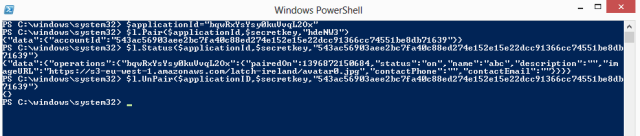
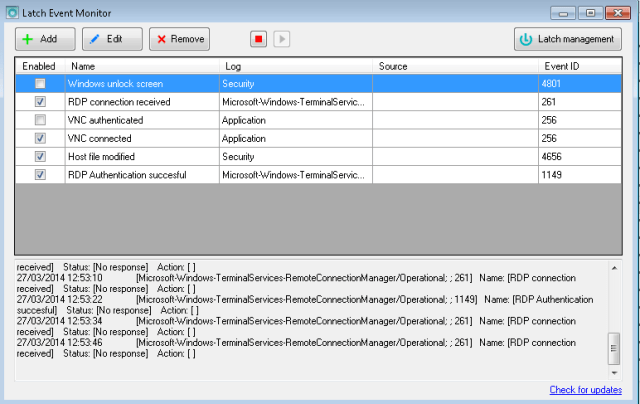
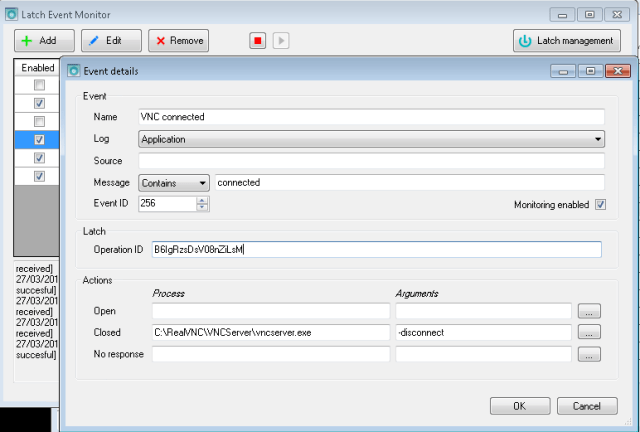
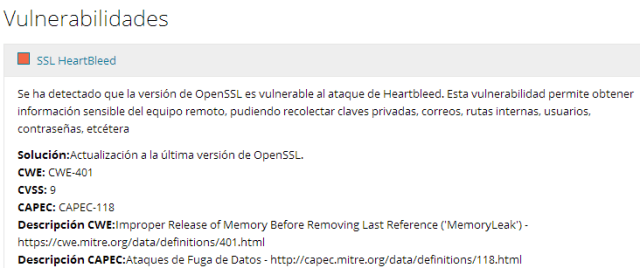
Although media talked about 66% of affected sites, actually that is the figure corresponding to Apache and nginx market. Not all of them will use OpenSSL and, not all of them using it would be vulnerable. The problem has already been fixed in our Latch servers. By the way, we have renewed our certificates for the API connection. If you as a costumers were doing a certificate check on your side, you must update it with the new ones released yesterday
There are lots of scripts with proof of concepts that allow to, with just a click, attack vulnerable servers and, as a collateral effect, its users.
 |
|
|
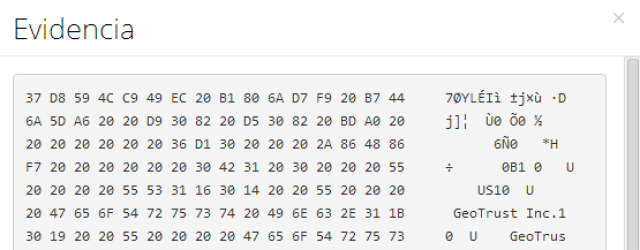
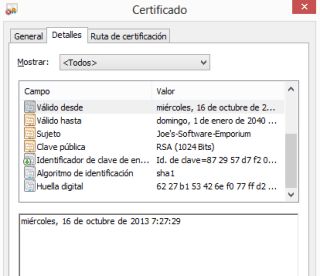
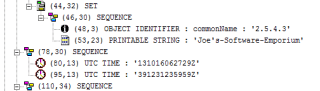
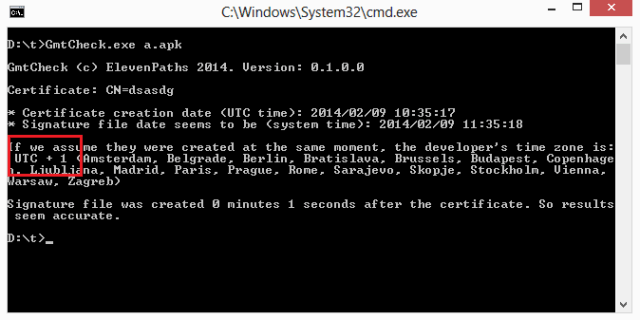
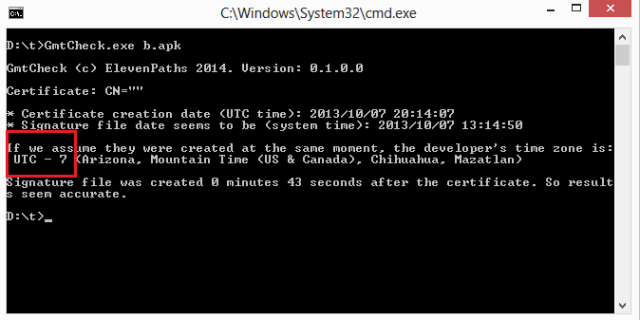
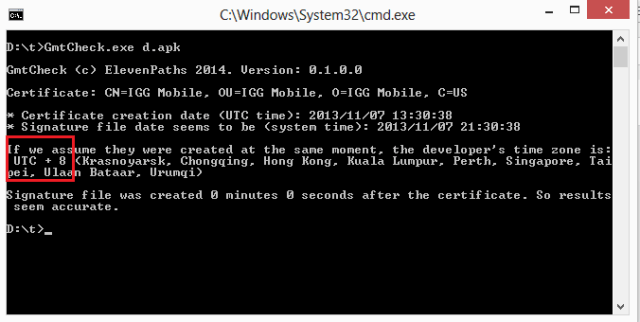
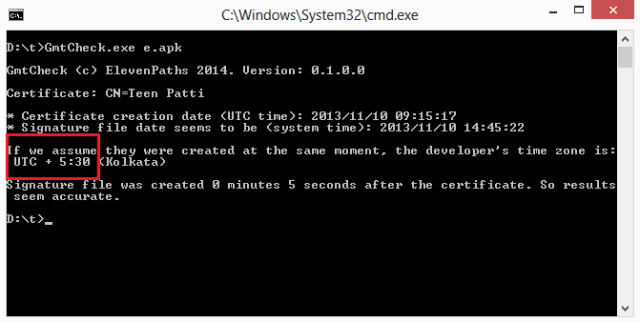
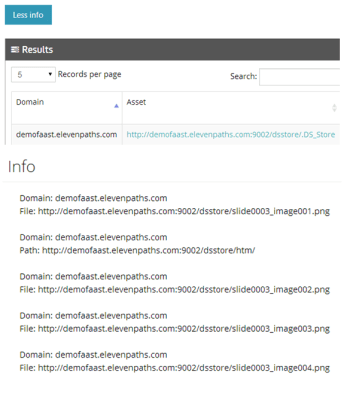
Faast features includes a way to show, as a picture, the evidence of a vulnerability exploited in a target. The evidence is shown both in the scanning report (in PDF) and the web interface.