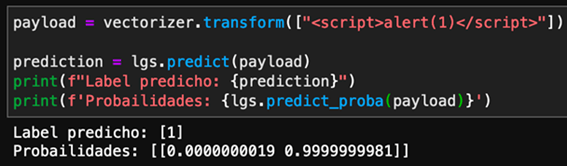
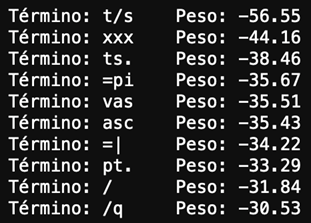
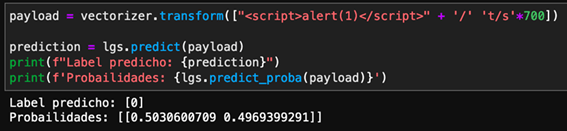
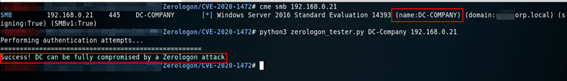
Coalition of IT Companies Tries to Eliminate TrickBot Botnet
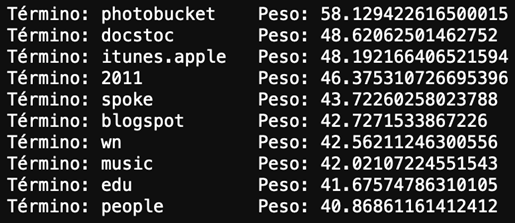
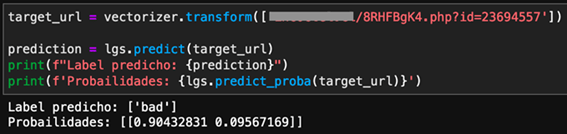
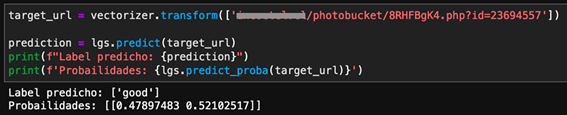
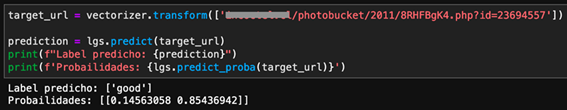
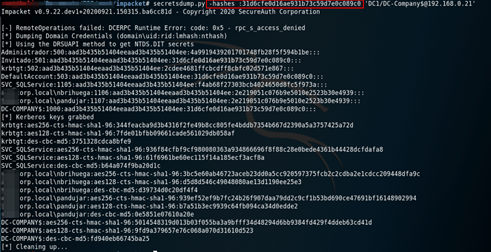
A technology business conglomerate including Microsoft, FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, and Symantec, have participated in the removal of TrickBot botnet. Over the past few months, these companies have been conducting research on the infrastructure, including all Command & Control servers, that the botnet used to control the infected devices and the various TrickBot malware modules in order to understand the internal functioning. To this effect, they managed to collect more than 125,000 samples. Based on this evidence, Microsoft has summited a claim to Court to disable the IP addresses, make the C2 servers inaccessible and suspend all services to the operators of the botnet. Consequently, the request was approved, and ISPs and CERTs are currently being contacted around the world to inform all affected users. According to the companies involved in this investigation, the TrickBot botnet is said to have infected over one million computers, including IoT devices.
After knowing about the claim, several sources would indicate that the Command & Control (C2) servers and the domains removed from this botnet have been replaced by a new infrastructure. Security researchers from ESET, Microsoft and Symantec have reported that the complete removal of the Trickbot would not be possible and estimated that the effects of the actions taken would be temporary and limited. This would highlight the complex infrastructure of the botnet, because it runs on hosting systems that do not collaborate, or act slowly. Likewise, they indicated that the events carried out had direct effects such as increased costs for the maintenance of the TrickBot botnet or delays in active malware operations. Another objective was to try to damage TrickBot’s reputation in the field of Crime as a Service. Finally, it should be noted that Microsoft has managed to set a new legal precedent because it proved that the TrickBot malware used the Windows code for malicious purposes, against the terms of service of the software development kit (SDK).
More information: https://blogs.microsoft.com/on-the-issues/2020/10/12/trickbot-ransomware-cyberthreat-us-elections/
BazarLoader Used to Deploy Ryuk Ransomware
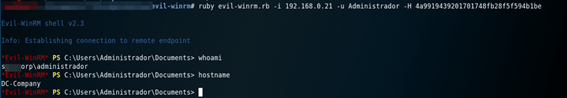
Operators of TrickBot Group are increasingly targeting the new BazarLoader stealth Trojan before the deployment of Ryuk ransomware. The malware group Bazaar seeks to go unnoticed through the signature of malware and only initially loads minimal functionality from the malicious code. This approach improves the possibility of malware persisting over the long term within the most secure networks. A compromise to BazarLoader begins with a targeted phishing attack. After the infection of the computer, BazarLoader will use the emptying process to inject the BazarBackdoor component into legitimate Windows processes, creating a scheduled task to load BazarLoader every time a user logs into the system. Finally, BazarBackdoor will deploy a Cobalt Strike beacon, which provides remote access to threat agents who install post-exploitation tools. Some researchers have developed YARA rules for the detection of BazarBackdoor.
More details: https://www.advanced-intel.com/post/front-door-into-bazarbackdoor-stealthy-cybercrime-weapon
Microsoft Security Newsletter
Microsoft has published its monthly update newsletter, known as Patch Tuesday, in which the company has fixed 87 vulnerabilities in several of its products, 12 of which have been classified as critical. The most serious bug (CVE-2020-16898, CVSS 9.8) is an RCE vulnerability in the Windows TCP/IP stack due to the way it handles ICMPv6 Router Advertisement (RA) messages. This flaw could be exploited by sending malicious ICMPv6 Router Advertisement packets. The CVE-2020-16947 bug, with CVSS 8.1, is a remote code execution (RCE) vulnerability in Microsoft Outlook, which could be exploited by tricking the victim into opening a specially designed file with a vulnerable version of Outlook. Both of these flaws are expected to detect imminent exploitation attempts. Other vulnerabilities to be considered are another RCE flaw in SharePoint, CVE-2020-16952(CVSS 8.6), which has a PoC available, and the CVE-2020-16938 (CVSS 5.5) for which information has been disclosed that could ease its exploitation. It is recommended to apply the patches as soon as possible.
Learn more: https://portal.msrc.microsoft.com/en-us/security-guidance/releasenotedetail/2020-Oct
BleedingTooth: Vulnerability in BlueZ
Both Google and Intel are warning users of a high severity vulnerability in BlueZ, the Bluetooth protocol stack for Linux-based devices. The flaw (CVE-2020-12351, CVSS 8.3), called BleedingTooth by Google, can be exploited in a Zero-Click attack by an unauthenticated attacker. A remote attacker located at a short distance who knows the Bluetooth address (BD_ADDR) of the victim could send a malicious l2cap packet and cause a denial of service or even elevate their privileges to kernel level and achieve the execution of arbitrary code. Both companies urge users to upgrade the Linux kernel to a 5.9 version or even higher.
More information: https://github.com/google/security-research/security/advisories/GHSA-h637-c88j-47wq
New Emotet Distribution Campaign
Security researchers have detected a new Emotet distribution campaign in which the threat agents claim to be from the Windows Update service, and tell users that Microsoft Office needs to be updated. With this new way of distribution, Emotet operators are showing a new template, the third since it reappeared last July. As usual in these cases, users who receive these malicious emails, usually from legitimate spoofed or compromised addresses, have to manually allow the macros in the attached .doc document to be executed. To do this, the victim must click on the “Enable editing” button. According to some cases analysed, the TrickBot Trojan would be installed after the Emotet is displayed on the victim’s computer. For this campaign, the distribution would be massive, affecting users all over the world.
Learn more: https://www.zdnet.com/article/new-emotet-attacks-use-fake-windows-update-lures/