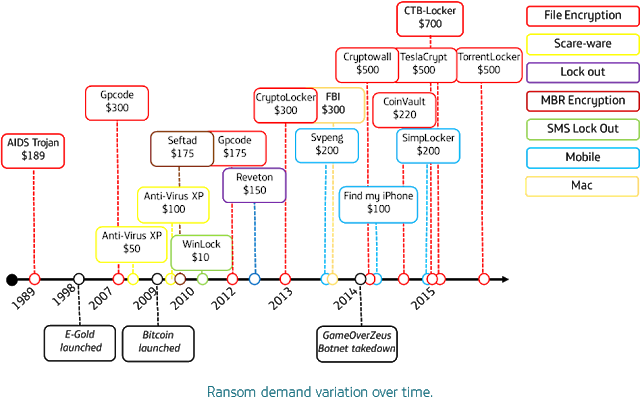
Smart Cities are no longer a promise of the future but an increasing priority for local, regional and countrywide governments and a flourishing business area for technological firms and CSPs with interests in the IoT market.
The European Union is so far the part of the world where more efforts have been made to develop smart cities. At the same time, we find a higher degree of scrutiny and follow-up of how well they rank and abide to predefined European standards. Despite being a conglomerate of various countries with different legislations, areas that affect smart city legislation, such as environment or mobility are normally legislated at Union level, easing the path to creating a more homogeneous standard for Smart Cities, and helping EU based companies to bid for projects in different countries.
LATAM is following this trend and starting to understand the different European experiences in order to begin building the most adequate ecosystem for the development of Smart Cities.
Telefónica has a four pillar guideline that serves as a best practices guide of how to successfully turn Cities into Smart Cities.
- Go hand in hand with citizens
The citizen must perceive Smart City improvements as advances that provide better and more efficient municipal services enhancing life in the city. Smart Cities must inevitably improve pre-existent conditions substantially in order to justify investment and the logical inconveniences during the initial deployment.
- Open for Business
It is key to adopt an integrating vision when planning Smart Cities. The best option is to opt for open standards with a holistic perspective that easily integrate any potential technological partners in the platform and ensure continuity in time. Smart Cities should always use top down design approaches with the citizen in the center: the final objective is always to offer better services to the citizenship.
Each layer of technology is set to serve the next in a four tier architecture:
Sensors > Connectivity > Management Platform > Analysis and Intelligence
- The best partnerships provide the best results
Having solid technological partners with proven know-how to efficiently deploy these services and maintain them in good shape is fundamental in order to meet citizen’s expectations
Expect the best from the best. Seeking expertise and market leadership implementing solutions is a sound approach to achieve optimal results. Best in class partners provide their portfolio of top class solutions and the necessary experience to successfully deliver projects within the planned scenario timeframe and budget.
- Involving startups and SMEs
It takes more than a group of large corporations to deploy and maintain Smart Cities. Disruptive technology is often introduced by smaller startups with bold and innovative ideas. It would be a mistake to rule small companies out of this transformation process as they have an important role to complement successful Smart City developments.