We have been monitoring security in industrial environments for some years and have seen how these infrastructures have become a target for cybercriminal groups.
Our innovation area has developed a system for capturing threats in industrial environments which allows us to carry out a detailed analysis of the attack techniques and tactics used in this area.
Threat detection in industrial systems
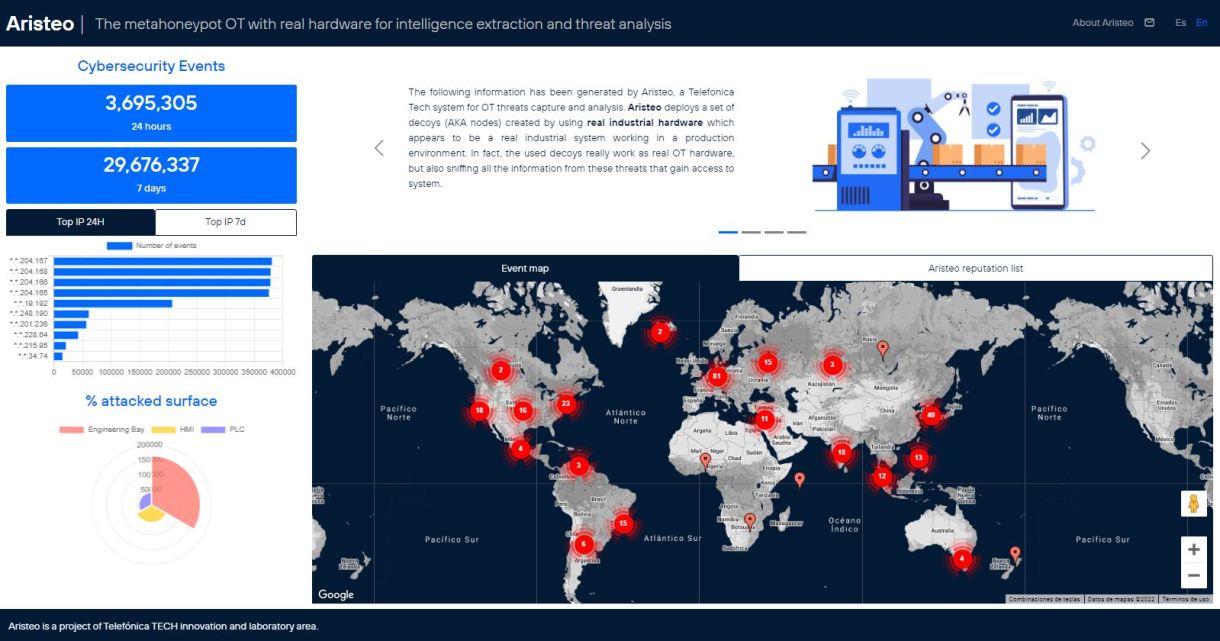
With this honeypotting tool called Aristeo, we have seen exponential growth in attacks, reaching figures of around 7 million detections in 24 hours and 35 million in 7 days.
The data from these samples allows us to show that the IT components of OT infrastructures are the main attack vector. In our tool they are called Engineering Bay and HMI, systems that are usually supported by common operating systems and protocols in IT networks.
These detected attacks can mostly be mapped to the techniques that make up the initial access tactics framed in the ATT&CK matrix for ICS, which was updated on 21 April.
Additionally, these detections often turn into ransomware attacks, as indicated by Nozomi Networks in its 2H2021 security report.
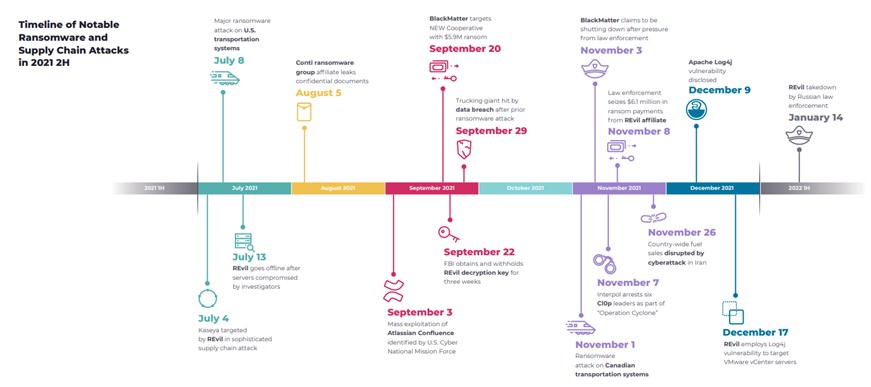
The biggest concern about this increase is the physical repercussions that these attacks can generate, which have increased in the last two years.
Cases such as the JBS Food hijacking, which caused meat shortages in several countries around the world, added up to 10 impact cases in 2020, surpassed 20 in 2021, and are projected to reach 50 in 2022, according to waterfall and icsstrive’s OT incident report.
Improvements for threat detection in industrial systems
This trend has led to more in-depth and detailed research into potential vulnerabilities in industrial systems equipment, with 651 reports on 47 manufacturers and 144 products by the second half of 2021 alone.
Companies in the industrial sector have improved their own threat detection and testing systems. The best example of this is Siemens, which created a CERT and reports once a month all vulnerabilities or updates of vulnerabilities in its products (a process similar to Microsoft’s). By May 2022, they reported 27 alerts, of which 12 were reports of new detections.
This initiative has been followed by other companies in the sector, such as Schneider Electric, which, like Siemens, opted for the strategy of monthly reporting of threat detections revealed by its research teams or by external researchers. In this case, for the month of May they reported 6 alerts
Cybersecurity, a critical need for industry
These changes in industrial environments undoubtedly make cybersecurity a burning need. As we have said on previous occasions, they require a change in the approach of the operations teams and an integration of these networks into the security governance of the entities or companies.
One of the common points in specialised OT cybersecurity analyses is the lack of visibility of events within operations networks, which means that incidents cannot be detected in their early stages.
The reason is that you can’t protect what you can’t see, and industry studies have confirmed that less than 62% of companies have complete visibility of network events.
In terms of personnel, it is critical that operations environments start with cybersecurity training processes on an ongoing basis, just as they are constantly trained in occupational safety, operational risk and occupational health processes. It is essential that operators understand the importance and procedures they must comply with to safeguard information.