Prerequisites
Admins have to follow the usual steps if they want to protect SugarCRM with Latch:
- Create a developer account if they haven´t it.
- Create an application with the features they want.
- Download the plugin.
- Install and configure the plugin in their SugarCRM environment.
Steps 1, 2 and 3 are documented on the website of Eleven Paths, step 4 is going to explained in this post.
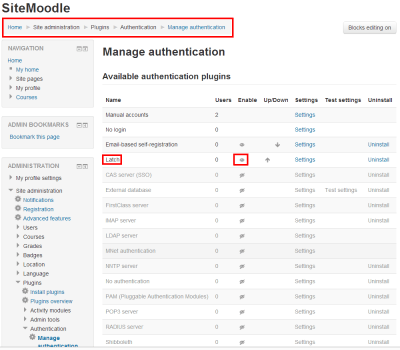
Go to the “Admin” panel in SugarCRM.
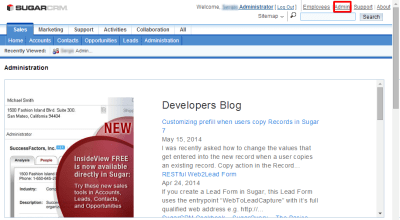 |
| SugarCRM Admin Panel |
Go to module loader using the “Module Loader” link, in the “Developer Tools” section.
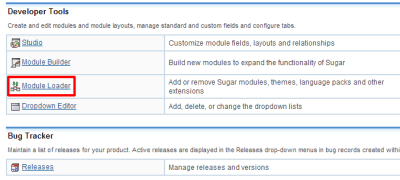 |
| “Module Loader” in SugarCRM |
In this section add the downloaded zip file, upload and install it.
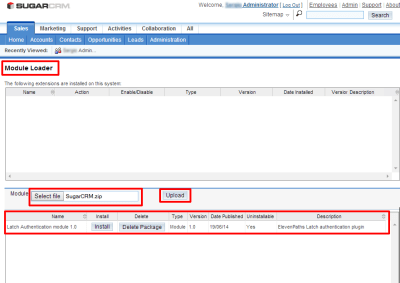 |
| Add the downloaded module to SugarCRM |
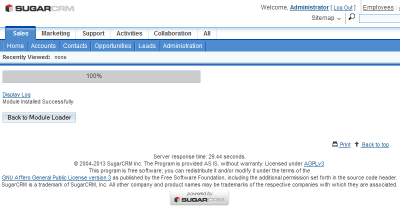 |
| Module installation |
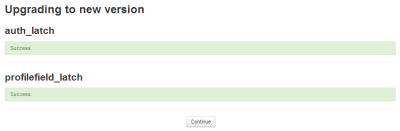
Next, rebuild SugarCRM template. Return to the “Admin” panel and click on the “Repair” link, and then on “Quick Repair and Rebuild”.
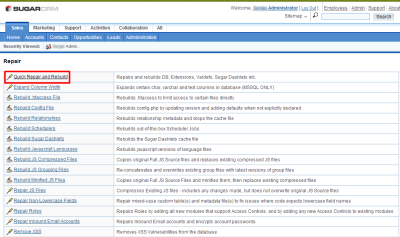 |
| Rebuild the templates |
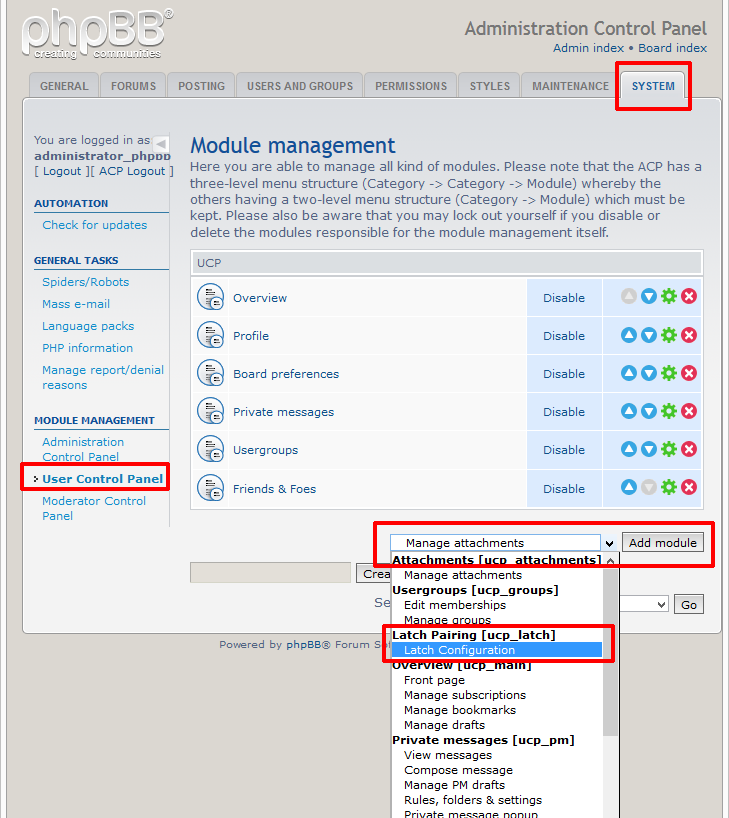
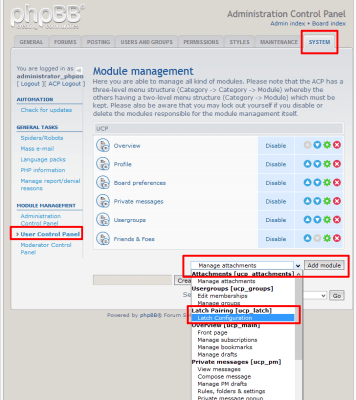
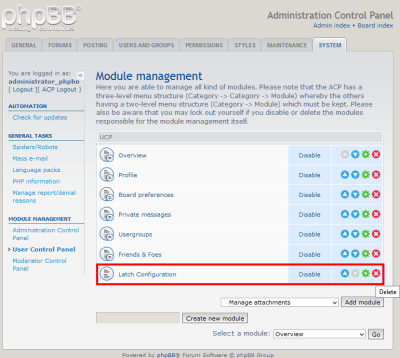
Once the process is completed, SugarCRM will rebuild the application and Latch module can now be set up. A “Latch Configuration” link will appear in the “Admin” panel.
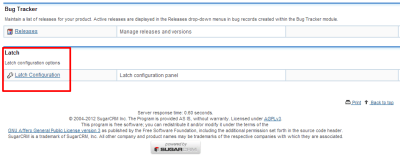 |
| Accessing Latch module setup menu |
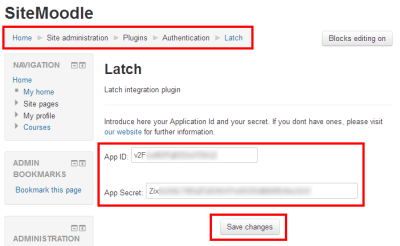
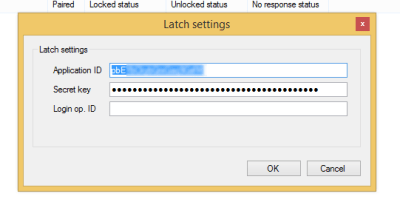
Here the administrator has to add the Application ID and the Application Secret.
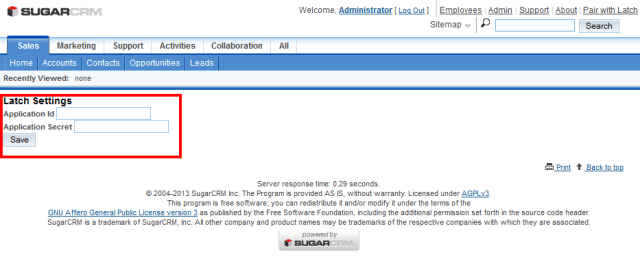 |
| Application ID an Application secret form |
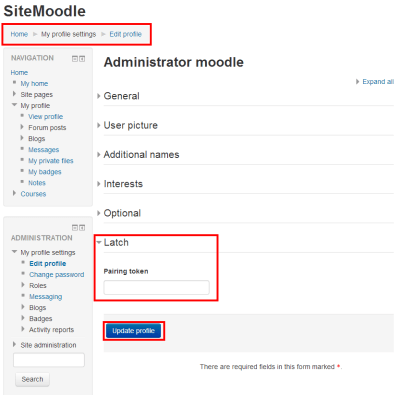
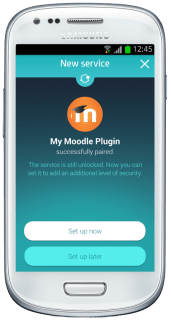
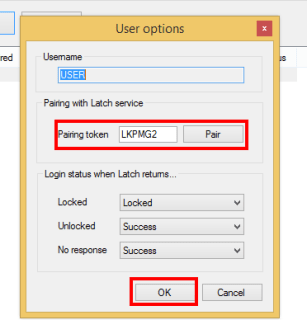
Latch is now ready to be used and users are ready to pair their accounts. Users with SugarCRM accounts have to set their own accounts going to “Pair with Latch” and typing the characters generated with the phone into the text box displayed on the web. Once the token generated by Latch is introduced into their accounts, a notification will be received on the phone, announcing that the account is already paired.
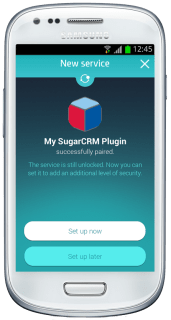 |
| SugarCRM successfully paired |
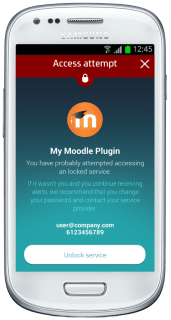
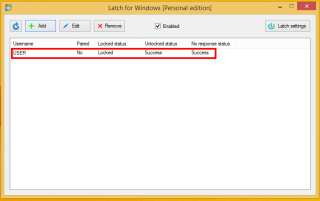
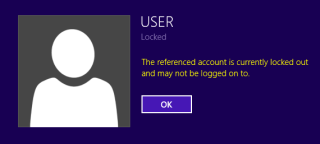
Now the user may lock and unlock access to his SugarCRM account and a notification on his phone will be received, warning about anyone trying to access the account.
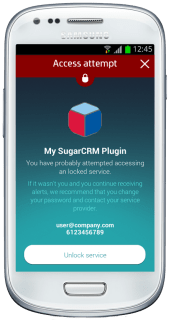 |
| Notification of an unauthorized access attempt |
The database
When the plugin is installed in SugarCRM, SugarCRM database is set to store the values needed by Latch.
The latch_accounts table indicates which user account has been paired with Latch, and the account id user.
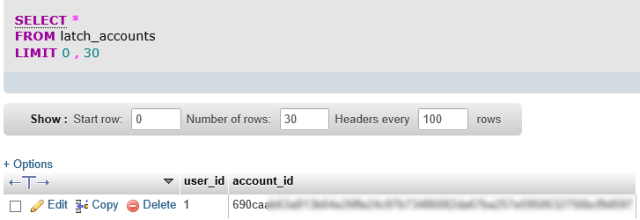 |
| Table latch_accounts with the users that have already paired their accounts |