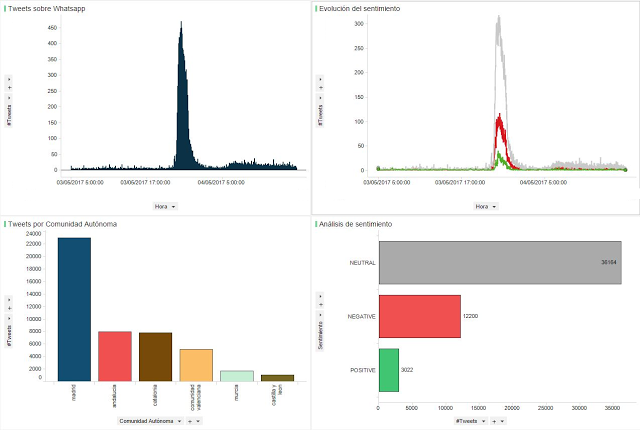
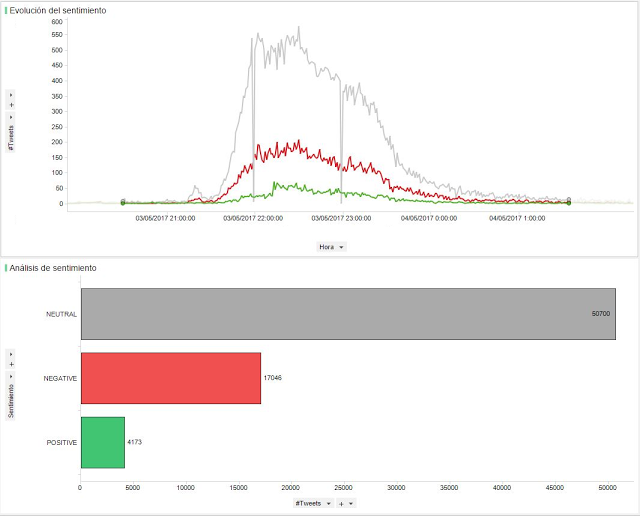
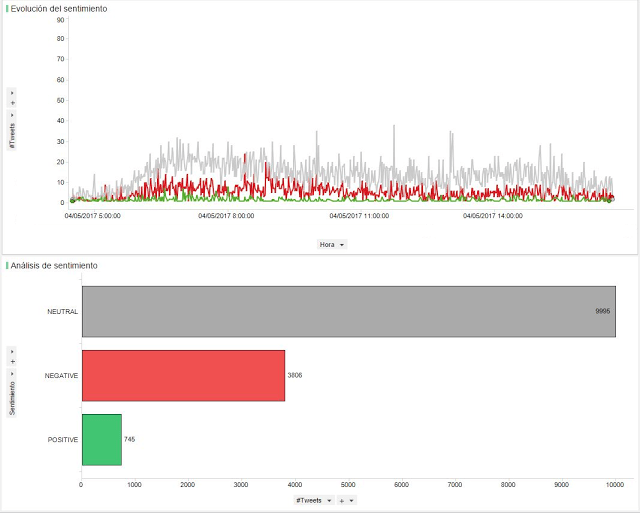
Recent years have seen a large public debate surrounding the technology behind Big Data and how it can help optimise organizations, maximise profits and bring companies closer to their consumers. However, data can also be leveraged to develop a social element that can use the large amount of information for a societal benefit. We recently hosted the first Big Data for Social Good in Action event with the aim of bringing together the people who wanted to transform Big Data for Social from “storytelling” to “storydoing”.
Elena Gil (LUCA CEO) started the event explaining the concept of Big Data for Social Good and the potential societal impact it can have. She highlighted three situations in which data was used to help with emergency calls in Colombia and how through further work with LUCA, data scientist measures for future natural disasters could be developed. She also encouraged all attendees to take part in projects that could have a global impact.
Continuing on from her introduction, Elena was then joined on stage by Trinidad Jimenez ( Global Director of PR at Telefonica), Javier Carro (Data Scientist at LUCA) and Alberto Asuero (CTO at Geographica). Together, they discussed the importance of open data, the future power of Big Data for societal purposes and the evolution of this technology, amongst other topics.
 |
| Figure 1: Debate in full swing at the #BD4SG event |
Following the discussion panel, we had the privilege of hosting different specialists from various sectors presenting real cases of the application of Big Data for Social Good. The director of digital communication at UNICEF, Nelson Leoni, presented an investigation carried out by the organisation analyzing the impact of Zika on the Brazilian population using mobile data.
David González (CTO and founder of Vizzuality) presented his Global Forest Watch project. It involves a web application with open code that allows the global monitoring of forests in almost real time. This data surrounding the change in volume of forests allows people to monitor the global rates of deforestation and detect illegal activity.
 |
| Figure 2: Elena Gil presented a general overview to the Big Data 4 Social Good attendees |
The last case study was presented by Juan Murillo (Urban Data Services & Applications BBVA). Juan talked about the impact of Hurricane Odile on the population of the peninsula of Baja California. Using a model that measured the activity registered to credit cards used by the citizens throughout the natural disaster, they could measure the economic impact on different segments of the population.
 |
| Figure 3: Some highlights from the event. |