The power of a good headline is hypnotic. The one taking a lot of security news during these days is the “Found first malware for Firefox OS”. The title is attractive, but, is it right? Reading the news invites to think about what has really happened, what is this “discovering” about, and why we haven’t overcame still so many myths.
Firefox OS is a recent operative system based on web. All its programs are web based, created using JavaScript, CSS3 and HTML5. This implies that applications may be distributed in two ways: in a zip that contains it all, or via an URL that hosts it and is later visited.
A 17 years old by has developed a malware proof of concept for Firefox OS. He will be presenting its research in a convention in November. He states that his application allows to perform some potentially unwanted remote tasks over the device, and that is able to control it sending remote commands.
First of all, security model
According to Firefox OS security model, “uses a defense-in-depth security strategy to protect the mobile phone from intrusive or malicious applications. This strategy employs a variety of mechanisms, including implicit permission levels based on an app trust model, sandboxed execution at run time, API-only access to the underlying mobile phone hardware, a robust permissions model, and secure installation and update processes“. So far (except the way hardware is accessed), nothing that any other operative system doesn’t implement (and nothing that really may stop “infections”).
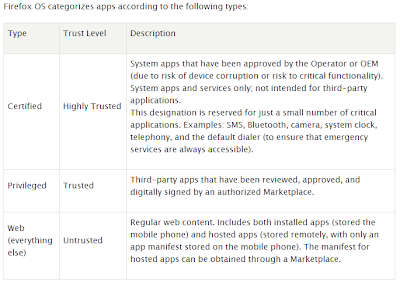
Something that, in some way, may make a difference in Firefox OS, is how it classifies permissions in apps. There will be three different kinds:
- Certified: the ones installed by the vendor and critical functionality (telephone, SMS, bluetooth, clock, camera…). They will be able to access any API. For example, only certified apps (the ones coming with the device) will be able to make phone calls.
- Privileged: The ones reviewed, approved and digitally signed by an authorized marketplace. They will have access to a subset of APIs accessible to certified ones.
- Untrusted: The other ones that will not be in a market. These will have only access to a subset of APIs that may not make any harm.
Let’s see now what can be deduced from the announce of the program created by Shantanu Gawde.
Differenciate between the “what” and the “how”
A teenager has created an application that makes unwanted actions on the system. He talks literally about “infecting” and “control like a botnet”. About sending commands to access SD card, about “spooking the user remotely controlling FM radio”, “upload and download multimedia files”. It seems to be able to control certain device apps, but we do not know how far it may go.
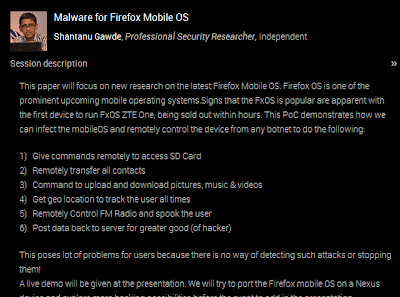 |
| Official description in http://g0s.org/key-focus-areas/ |
Is this malware? It depends. There will be legit applications that will need to access SD card data, contacts, etc. It will be allowed because the user will trust the vendor or developer. As the Firefox OS security description document states, the model is based on application trust.
What may attract some attention is the state about controlling other apps (he specifically talks about controlling FM radio). Talking about “sending commands” invites to call it “malware”, too, though, once the application is installed, it seems quite easy to send commands… so in general, the problem is not so much “what” does this proof of concept do, but “how”, how does it get the necessary permissions and how it got to get them. With the information we have, we guess the user launches an application hosted in a server and accomplish some tasks that may be potentially unwanted by the user.
More questions than answers
To get to the real scope of the statement, we should answer these questions.
- Is this program able to bypass some security restriction in Firefox OS? This would include elevation of privileges, accessing without permissions to privileged API, bypass security dialogs, warnings that could alert the user… any way that implies bypassing, breaking or evading Firefox OS security model. It seems to do that, but it’s not clear.
- Does the malware replicate itself in some way, for example leveraging some vulnerability or design flaw? Does not seem so. If Gawde had found a way to spread a program without human interaction, that would have been breaking and disturbing news. But, with the information we have, it does not seem to be the case.
- Does the malware hide itself in some way, for example in legit apps? It does not seem so, either. It would have been interesting if a way of launching hidden or embedded apps had been disclosed, just as the first “virus” did. What may be a problem with Firefox OS is, that confusing or obfuscated URLs hiding apps would execute just with a click… and that has been alerted since long ago.
- Are special circumstances needed for the proof of concept to work? Are just some devices vulnerable?, Does it work with default configuration? Or is is necessary to keep some service, or app working…?
- Does it use any technique to hide its execution from the user? Something that attracts attention is that the developer itself says “there is no way to detect the attacks or even stop them”. In security, such convincing assertions are usually misguided. We suppose he refers to a model where an URL is visited and it results in an app executing that starts, without user interaction, some information exchange between the “victim” and the attacker, that may control the device.
Without these answers (between others), information may be based just on speculation. And the developer should have answered them beforehand in his statement, just like others do, so we can understand (without the need of technical details) how he got it and not describing so much what he got. It should be highlighted that he states that the purpose of the PoC is of course to motivate developers to ensure better security on their platforms rather than providing inspiration to those with malicious intents.
Anyhow, the “malware” or any other in the future will not be exactly a surprise. When execution of uncontrolled applications and alternative “markets” are allowed, abuse is practically guaranteed. Although it’s through restricted applications, many of them will not need special permissions to infect with “adware” and show ads, and some other may just find some ways to bypass permissions leveraging vulnerabilities or design flaws.
A Firefox OS spokesman states that possible, Gawde relied on developer mode functionality, which is common to most Smartphones but disabled by default. In addition, we believe this demonstration requires the phone to be physically connected to a computer controlled by the attacker, and unlocked by the user. In other words, they think he has “cheated”. Of course, they try to downplay the issue because of the lack of information.
So, without any more actual data, the headline should be that a researcher has possibly found a design flaw or a way to bypass some security in Firefox OS, executing privileged remote actions on the device. But we can’t be sure yet. What is for sure is that, talking about “malware” confuses the user, that may feel menaced without an actual reason to… yet.






every os has malware, osx, windows, android, etc. It isn't an os if it does have malware 😉
Very useful post. This is my first time i visit here. I found so many interesting stuff in your blog especially its discussion. Really its great article. Keep it up. Search Bar Firefox 57 Quantum addon