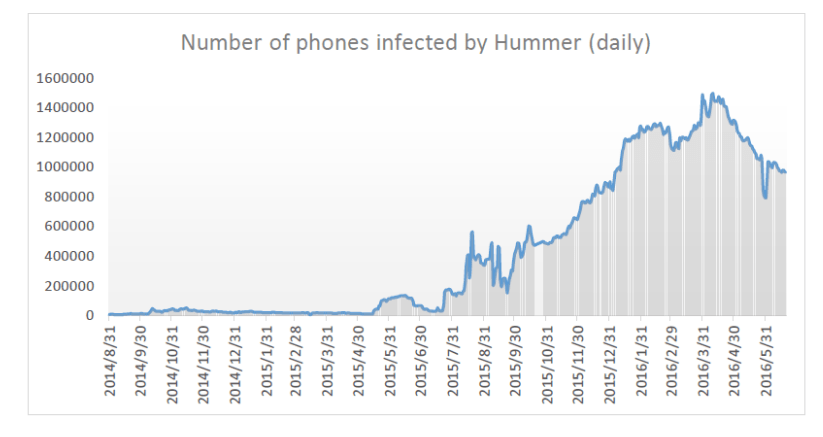
|
| Figure 1: Las Fallas de Valencia attract more than one million people each year. |
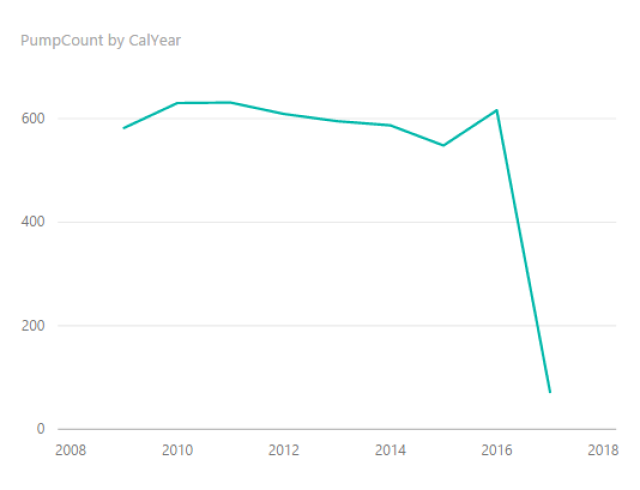
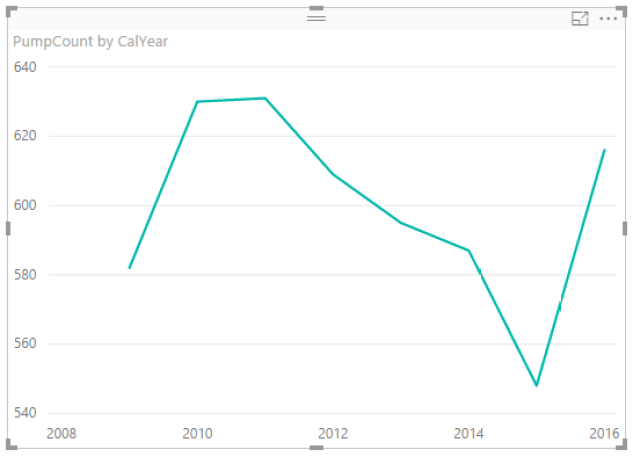
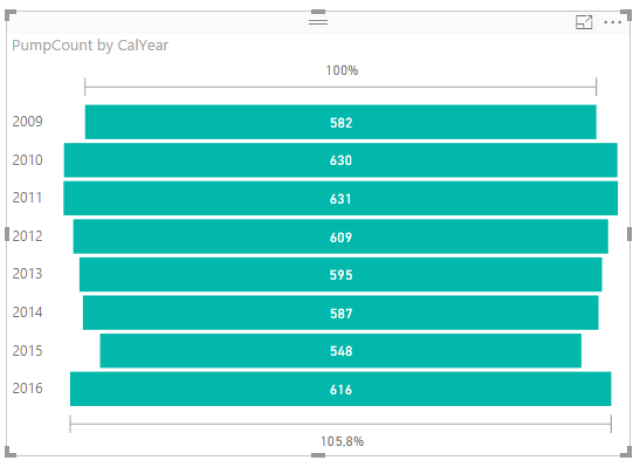
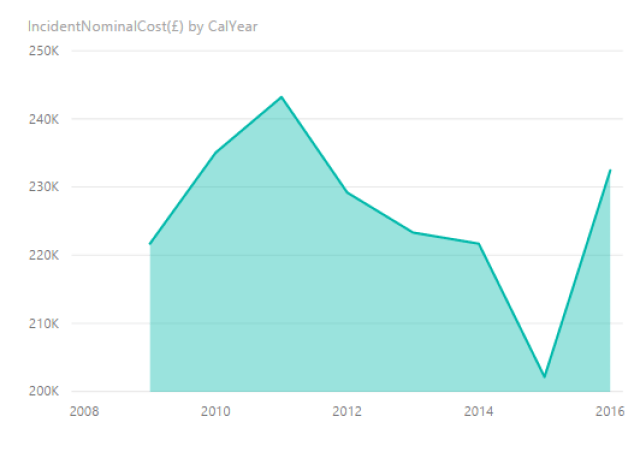
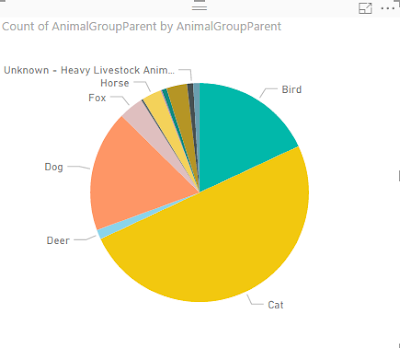
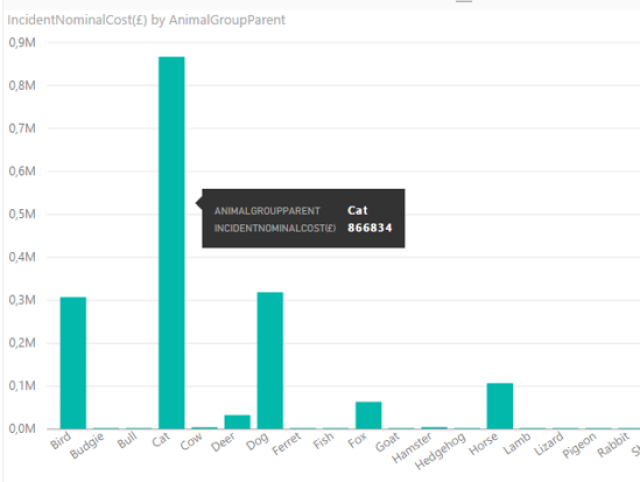
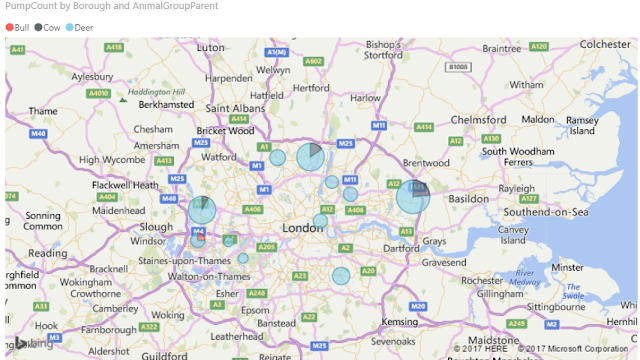
Like the two years we analyzed, the 2016 festival was also a definitive success. The festival welcomed over one and a half million people with a spending of 500 million euros.