A few days ago, attention was focused on Reddit, within a community that is characterised by its conspiracy theories. According to the news it consisted of filtering 43 GBs of data from “Windows XP” but, according to the name of the Torrent (more accurate), what was filtered was “Microsoft leaked source code archive“, because it actually contained much more. This is a compilation of previous leaks, documents, documentaries, images… and yes, unpublished source code. More than half of the content is fact made up of all of Microsoft’s patents, up to 27 GB in compressed form. Let’s have a look at other curiosities
Directory and File Analysis
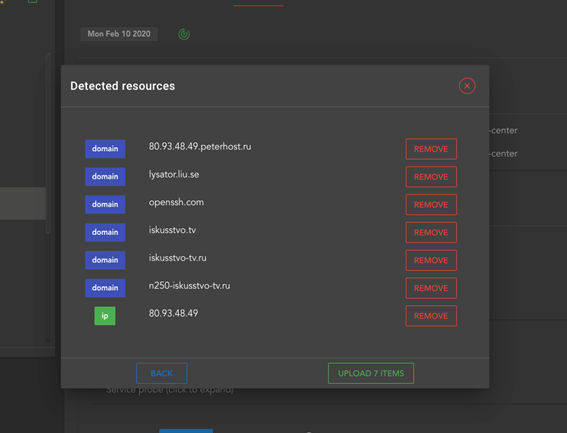
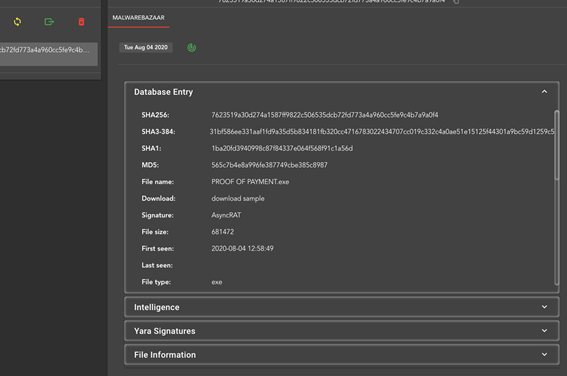
Here is an example of what it can be downloaded:

The description of Torrent itself makes this clear. Included in this Torrent are:
- MS-DOS 3.30 OEM Adaptation Kit (source code)
- MS-DOS 6.0 (source code)
- DDKs / WDKs stretching from Win 3.11 to Windows 7 (source code)
- Windows NT 3.5 (source code)
- Windows NT 4 (source code)
- Windows 2000 (source code)
- Windows XP SP1 (source code)
- Windows Server 2003 (build 3790) (source code) (file name is ‘nt5src.7z’)
- Windows CE 3.0 Platform Builder (source code)
- Windows CE 4.2 Shared Source (source code)
- Windows CE 5.0 Shared Source (source code)
- Windows CE 6.0 R3 Shared Source (source code)
- Windows Embedded Compact 7.0 Shared Source (source code)
- Windows Embedded Compact 2013 (CE 8.0) Shared Source (source code)
- Windows 10 Shared Source Kit (source code)
- Windows Research Kernel 1.2 (source code)
- Xbox Live (source code) (most recent copyright notice in the code says 2009)
- Xbox OS (source code) (both the “Barnabas” release from 2002, and the leak that happened in May 2020)
We have indicated the most relevant part in bold since, about the rest, much was already known from previous leaks. For example, in May 2020 the original Xbox and NT 3.5 code was leaked; in 2017, some parts of Windows 10; and in 2004, some parts of NT and 2000.
We show here the complete TXT justifying what the Torrent consists of.
The PDF section is nothing to be missed, mostly because of the value of gathering so much documentation and news about code disclosures.

A Mysterious Encrypted RAR
The leak contains an encrypted RAR (Windows_xp_source.rar), and the person including it appeals to the community to try to decrypt the password.
“Including ‘windows_xp_source.rar’ in this collection, even though it’s password protected. Maybe someone can crack (or guess) the password and see what’s inside. The archive is bigger than the other XP / Neptune source tree. It might be genuine, it might not. But I’m including it just in case, since the file was so hard to track down. Original upload date seems to have been around 2007 or 2008.
The hash key is: $RAR3$*0*c9292efa2e495f90*044d2e5042869449c10f890c1cced438”
¿Is This relevant?
What is important, therefore, and seems to be new, is the source code of kernel 5 from 2003 and largely shared by XP as well. Nt5src.7z, which is about 2.4 gigabytes and when decompressed reaches about 10 GB. It seems that the code is very complete, but it is not known if it contains enough to compile it. The vast majority of the files are dated 2 September 2002. The Service Pack was officially released on the 9th.
With respect to whether this leak is a security threat, it will help detect or analyse potential vulnerabilities that are still preserved in Windows 10 by inherited code much faster. Attackers will be able, once an opportunity for flaw has been identified, to better understand why it occurs if they go to the clear code portion. And not just the inherited parts in Windows 10. Windows XP and 2003 themselves are still found on a good number of important systems. Truth be told that since 2014, when their support was stopped, administrators have other problems added if they still maintain this system. But this can make it worse. Not much more, but it is important.
In any case, any researcher looking for vulnerabilities in the code would start from comments… where programmers reflect doubts, fears and… potential cracks. A simple search by “WARNING:” gives us some interesting idea of what things can go wrong in the code, according to the programmers themselves. Some of them will be mare curiosities and others could be seen as potential security problems. Here are some examples.
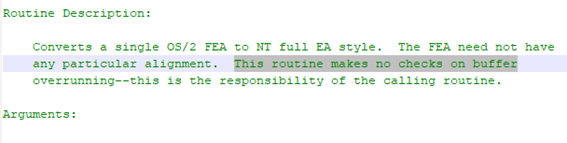
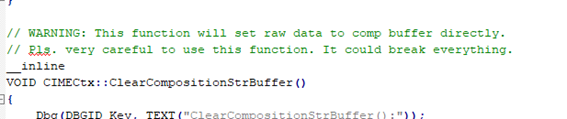
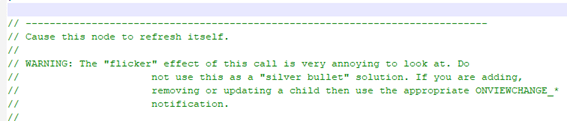
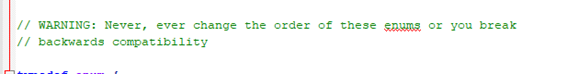
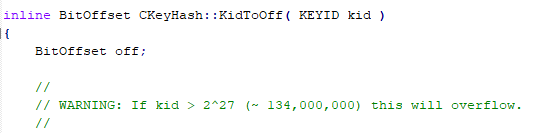
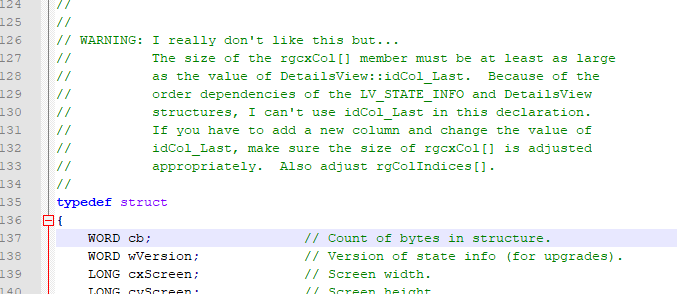
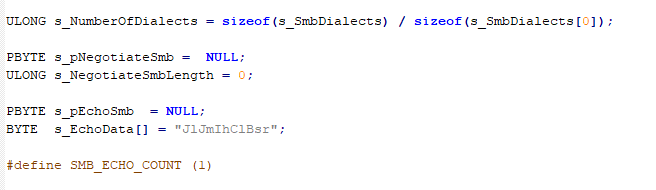
JlJmIhClBsr Chain
We didn’t want to forget that in the code related to the file sharing, there is the JlJmIhClBsr chain, something curious that can indicate that the NSA already had access to the Windows code (this would not be strange at all) but that also implied that it made a mistake when creating the exploit of EnternalBlue. Because by including that chain, which was in the source code, it is not very well known why, it was adding (without being aware of it) a kind of very relevant IDS signature to know if someone was being attacked by the EternalBlue exploit.
This is very curious because it would also imply that the NSA created the exploit by fixing or adapting the source code directly. When the exploit was made public, WannaCry, created under EternalBlue, also inherited that chain. However, it was useless and when it was ported to Metasploit it was simply removed. At the time, we already investigated and verified that in reality this chain JlJmIhClBsr would only have one use: to serve perfectly as a signature or mark to detect the network attack. A mislead from the NSA.