A few weeks ago, Manuel Fernández, developer and security auditor in Eleven Paths, found some DS_Store files served by some Google URLs while testing FaasT. Google awarded the discovery with a mention in its Hall of Fame. We have found as well some files with certain sensitive information in Yahoo! servers, but they never answered our call. What did we find exactly? and, was it important?
We already know that when a company or pentesting team is running a pentest, all details available are important. The way they put them all together makes the different between a test with a big success and a moderate one.
During our tests with FaasT (to check if it could find something else in very exposed web pages like google.com, Yahoo!, apple.com…) we found some interesting data.
 |
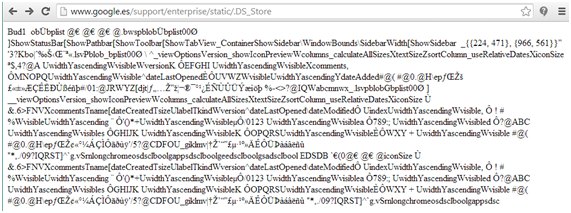
| Google.es with DS_Store available on their servers |
Thanks to FaasT, we found lots of .DS_Store files inside the search engine server. A DS_Store file may have internal paths inside, from the system of the user manipulating the web, dates, and new URLs that may be helpful for going further with the pentest.
FaasT identifies this kind of mistakes and shows them in detail inside its web interface. Persistent pentesting will allow to detect, between many other things, this configuration mistakes that implies lowering security level, feedback for the pentest, and open new ways… so adding up all this details empowers and completes the test.
When this leakage was detected in Google, we tried the DS_Store plugin in FaasT against the URL where they were detected, and we got an interesting list of new resources from them. In the figure below, there is an example as how FaasT shows elements found inside a .DS_Store file exposed in an URL. In this case, applied to our domain demofaast.elevenpaths.com and where new paths to PNG files can be found inside .DS_Store file.
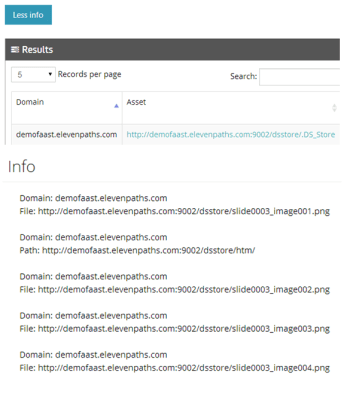 |
| Example of how internal information inside in a DS_store file is shown with FaasT interface |
When analyzing Google .DS_Store files, we got the following information:
- More than 40 new paths, storing data about Google GSA (Google Search Appliance) where the infrastructure, API documentation, or configuration was detailed.
- More than 30 new PDF documents, not all of them publicly available.
- Some other .DS_Store files.
- Some other HTML resources.
Once Google was informed, the files were quickly removed and placed us in its Hall of Fame as a recognition for the little help improving their security.
Yahoo! case
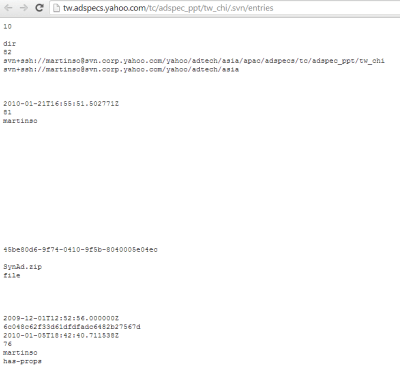
This case is much more simple. We found some SVN files with very interesting information in them, inside a domain related with ads in Yahoo!. This is a snapshot with what we found in different paths inside the domain.
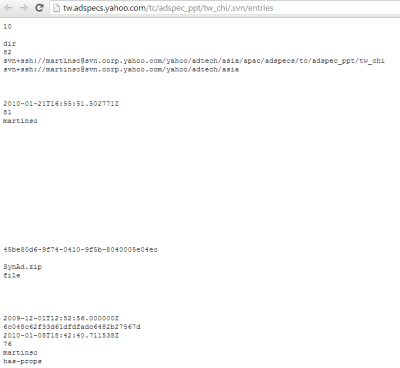 |
| Sensitive information in tw.adspecs.yahoo.com |
 |
| More sensitive information in tw.adspecs.yahoo.com |
Fundamentally, there were two URLs.
* http://tw.adspecs.yahoo.com/tc/adspec_ppt/tw_chi/.svn/entries
* http://tw.adspecs.yahoo.com/tc/adspec_ppt/.svn/entries
* http://tw.adspecs.yahoo.com/tc/adspec_ppt/.svn/entries
Where you could find links to some files, like http://tw.adspecs.yahoo.com/tc/adspec_ppt/tw_chi/SynAd.zip
From the text files themselves, following information was available (maybe obsolete, but interesting in any case for a pentest):
- ssh user for svn.corp.yahoo.com (martinso)
- svn user: (martinso)
- an internal domain: svn.corp.yahoo.com
- internal path: /yahoo/adtech/asia/apac/adspecs/tc/adspec_ppt/tw_chi
May days later after notifying Yahoo!, they removed the content. We never had an answer from them.
Pablo González