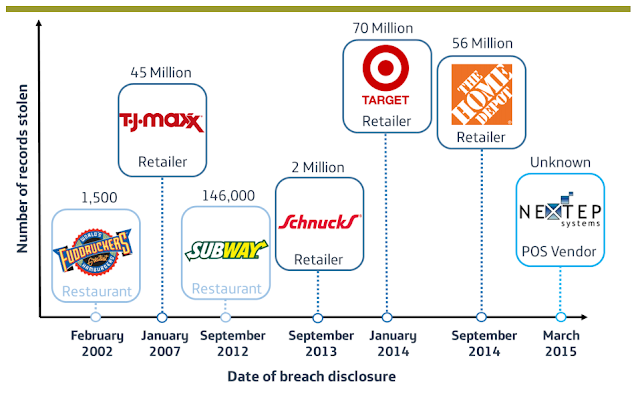
Although the smartphone has been the catalyst for the shift towards more secure mobile payments, credit and debit card transactions at point-of-sale (PoS) still remain the main entry point of consumer data into merchants’ information environment. Perhaps an obvious point, and one certainly not missed by cyber-criminals if the “mega breaches” affecting major U.S retailers in the past few years are anything to go by.
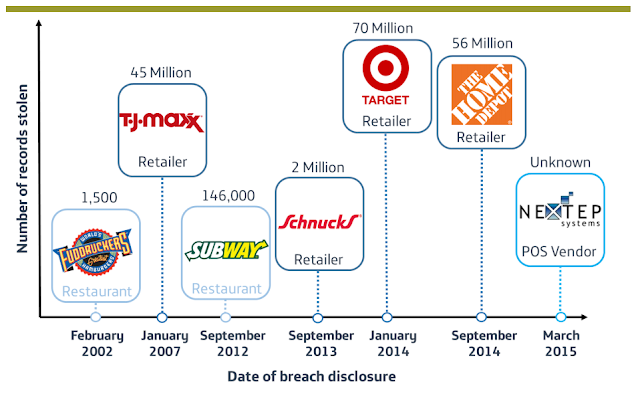 |
| Illustration of PoS malware breach headlines, 2002- 2015 |
Targeting the weak link in PCI-DSS, cyber criminals have refined PoS malware, employing “RAM Scraping” techniques to parse memory processes on PoS terminals before card data is encrypted. It is now a mature cybercrime model, responsible for the majority of confirmed data breaches and feeding a booming underground marketplace. Focusing too much on the headline-grabbing breaches belies that from a frequency perspective, small and medium sized enterprises are most affected; criminals are after the money, not the headlines. However, awareness has undoubtedly risen, and the average time between breach and detection appears to be narrowing, but the number of detections in Q1 2015 outstripping the previous two years is also a narrative of soaring propagation rates.
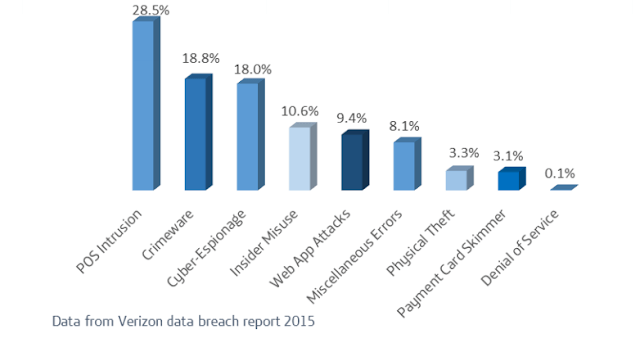 |
| Frequency of incident classification patterns with confirmed data breaches |
Industries with high card transaction volumes (particularly hotels and entertainment) in addition to the more obvious retail sector, are most at risk from PoS malware. The size of the U.S economy combined with the late adoption of EMV “Chip and Pin” technology ensures it will almost certainly remain the most targeted during 2015, and an attack surge within the target rich environment is possible before the October implementation deadline. Although even when EMV is implemented, data remains that enables fraudulent e-commerce transactions. In large enterprise, the drive for innovation at PoS can see security overlooked in favour of the consumer experience and integration with other business applications. Secure technology that would hinder PoS malware such as end to end encryption is often unrealistic for small and medium sized businesses to implement. Conversely, criminals are able to call upon a readily available and proven PoS malware codebase, unthreatened by obsolescence of a PoS data environment set to remain largely Windows XP based for several years to come.
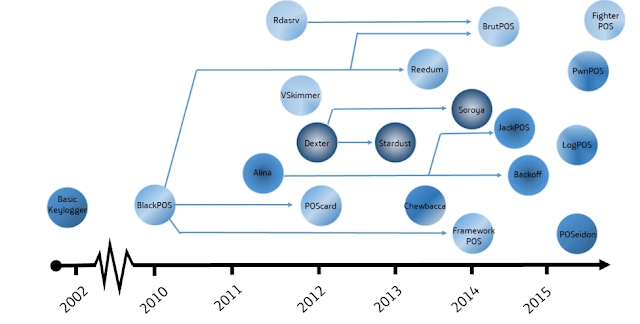 |
| Evolution of PoS malware variants |
Technical analysis reveals heavy development occurring across a few key codebase variants, with some strains adopting nation-state level complexity and others stripping back and removing unnecessary overhead. The overall malware campaign, in particular the exfiltration of stolen data can be complex, and is often based on detailed network knowledge.
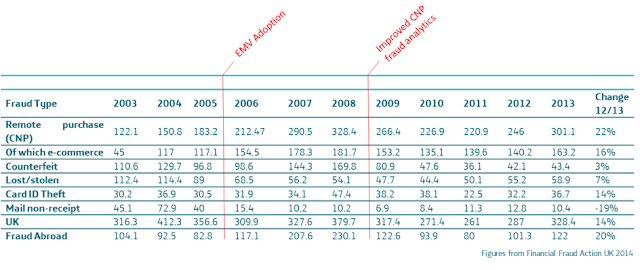 |
| Figures in millions (pounds) of UK credit card fraud and countermeasure implementation date |
While it is possible that large companies may be able to limit the impact of protracted “mega breaches”, the risk of smaller more distributed breaches remains, and the upwards trajectory of PoS malware in 2015 shows no signs of slowing. However rather than be overawed in the face of the threat, it should be remembered that common PoS network intrusion methods such as phishing and attackers using default passwords are often targeted but nothing new.
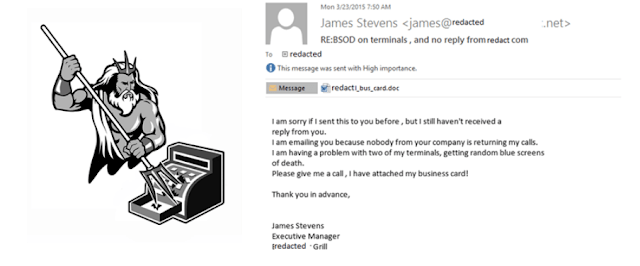 |
| PoSeidon Logo and a phishing email campaing used to target PoS vendors |