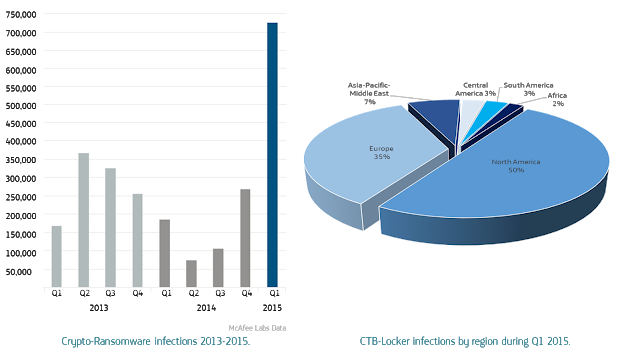
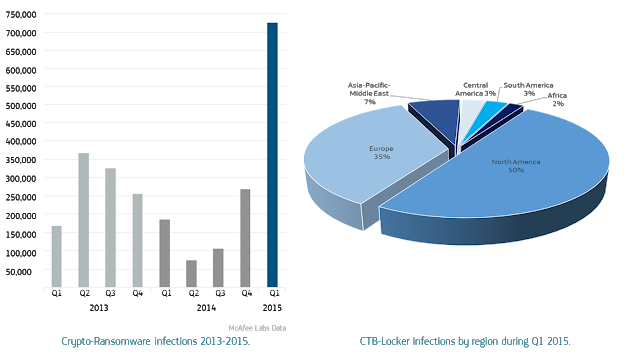
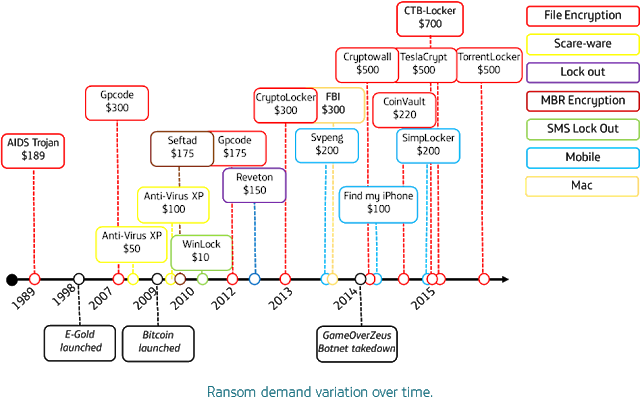
The scourge of crypto-ransomware malware featured prominently in threat predictions for 2015, and the 165% increase reported in Q1 2015 indicate that these fears were well founded. Using a criminal model that runs counter to many of the others included in the threat predictions, crypto-ransomware is not concerned with exfiltrating valuable data, instead surreptitiously encrypting files to subsequently employ an abrupt, confrontational extortion demand. While on the surface the technique may seem crude, the evolution of crypto-ransomware and the criminal marketplace which has served as its incubator, it is actually a calculated operation, abusing technologies long upheld by privacy advocates. The propagation statistics of the CTB-Locker variant are broadly illustrative of the overall geographic spread of this subversive threat to date during 2015.
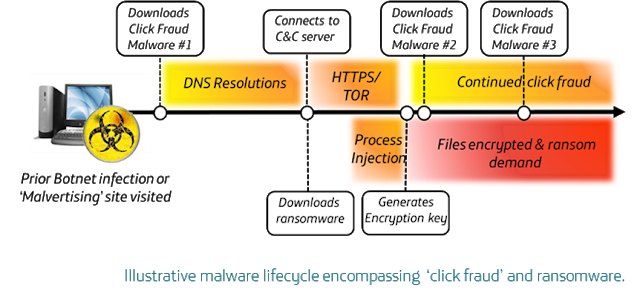
The infection vector criminals use to distribute crypto-ransomware varies, and is often symbiotic with prior malware infections; during 2014 it would often be a result of the Gameover Zeus botnet, and 2015 has seen an increase in ransomware as part of a malware lifecycle encompassing ‘click fraud’ and ‘malvertising’.
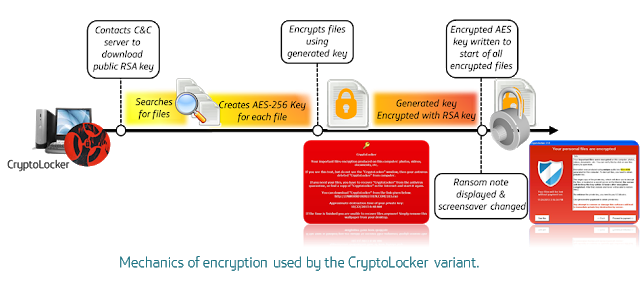
Once infected, asymmetric encryption is employed to create a public-private key pair for the malware to encrypt files. The key used to encrypt the files is often itself encrypted again, in a process often using a combination of RSA and AES cryptography, and ultimately without access to the attacker’s private key it is next to impossible to decrypt the data.
Over time the price point of the ransom demand has been adjusted by criminals, and is now commonly around $400 (€360) to be paid in Bitcoin, which appears to be close to the price ceiling at which untargeted ransomware balances likelihood of payment with the maximum ransom demand from an average user. However in June 2015 the FBI issued an advisory stating the CryptoWall variant had caused $18 million in damages including ransom payments of $200-$10,000 from both individuals and businesses.
Crypto-ransomware epitomises the nexus between the modern cyber-criminal and effective use of age-old psychological intimidation, and is a model that appears to scale well to technologies like mobile, cloud and IoT. Indeed the potential for this threat to develop further, nurtured within the cyber-criminal ecosystem is perhaps more sinister than viewing propagation statistics alone.
The only way to nullify the criminal business model is if no-one paid a ransom; however such idealism is of no compensation to an individual or business who have been infected and lack sufficient safeguards. Security awareness and system hardening are preventative measures, but the only contingency to rely on should infection occur is to have sufficient backups; ideally three copies, in two different formats, with one stored offline. Coding errors and seizures by law enforcement relating to specific variants may offer a chance of decryption in a small percentage of cases, but a ‘cure’ should be regarded as non-existent. The criminals may never even intend to provide decryption, but the trajectory of ransomware is testament to the number of unprepared victims who felt they had no other choice.
» Download the “Cyber Security Pulse and Ransomware report”