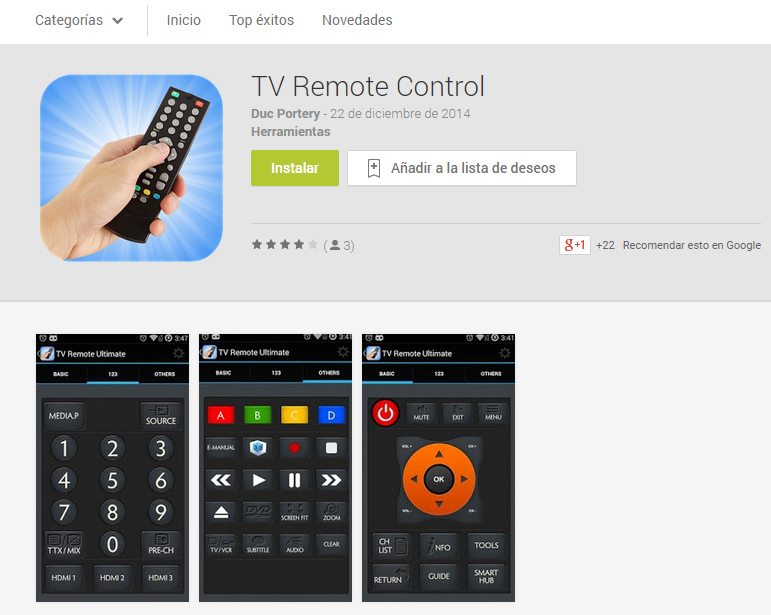
Since December, a developer has been uploading apps to Google Play, with the only intention of booting with the device and make GET requests in the background. Promising different kind of apps (from remote controls and X video searchers to flight simulators and games) these apps sum up to 50.000 downloads between all of the 32 apps we have spotted. Obviously not all the downloads translate into an infection (VerifyApps and other factor may affect) but they seem to be quite popular.
 |
| Some of the apps are just “clickers” under different “disguises”to attract victims |
One of the apps is a scientific calculator with the description text in Italian. We have asked Google to remove the application that was still online (maybe because it was a little more advanced than the others and passed unnoticed) and that we have located thanks to Path5.
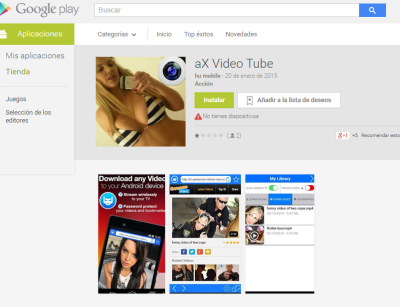 |
| App that wasn’t removed from Google Play. One of the latest remaining. It worked in a more sophisticated way than the others. |
What the app does
When it starts, it always shows a dialog with the text “Application is not compatible” in Italian, Turkish and Spanish, between other languages.
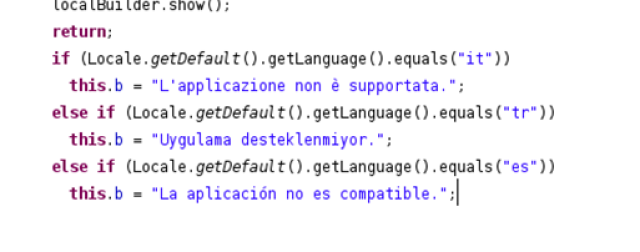 |
| The app always shows the same dialog when it starts |
It hides its icon, modifiying values in the Manifest, after the first time it runs and after showing the message. It does nothing else until it receives a change in WiFi, data connection or a reboot. It connects to this encoded URL (it is not base64, although it looks like it).
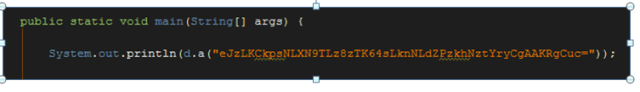 |
| Encoded URL |
Decoded, it turns out to be: hxxp://1.oin.systems/check.php. If it responds with a “True” (which is pretty much always by now), its activity will start.
Other variants connect to other URLs like this one:
Or this, depending on the sample: hxxp://pop.oin.systems/commands.php.
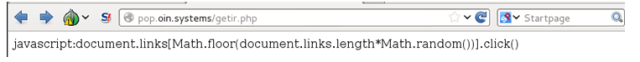
Every time a new request is made, the apps get instructions on where to go and click. In every connection they get new domains to connect to.
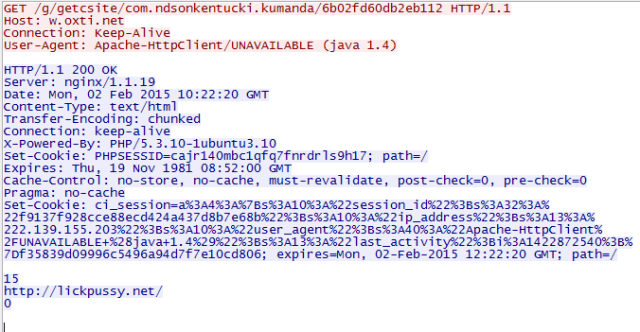 |
| Request for the place it has to visit |
In just a few minutes, the device has generated dozens of requests. For the user standpoint, the problem will be the data consumption if he has a paying data plan. Apps are activated when the device boots so, although the app itself is not active or launched, the device will be consuming data all the time.
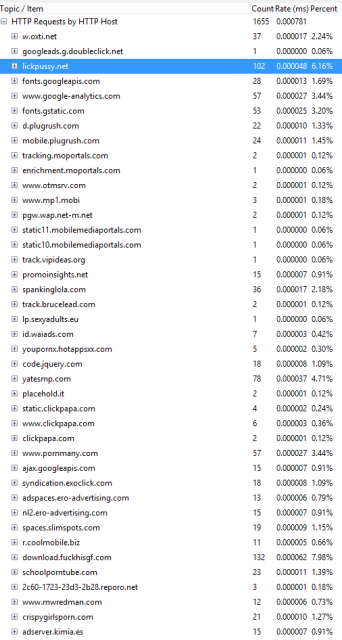 |
| Extract of the traffic generated by the device during a few minutes. Most of them are porn sites |
Indiscriminate visits will be done through a service that builds a WindowManager with a weight and height of “-2” so the user is not able to actually see it in the screen, where a WebView is added. There is where the URLs are loaded.
It will take some other values from some other URL. Every 15 seconds (time to load the web) it will call:
Another task will take care of executing this JavaScript over the loaded URLs. This will result in random clicks on the web.
This strategy of hiding the icon, avoids the user to even bothering in uninstalling an app, because he will think it was never installed in the first place. Moreover, if it keeps quiet until next reboot or when connectivity changes, there are more chances of the user forgetting about it.
Permissions are not very blatant.
 |
| Permissions of these apps |
Detection
The app was not deteced by any engine during December and January. January 20th we sent it (for the first time) to VirusTotal from ElevenPaths’ lab.
 |
| Detection in January |
Eventually in February, some engines started detecting it. Engines have created a specific signature for this family, called Riskware.Clicker.
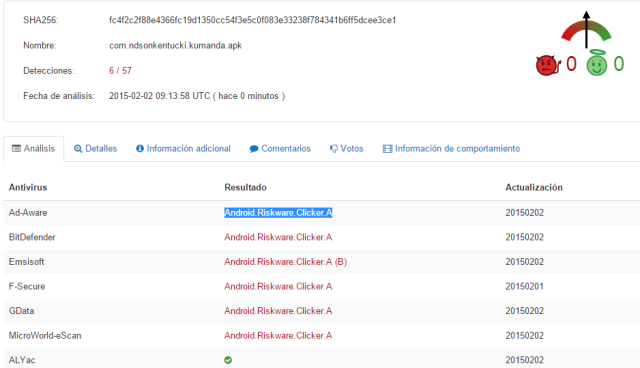 |
| Detection in February |
The attacker
This is a typical schema, but quite witty in its implementation. We have detected that the attacker has been acting since later December and that he probably is Turkish (thanks to the information obtained from its ad-hoc certificate). Its current timezone is GMT+2, added to the language used in some apps, makes us think that it’s someone developing from Turkey, although with some Italian relationship. Some other specific characteristics has allowed us to spot the other apps very quickly.
The strategy has been the usual one. During most of the time, the app starts in Google Play like an anodyne app. It consolidates in the market and maybe someone downloads it. For the next version, the apps mutate into something more attractive to the user, maybe it changes the code, maybe the icons and description. In this moment a “race” starts, because Google will remove it quickly but it will try to get the more the better installations.
 |
| The app was something called Beklre (up in Google Play) and then mutated into a fake Talking Tom (down in Path5) |
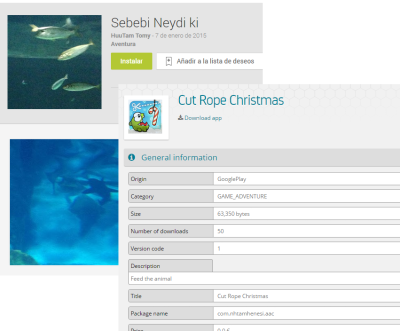 |
|
The app was something called “Sebebi Neydi ki” (“Which is the reason” in Turkish)
and then mutated into a fake Cut the Rope for some hours (down in Path5)
|
 |
| Some other apps that seem to belong to the attacker |
Miguel Ángel García
[email protected]
@nodoraiz