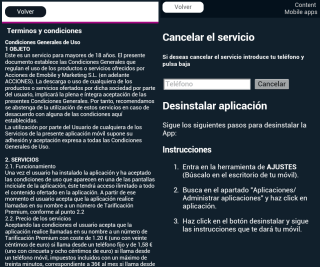
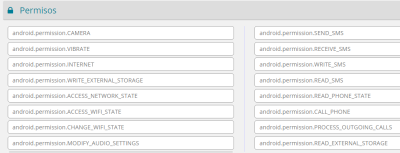
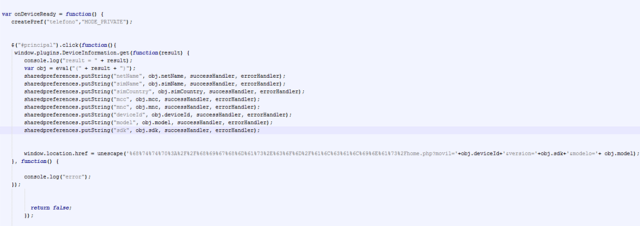
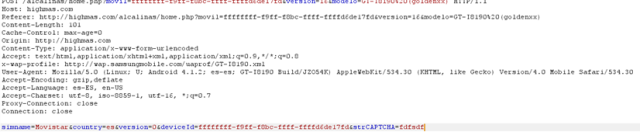
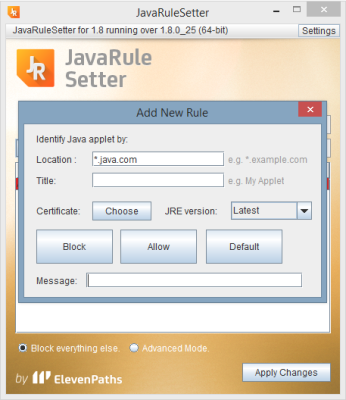
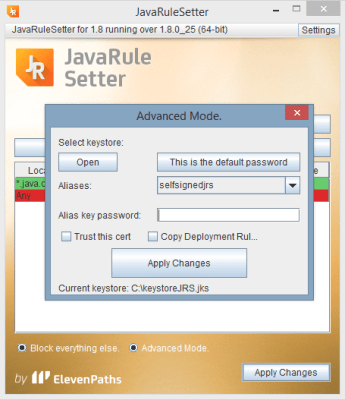
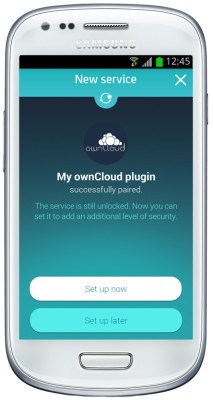
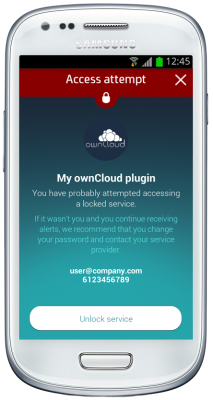
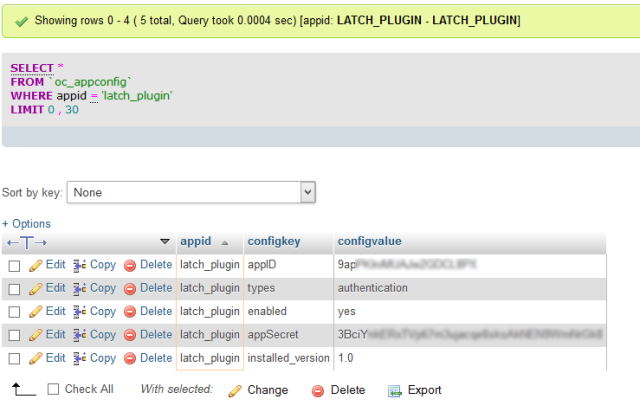
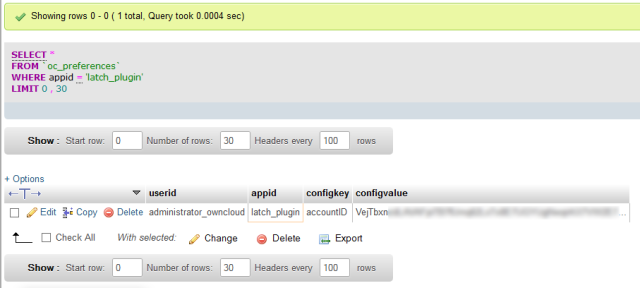
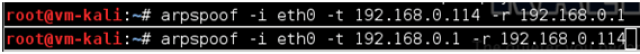
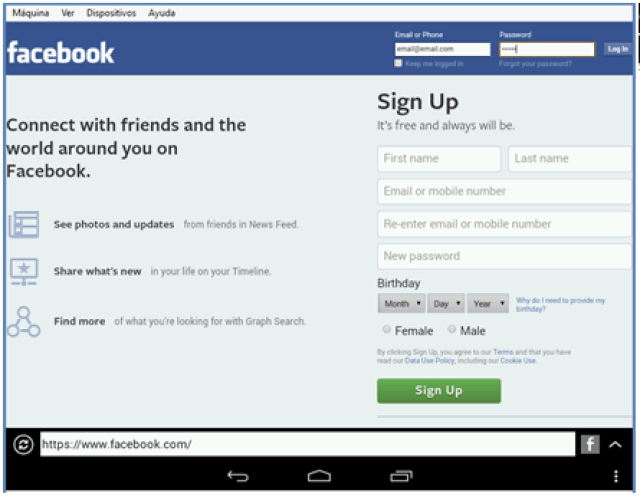
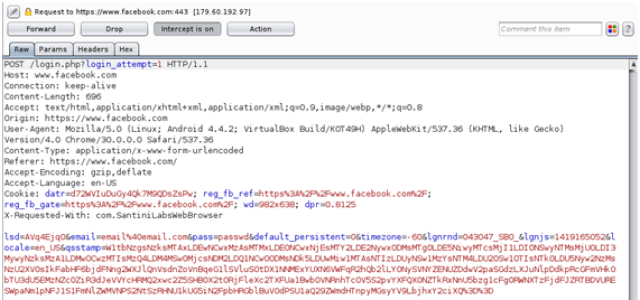
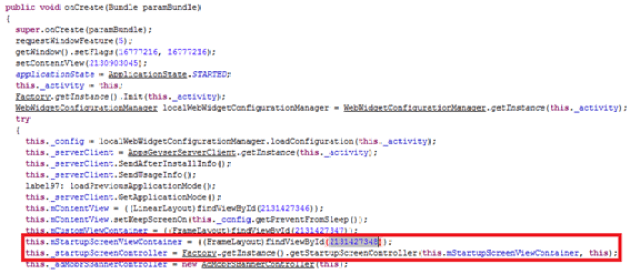
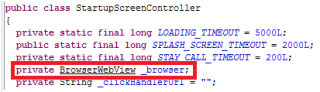
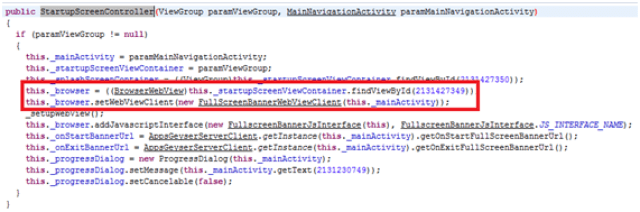
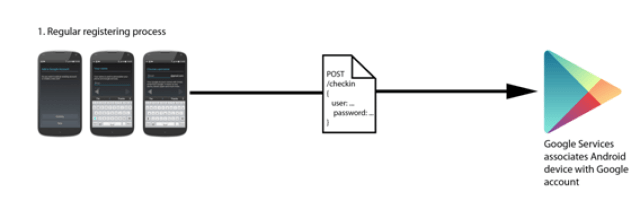
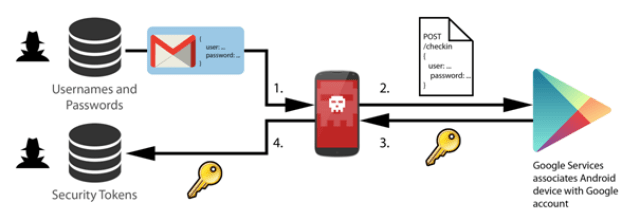
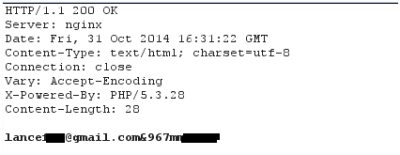
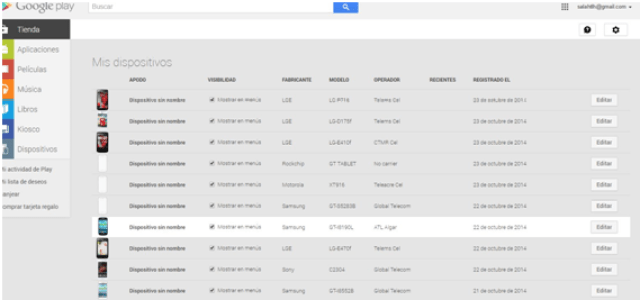
This solution is compatible with the new Spanish electronic ID, DNIe 3.0, which allows for secure identification and replaces common passwords with multi-credential systems which combine at least two factors to establish the user’s digital identity. By using SmartID Spanish companies can implement security solutions based on the new identity card quickly and easily, reducing fraud and identity theft.
SmartID and SealSign on Mobile World Congress 2015
Florence Broderick 23 February, 2015
This solution is compatible with the new Spanish electronic ID, DNIe 3.0, which allows for secure identification and replaces common passwords with multi-credential systems which combine at least two factors to establish the user’s digital identity. By using SmartID Spanish companies can implement security solutions based on the new identity card quickly and easily, reducing fraud and identity theft.