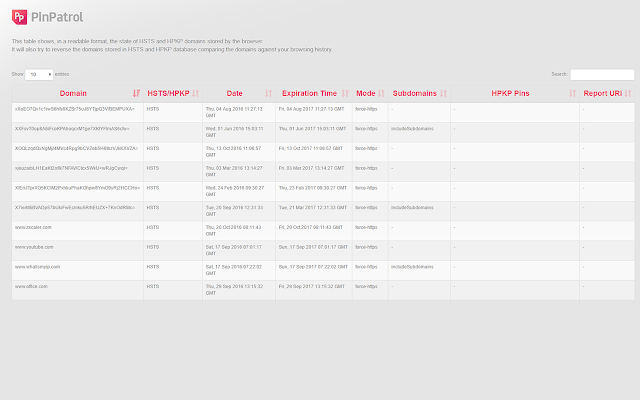
Back in July, we created a new tool for improving the experience using HSTS and HPKP in Firefox. Now it’s time for Chrome. It shows this information in a human readable way. PinPatrol for Chrome is very easy to use and it can provide useful information about the HSTS and HPKP data stored by your browser… or any other. Porting it to Chrome, it has become not just a Chrome extension, but a simple forensic tool for interpreting HPKP and HSTS data from any Chrome’s user.
Back in July, we created a new tool for improving the experience using HSTS and HPKP in Firefox. Now it’s time for Chrome. It shows this information in a human readable way. PinPatrol for Chrome is very easy to use and it can provide useful information about the HSTS and HPKP data stored by your browser… or any other. Porting it to Chrome, it has become not just a Chrome extension, but a simple forensic tool for interpreting HPKP and HSTS data from any Chrome’s user.
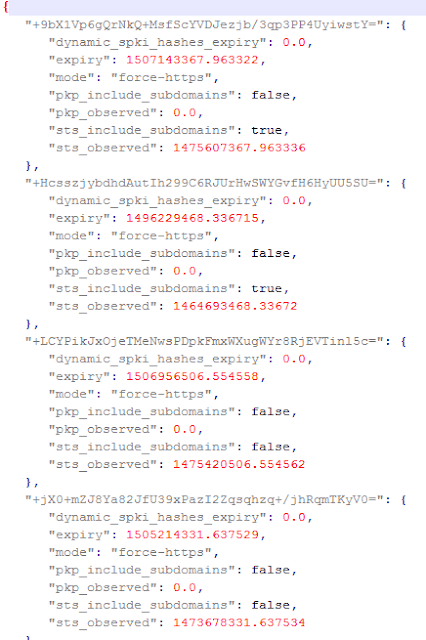
Just as Firefox, Chrome stores HPKP and HSTS information in a clear text file. But their strategies are quite different. The main ones are that:
- Chrome stores the information in a Json file.
- Instead of storing it in cleartext, it hashes the domains in a standard format, so there is some “privacy” for the users.
- It uses report_uri from HPKP protocol (Firefox does not yet).
The way the domains are hashed is documented. An example is here. This is the way a raw Json looks like:
Chrome offers an integrated way (chrome://net-internals/#hsts) to check some HSTS and HPKP values, but definitely it is not the best way to watch your domains.
There is another difference in the way Chrome works. Chrome does not allow extensions to get to your profile files, so you have to drag and drop yourself the file where the information is stored (%localappdata%GoogleChromeUser DataDefaultTransportSecurity in the case of Windows). We can think of this as an advantage to use this extension as a forensic tool.
Another interesting thing the tool tries, is to “un-hash” the domains. If there is a domain in your HSTS and HPKP domains repository, it means you have visited it. So it should be in your History files. What the tool tries is get to your history of domains visited and hash them. If this hash matches with some of the hashes in HSTS/HPKP, the tool “translates” it so it is un-hashed.
 |
| PinPatrol takes history domains visited, hashes and compares them against HSTS and HPKP hashed domains |
But, why are there so many domains that are not un-hashed? Some reasons:
- Your history has been deleted and the domain is not there, but still in the HSTS/HPKP repository.
- Some visits to some domains with HSTS and HPKP are done “in the background” of a webpage, as part of its APIs, advertising system, etc. And these are not stored in the History.
Here is a very short video about how to use the tool.
The tool is available from the official Chrome Extensions Store:
https://chrome.google.com/webstore/detail/pinpatrol/jenmooahjheolakpacikdlloalfaihef/
We hope you find it useful.