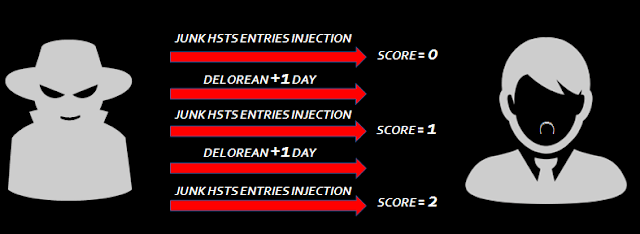
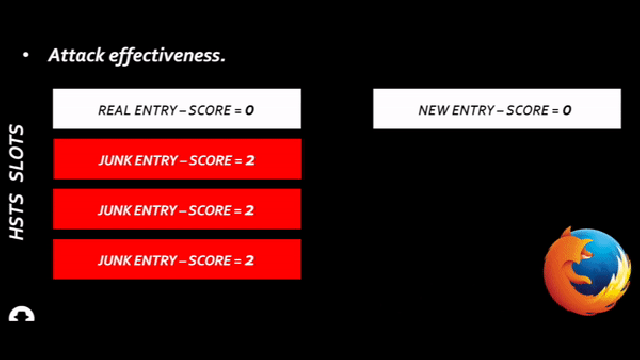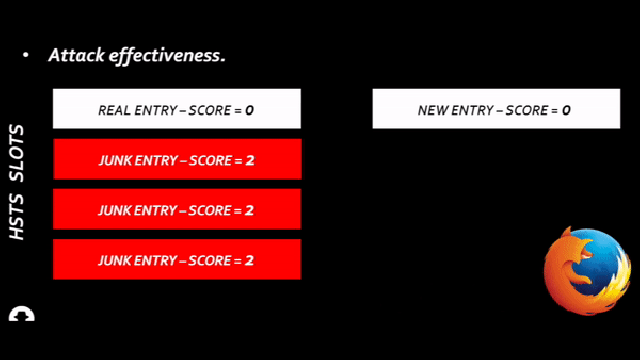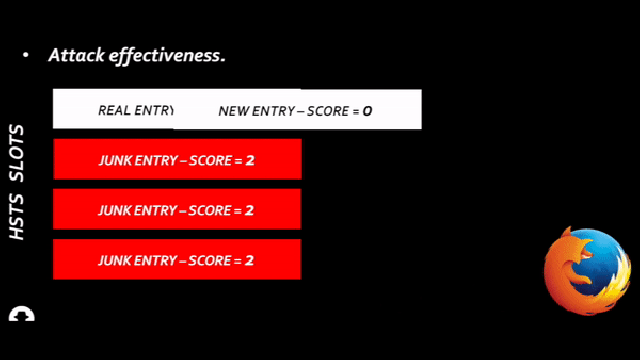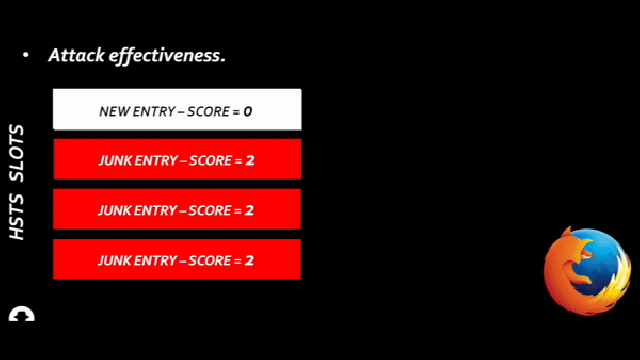
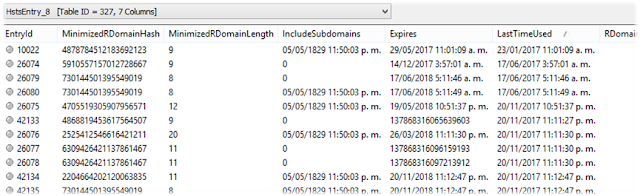
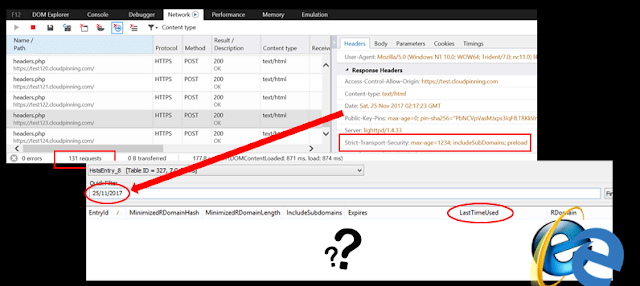
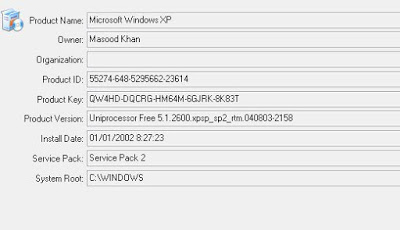
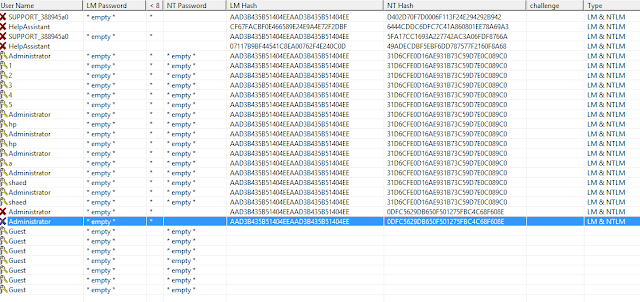
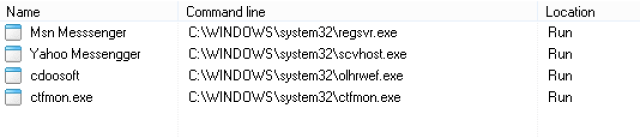
“With the dataset from this project we can have our Mobility Plan ready. It is important to recall that this is a very advanced way to obtain the needed information with the same accuracy. This system replaces the old one which, manually, we would do by counting people and their displacement”.
Don’t miss out on a single post. Subscribe to LUCA Data Speaks.