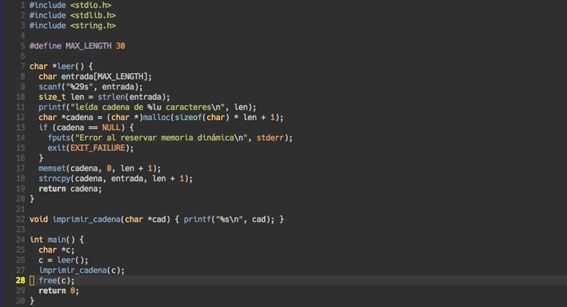
Our brain is amazing and has evolved over thousands of years to make our lives simpler or to minimize processing time on things it considers unnecessary. One of them would be reading each letter in a written text. This can be checked by several ways, as in the following example:
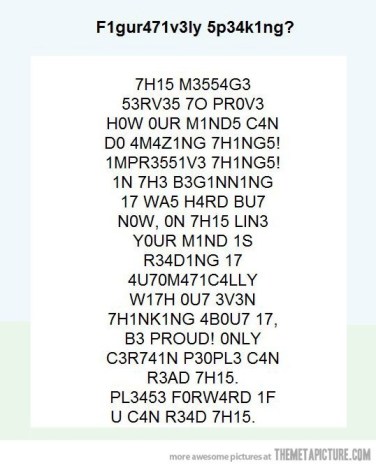
Why Does That Happen?
This is due to the way we learn to read, since initially we only see images and it is not until after we understand them that we begin to associate sounds with words. Once we are used to reading the same words for a long time, our brain places words where they are not, or immediately replaces the numbers with their corresponding letters, or can read text when it is written backwards, among many other things.
Without a doubt, this brain capacity is incredibly powerful, but it also poses some cybersecurity risks because of the possibility it offers to easily generate deception. For example, if you get a message saying “www.gooogle.com” you don’t realise that “gooogle” has three “o” instead of the two that the actual website has.
What TypoSquatting Is
For many years now, criminals have realised that it is possible to use this capacity against us. Phishing campaigns use these small text alterations to trick users, and they are very effective if they are associated with feelings of fear or financial distress. This type of threat has been called TypoSquatting.
Due to the current health crisis caused by the Covid-19, this technique is being increasingly used. One of the institutions that has been most targeted by these hoaxes is the World Health Organization, which had to publish a cybersecurity communication intended to mitigate the damages of these hoaxes.
One of the thousands of examples can be found in one of the existing pandemic tracking systems, called coronatracker.com. This is used as the basis for different typosquatting-type mutations, as we can see below:

To summarise the analysis, only the second domain detected will be taken: coronatracker.info. This domain uses the technique of changing the root domain (from com to info) so that the victim, when focusing on the webpage name, does not notice any other details. In the following example below, an SMS tries to trick the user by using the domain of a bank, changing the root domain from com to one.

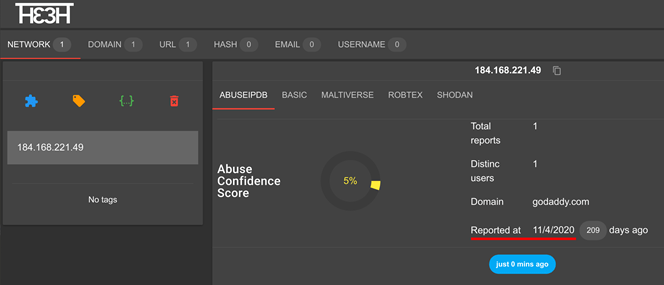
When performing the analysis of coronatracker.info by using our TheTHE tool, it can be seen how this TypoSquatting hoax hides a dedicated phishing site and that the domain was created during the first week of the pandemic, like thousands of others that have emerged. When using the IP, we see in the first image that it has already been reported in AbuseIP for being a suspicious IP. In the second, we see how the analysis with Maltiverse detects it as malicious.

Using the domain, it can be seen that this has already been reported in VirusTotal and responds to 9 different IP addresses.

As you can see, criminals do not miss any opportunities to spread malware. This storm of events triggered by the pandemic is the perfect time to use all the mechanisms at their disposal to access personal, data and financial data, or simply to access machines to reach more victims.
These techniques are not only applied in domains, but also in mobile applications, development software packages, e-mails, instant messaging, SMS and any other means that may be used to make victims click on the link.