The weakest link
 |
| Finding Nemo. Source: imdb.com |
Whether or not they realize it, organizations depend on us, also around the clock, to defend both personal and enterprise interests. Attackers can leverage vulnerabilities in our personal digital lives to get at our employers, and vice versa; and often, this is precisely what they do. Users are an easy mark. We are the weakest link, “the fish” as they say at the poker table susceptible to phishing, watering hole, and social engineering. We are error prone, willing to sacrifice security for productivity gains, often lazy, or resistant to security policy. To make matters worse, when we leave the office we haven’t got the resources our employers have; and so, we don’t take the precautions that might otherwise help our organizations minimize the risks associated with attacker-leap-frogging from the personal to the professional.
Just as with businesses, the overall level of risk to which we, the fish, are exposed is increasing, and we ought to dedicate more care and awareness to safeguard our personal digital lives, the same way our employers do to protect their assets. But, we don’t (at least not the majority of us) and so long as we don’t do enough to protect ourselves we will continue to be fish.
Long live the antivirus?
There´s a paternalistic aspect to securing users and consumers that, though well intentioned, may ultimately have caused this problem. I am referring to the very global security policies and measures to which our organizations subject us. Take the antivirus as an example. The antivirus is practically ubiquitous in desktop systems of all large and medium enterprises, and its presence is enforced; sometimes even on visitors and contractors, through policy, and complex and expensive network admission control systems. Enterprises have been singing the praises of antivirus in this way, both explicitly and implicitly, even when “fake-av” aka “rogue antivirus” came along in 2008 to sound the death knell on the venerated, but tired bluff of recursive decompression, signatures, heuristics, and so forth.
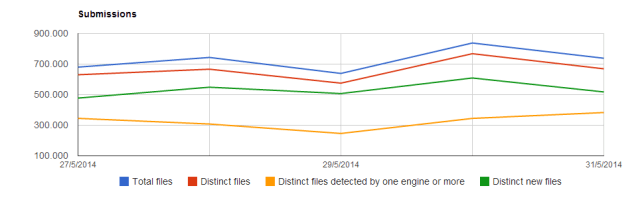 |
| Virustotal statistics |
Enterprises and households could have saved themselves numerous headaches, by focusing their time and budgets on alternatives to the antivirus, years ago. At least since 2007, when studies began to demonstrate that the trusted software was only effective 20-30% of the time. Instead, we all soldiered on, long after the tool was rendered more or less useless. It survived, thanks in no small part to organizations that insisted on playing this losing game, throwing good money after bad on a losing hand. The thing is, antiviruses have become largely irrelevant to attackers, who now avail themselves of novel vectors of entry inaugurated by the mobile-cloud-social era in which we all live.
But, let’s set aside the irrelevance of antiviruses, and their technical limitations. (Antivirus technology has always imposed significant system performance issues, the risk of false positives, and even an additional attack target due to its kernel level access). Their ineffectiveness is not just limited to the underlying technology, but also due to the lack of user involvement and understanding. How many users know, or even bother to tune the software to their system? How many are aware that it does not adequately address zero day threats, or most malware on websites, phishing, advanced malware and Trojans, and so on? Is it any wonder that users continue to download free and purchased antivirus software? Is it any wonder they think themselves secure once it’s installed?
Recently, Symantec officially proclaimed the death of the antivirus through a Wall Street Journal interview. For large manufacturers antiviruses continue to generate a lot of revenue, but the business proposition is no longer acceptable. It is a saturated market, in which top firms compete against cost free alternatives, including Windows Essentials, fight to displace competitors for miniscule changes in enterprise B2B market share, and depend largely on renewals. For such companies the shift to a replacement technology could not have come soon enough. Enter sandboxing and automated malware analysis engines, which overcome many of the shortcomings of the antivirus, including performance and detection of advanced threats.
Involve the user
What such technology does not address, however, is the fundamental need to involve the user in securing their digital identity. Sandboxing may be a solid step forward in detection. But, it is also a toolset which promotes continued reliance on a hackneyed, cat-and-mouse updating model. Similar to antivirus technology, this new technical approach to defeating malware lulls users into the belief that they are supremely protected, even against zero day threats. Sandboxing combined with malware analysis may be big business. However, it may also be, that security technologies which do not engage and motivate users to take an active role in their own defense are of limited benefit.
Excessive attention focused on new, advanced detection and mitigation technologies will likely result in the same blowback of unprepared, ignorant, and vulnerable user populations, as traditional antivirus. We are still the “weakest link”. Sandboxing doesn’t change that. But, times have changed; and like the skin of an expanding balloon our vulnerabilities are spreading out across an ever-widening attack surface: mobile, cloud and social. Systems, applications, and users are becoming increasingly difficult to secure; and global security policies and measures imposed across these surfaces are stretched thin.
Perhaps it is not the technology, but our focus which must shift, from global policies, toolsets, and procedures, to one that leverages the user’s help. After all, we bring our own advanced, mobile computing devices to work; we subscribe to cloud based storage systems, and upload and share company documents; we use professional and personal social networks, and leverage them to the benefit of ourselves and our employers, spin up new systems and servers, for trials, training and our own curiosity. It doesn’t require much imagination to see how our public and private lives have never been so intricately interwoven.
A quick review of some statistics show this intermingling is likely to deepen, that there are business incentives for it to happen, as well as significant business risks. According to Citrix, organizations predict that the percentage of BYO desktops and laptops will grow from 18-25%; Gartner says that by 2017, 50% of businesses will not supply employee computing devices; Deloitte adds that 69% of polled companies experience no technical support problems after implementing BYOD; despite the finding by Acronis that 80% of businesses do not provide education or training on BYOD. In a 2012 survey, commissioned by Check Point, of 768 IT professionals in the US, Canada, UK, Germany and Japan 78% said there were more than twice as many personal devices connecting to corporate networks than there were two years before; and 47% reported that customer data was stored on mobile devices; 90% of which, according to Forbes, are used for email, calendar, shopping, banking and social.
 |
| Source: http://dreamscashtrue.com |
The new digital polis involves a fusion of the private with the public, the personal with the professional, and requires organizations to change their perspective on securing systems, applications, users and other assets. This new view opens unprecedented opportunities to engage with us users (whether we are employees, partners or consumers). Organizations can become protagonists in our active involvement both within and without the workplace to secure ourselves, and thereby protect the enterprise. Currently, few security solutions help in this way. Most strive to do precisely the opposite: to minimize users’ roles in the security process. Rather than encouraging us to secure ourselves, these solutions lead us into taking foolish risks, shortcuts, and workarounds, making erroneous judgments and mistakes. In sum, we end up behaving like the weakest player at the poker table, the mark for all of our adversaries, the fish who, no matter what, always has the weakest hand.