We have studied some details of the leaked APKs. They were not public until this recent attack, and they were not detected by many antivirus engines until the leak. It is not the first time that we know about this company’s APKs. During 2014 summer, some remote control Android apps were known to belong to this HackingTeam, and they were used to spy mobile devices.
A certificate for binaries in an APK. waste and a mistake
To digitally sign an executable file in Windows, an Authenticode certificate is necessary. It may be expensive, between 200 and 500 euros a year, depending on the CA that issues them. To sign an APK, Android doesn’t require anything. It may be “self signed” and, therefore, free. And that is the way most of developers work. In fact, from our database, less than 100 APKs (0,002% approximately) use certificates signed by a CA.
The APKs from HackingTeam were signed by this certificate that allows signing executable files as well.
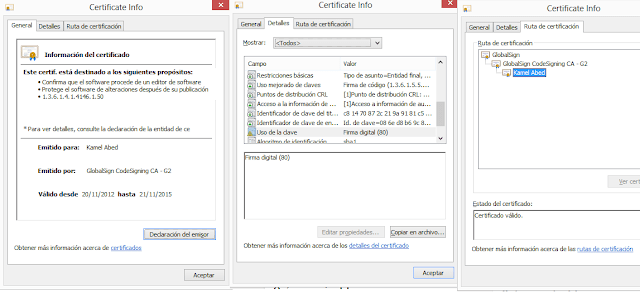 |
| The three views of the Authenticode certificate used to sign the APKs |
And the problem is not only the waste, but the exposition. These certificates were already known since early 2013, when the tools used by HackingTeam to spy remotely were discovered. So, these APKs have been signed after that, in March. We already knew, by then, that they have been used to sign malicious code (at least, since February 2013, as this link states). An unnecessary mistake from HackingTeam.
The certificate expires in November 2015. As a side note, in the executable files (in the APK, it does not make any sense) it’s revoked and is not countersigned. That means that, even if it wasn’t revoked, it would stop working in November 2015.
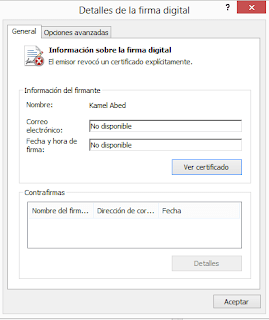 |
| Binary file signed with the same certificate |
What apps they were pretending to be
A quick search by the packageName allows us to know what apps were trying to be simulated and contained the trojan. These are some of them that we found.
 |
| Some examples of legitimate apps used as a decoy for the trojans |
All of them may be downloaded right now from aptoide or Google Play (although in the latest you may find the earliest versions). The topics are different. From the Quran to spy cameras.
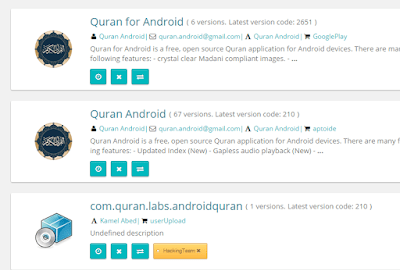 |
| Legitimate apps used to create the malware |
Obviously they differ from the good ones in several aspects.
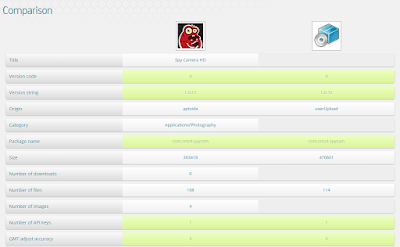 |
| Comparing the legitimate and the trojanized app |
Much more permissions are needed and a Google Map link is always in the code. We guess they locate victims this way.
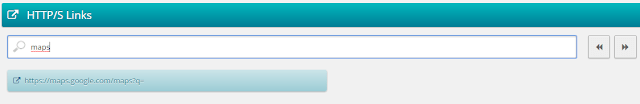 |
| All the HackingTeam apps keep a Google Maps link in them |
We insist: these apps shown in their markets are innocuous, it’s just that HackingTeam uses them as trojans (in the more classic meaning of the word) to encourage or disguise the malware installation.
More notable facts
Both in this leak and previous analyses made to HackingTeam programs (like the one on 2014 summer, where some trojanized APKs were discovered as well), we can see some that could have allowed the early detection of these trojans (aside from using the same certificate). For example, all the APKs share a singularity: between their /assets/, they keep binary files named with a single letter.
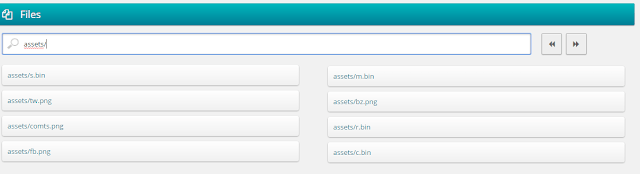 |
| HackingTeam Android malware contains this kind of files, with these singular names |
Searching by this kind of file or some of these hashes, we found no other sample containing them in our databases.
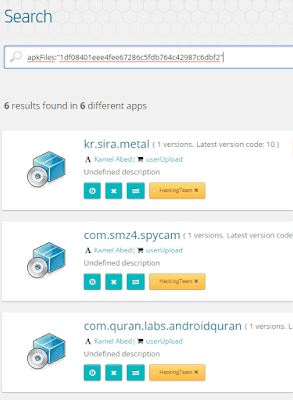 |
| Some of the files shared by HackingTeam samples are a singularity for them |
Finally, all the APKs in this leak (except one) were created “2013-04-09” roughly at 11:40, local timezone from the computer they were compiled in.
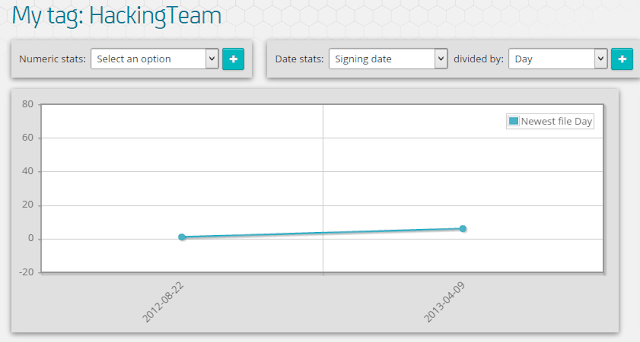 |
| 6 apps were created March, 9th, except one |