OWASP, the foundation focused on web application security, has recently updated its ranking of the most prominent risks. Let’s take a look at the new reorganisation of the top, commenting briefly on what aspects of security each of them touches on.
What is the “OWASP top 10”?
The OWASP top 10 is a fairly popular ranking in the world of web security and auditing, albeit nuanced and not without some controversy in the past. The list was first compiled in 2003 and updates have been published more or less regularly every three years since then.
Of course, the list is not representative of all risks in web applications. In fact, it is likely that some of the items on this list do not apply to certain types of applications, while other risks that are not on the list could critically affect them.
It should be taken as a “where the frontiers of the global risk map are moving”, rather than a detailed and particular blueprint of where the security emphasis should be placed.
The rankings are based on a study of a significant number of web applications and a survey of the industry, where practitioners indicate their greatest concerns about the various risks to their applications.
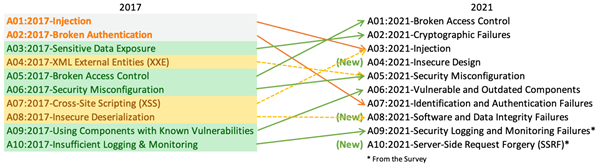
- In first place, we have a notable rise from fifth: A01:2021-Broken Access Control. This category covers all risks that allow an attacker to circumvent an imposed control in order to gain access to a resource. These types of vulnerabilities can emanate from the development itself to errors in the configuration during deployment. A simple example would be being able to access a privileged API because it does not correctly examine the access permissions of the source of the request.
2. The second place (climbing from third) goes to A02:2021-Cryptographic Failures. Cryptography is difficult, and if it is already complex to understand, it is even more difficult to apply its concepts in a practical and error-free manner. Add to this the fact that failures in cryptographic libraries are often cross-cutting. That is, a bug affects a myriad of libraries and programs that depend on them. Problems in the cryptographic chapter fill (rather flood) the audit reports: use of an obsolete hash function, insufficient encryption, insecure block cipher mode… and of course: absence of any kind of encryption…
3. The third place is a surprise, because after years of reigning at the top, injection vulnerabilities fall several notches. A03:2021-Injection groups together all those vulnerabilities in which the vector is the input of external code and is executed both on the client (browser) and on the server. In other words, both cross-site scripting and SQL injection. Undoubtedly, the progress made in terms of security, both in programming languages and in secure programming libraries and techniques, has something to do with this. It’s nothing to let our guard down, but it may be good news.
4. Fourth place goes to a new category, unheard of in the ranking: A04:2021-Insecure Design. However, it is an amalgam of possible flaws in the design and implementation of the logical controls that should ensure the correct functioning of the application. For example, allowing products in the shopping cart with a negative number of items, storing the credentials in clear text, etc. As we can see, it is a catch-all for all kinds of errors that put the security of the application at risk.
5. A05:2021-Security Misconfiguration moves up one place, from sixth to fifth. Although this category could be confused with the previous one, it is easy to see that it refers to aspects of security that need to be reviewed in the context of configuration rather than secure design and implementation. The clearest example would be allowing a web server to list entire directories or allowing traces of request execution errors to be published in response to a request. Typically, third-party products provide an open default configuration to create as few conflicts as possible. Adapting the configuration in a secure way should be part of the natural development and deployment cycle.
6. Sixth place belongs to A06:2021-Vulnerable and Outdated Components, which moves up from ninth. It is almost self-explanatory: that the application has vulnerable or outdated components and the most direct example would be a WordPress plugin that is outdated and vulnerable or abandoned by the developers. It is obvious that a system is not built and deployed and then forgotten about. Software has to be tended like a garden or the bugs will end up eating the fruits of the garden.
7. A07:2021-Identification and Authentication Failures was formerly known as Broken Authentication. It also features another major drop: from second to seventh place. Easily confused with access controls, identification and authentication is the first step in obtaining permissions and privileges at the application level. This category not only identifies risks at the point of authentication, but we are also capturing here the lifecycle of the user session. That is, aspects such as the robustness of the authentication token, the exposure of the token and its validity over time.
8. The eighth place is taken by a new category that covers certain risks that have been in many headlines: A08:2021-Software and Data Integrity Failures. This section takes care of everything related to the integrity and verification of sources when we install, update or have supporting infrastructure (continuous integration, …) Remember the “supply chain” attacks? Well, this new category is the result of recognising this type of attack as a critical and important threat that we cannot ignore. We must not only keep an eye on our domains but also on what we sit at our table.
9. A09:2021-Security Logging and Monitoring Failures moves up one place and updates its name. From Insufficient Logging & Monitoring to the current one, no wonder. An application generates an astronomical number of events. How many of these events are security alerts? And better yet, which of these are real and critical alerts? This chapter covers everything from the absence of event logging to the proper storage and management of events. There is no point in having done your homework in all other aspects and not knowing what is happening and not being able to act in time.
10. The ranking is closed by A10:2021-Server-Side Request Forgery as the industry’s number one concern (from the OWASP industry survey). It is practically the only category with a specific type of vulnerability. Not surprisingly, the vulnerability can pose a very high risk in a range of repercussions ranging from the discovery of exposed services on the internal network, access to non-public resources (files, databases, …) and even arbitrary code execution.
A new scenario for cybersecurity
This is the new scenario that OWASP paints in 2021. The changes are obvious, and although it is shown in an ordered list, we cannot weight the risk in relation to its position on the list. In fact, you only have to go through the security test guide to see how high the risks are.
The top is a tasting of what is the hottest or most important points, but we must not lose sight of the rest. Doing so can put us in an awkward position if we fail to give importance to chapters that do not fall into the ten categories listed.
Read more:
https://owasp.org/www-project-web-security-testing-guide/stable/