 |
| Different SDKs and plugins developed so far |
The best way to deal with this is to create a Powershell module that will export some functions. Creating a module is easy. Just use your editor of choice and write down the functions you need. You will need a Latch account, remember this is just as easy as:
- Register for free here to get a Latch account in a couple of minutes. Register as a developer.
- Create your account so you get your Secret and AppId.
- Download the app for your smartphone: It is available for Android, iOS, Windows Phone and Firefox OS.
Coding
We will create some funcions so we can interact with the official API. First of all, the constants:
Set-Variable API_HOST -option Constant -value "https://latch.elevenpaths.com";
Set-Variable API_CHECK_STATUS_URL -option Constant -value "/api/0.6/status";
Set-Variable API_PAIR_URL -option Constant -value "/api/0.6/pair";
Set-Variable API_UNPAIR_URL -option Constant -value "/api/0.6/unpair";
This will be the code function for the other ones. It will get an URL, the AppId and the Secret. Will return the result (code is simplified):
function AuthenticationHeaders{
param(
[string] $url,
[string] $applicationId,
[string] $secretkey
)
$requestSignature="GET`n"
$date = Get-Date -format u
$date = $date.Substring(0,$date.Length-1)
$requestSignature+=$date+"`n`n"+$url
$sha = new-object System.Security.Cryptography.HMACSHA1
$sha.Key = [Text.Encoding]::ASCII.GetBytes($secretkey)
$seedBytes = [Text.Encoding]::ASCII.GetBytes($requestSignature)
$digest = $sha.ComputeHash($seedBytes)
$base64Encoded = [Convert]::Tobase64String($digest)
$wc = New-Object system.net.webclient
$wc.Headers.Add("Authorization","11PATHS " + "$($applicationId) $($base64Encoded)")
$wc.Headers.Add("X-11Paths-Date", $date)
Try
{
$result = $wc.DownloadString($API_HOST+$url)
}
Catch
{
$ErrorMessage = $_.Exception.Message
$FailedItem = $_.Exception.ItemName
Break
}
return $result
}
Now you have the basics, the functionality is easier to achieve. For example, pairing an account would be just this:
function Pair{
param(
$applicationId,
$secretkey,
$pairingCode
)
$url = "$($API_PAIR_URL)/$($pairingCode)"
$result = AuthenticationHeaders $url $applicationId $secretkey
return $result
}
That will just basically call AuthenticationHeaders with the right parameters.
To check the status of the account (one of the most important features) just use this, using again the main AuthenticationHeaders function.
function Status{
param(
$applicationId,
$secretkey,
$accountID
)
$url = "$($API_CHECK_STATUS_URL)/$($accountID)"
$result = AuthenticationHeaders $url $applicationId $secretkey
return $result
}
For unpairing:
function UnPair{
param(
$applicationId,
$secretkey,
$accountID
)
$url = "$($API_UNPAIR_URL)/$($accountID)"
$result = AuthenticationHeaders $url $applicationId $secretkey
return $result
}
How to use it
There is much more to do and functions to implement, that are left as an exercise to the reader. To use this code, insert a line in the module with the functions you want to export, like:
Export-ModuleMember -Function Pair,UnPair,Status
Now, you can install this module, (just copying it to %UserProfile%DocumentsWindowsPowerShellModules, for example) and use it like this,. If you named it Latch.ps1, it would be, for example:
$l = import-module Latch -ascustomobject
$applicationId="bqwRxYXXXXXXX"
$secretkey="6O6zi6PDPnLzfVZcXXXXXXXXXXXXXXX"
$accountID="543ac56903aee2bc7fa40c88ed274e1XXXXXXXXXXXXXXX"
$l.Pair($applicationId,$secretkey,$args[0])
$l.Status($applicationId,$secretkey,$accountID)
$l.UnPair($applicationId,$secretkey,$accountID)
This commands will return a JSON you can parse, just like the specifications in https://latch.elevenpaths.com suggest.
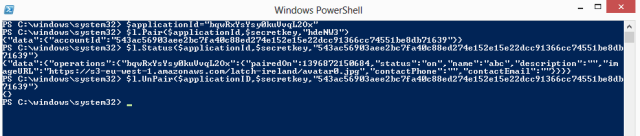 |
| An example of using this scripts for pairing, getting the status and unparing |
For another approach to this problem, the SDK for powershell may be used, that will be available soon.






thks