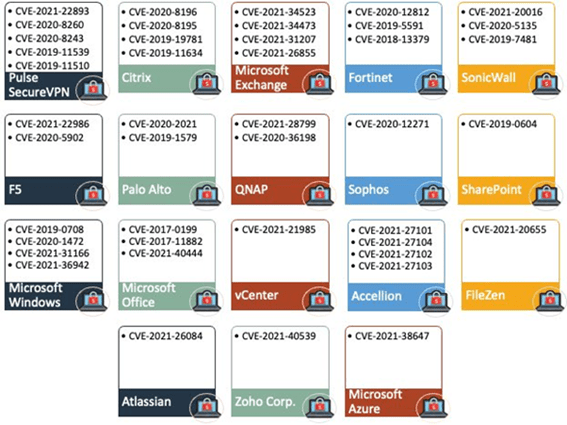
Zerodium interested in acquiring 0-days of Windows VPN software
Information security company Zerodium has reported its willingness to purchase 0-day vulnerabilities targeting VPN service software for Windows systems: ExpressVPN, NordVPN and Surfshark. The company has shown interest in exploits that could reveal users’ personal information, leak IPs or allow remote code execution. It is worth remembering that Zerodium is known for buying 0-days in different applications, which it then sells to law enforcement and government agencies, so the target of these new acquisitions is easily identifiable. However, this has generated some controversy, as reported by The Record, as many users use VPN apps to preserve their privacy in countries with oppressive regimes, and it is not known who Zerodium´s end customers are. So far, none of the VPN providers have commented on the matter.
More details: https://twitter.com/Zerodium/status/1450528730678444038
LightBasin: a threat to telecoms companies
Researchers at CrowdStrike have published a new analysis of the threat actor known as LightBasin or UNC1945, which has been targeting companies in the telecommunications sector since 2016. Linked to Chinese interests, LightBasin often targets Linux or Solaris systems in its operations, as they are highly related to its preferred sector. CrowdStrike has observed new Techniques, Tactics and Procedures (TTPs) associated with this group. For example, LightBasin would have taken advantage of external DNS servers (eDNS) to propagate its operations, or TinyShell, an open-source SGSN emulation software, to channel traffic from the C2 server. It is worth noting that eDNS is a fundamental part of the radio frequency networks (GPRS) used for roaming between different mobile operators. The researchers highlight the group’s extensive knowledge of networks and protocols, claiming that LightBasin would have compromised at least thirteen telecommunications companies in 2019 alone.
All details: https://www.crowdstrike.com/blog/an-analysis-of-lightbasin-telecommunications-attacks/
RedLine Stealer: main source of data from two Dark Web markets
Recorded Future’s cybersecurity research division, Inskirt Group, has published a report identifying the RedLine Stealer malware as the primary source of stolen credentials being traded on two Dark Web markets: Amigos Market and Russian Market. RedLine Stealer is an infostealer that has the ability to collect credentials from FTP clients, web browser logins, mail applications, as well as extract authentication cookies and card numbers stored in the browsers of infected devices. During the investigation, the Inskirt Group team detected the publication of identical listings on both marketplaces simultaneously, which contained the same information stolen from victims, far exceeding the contributions of other malware on both forums. In addition, it is worth noting that, although Redline Stealer was developed by the threat actor REDGlade, several versions, similar to the original, are currently being distributed and have led to its further spread.
More information: https://go.recordedfuture.com/hubfs/reports/mtp-2021-1014.pdf