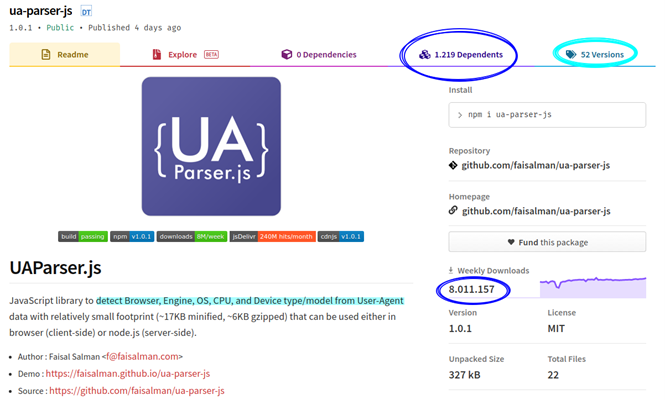
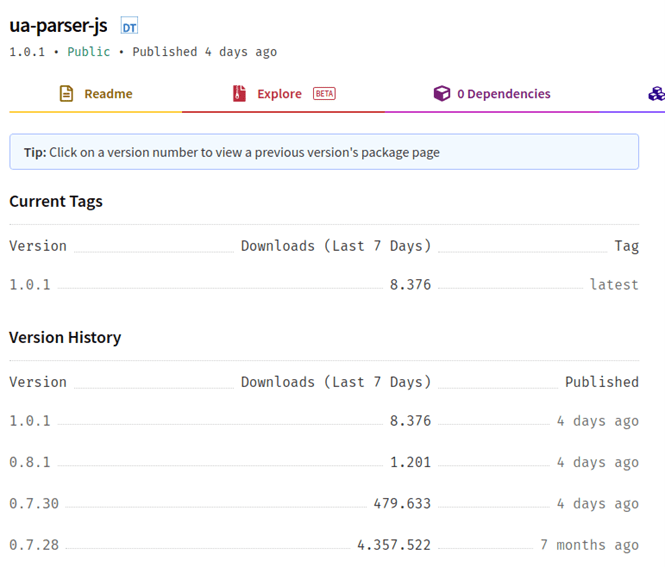
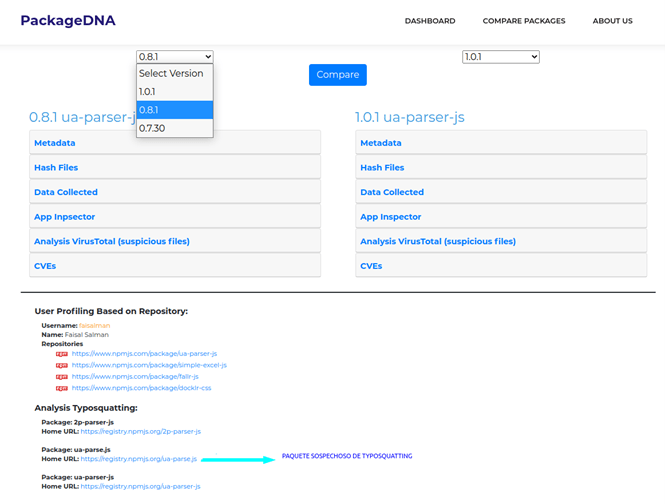
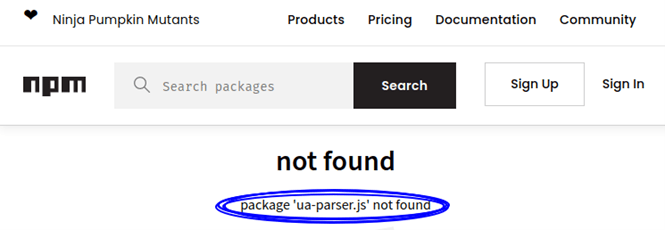
As promised last week in the first post of this series, this time we will talk about how to minimise the risks of our digital footprint.
¿ How to minimise the risks of our digital footprint?
The first thing we should focus on is egosurfing. This consists of doing a search on yourself in the different search engines to see what is available. To do this, it is not enough to search only by our full name, but to make combinations of our names, emails, phone numbers, IDs, or usernames through dorks. This involves using special operators and symbols in the various search engines, such as those offered by Google.
Based on this initial research or analysis, we will go on to collect the information and assess the associated risk. Assessing our exposure and digital footprint on ourselves or our organisations, seeing what is available, where and what risks it carries, is of vital importance to reduce our vulnerability to malicious third parties.
Once we detect and have the exposed information on our radar, in those cases where we have sensitive information, it is advisable to delete or hide the information. To do so, it will be essential to:
- Keep track of which pages or services we have registered on.
- Correctly configure the visibility of our profiles on social networks and control the content we upload.
- When registering for a service or profile, we will be asked for a lot of voluntary information about ourselves, such as likes, hobbies or place of work. It is worth assessing what information we want to provide and reviewing the purpose of the processing of our data.
- Avoid signing up for dubious-looking services and assess whether registration is necessary. Even if a service promises privacy, there is always the possibility of unintentional data leakage.
- Use different e-mail addresses for different areas of your life (work, personal, etc.).
- Do not reuse passwords and keep them under control together with your login details, e.g., through password managers.
Now that we know how to minimise the risks of our digital footprint, let’s see what practical resources we have for information removal. Next week we will tell you about it.