HMAC Calculation
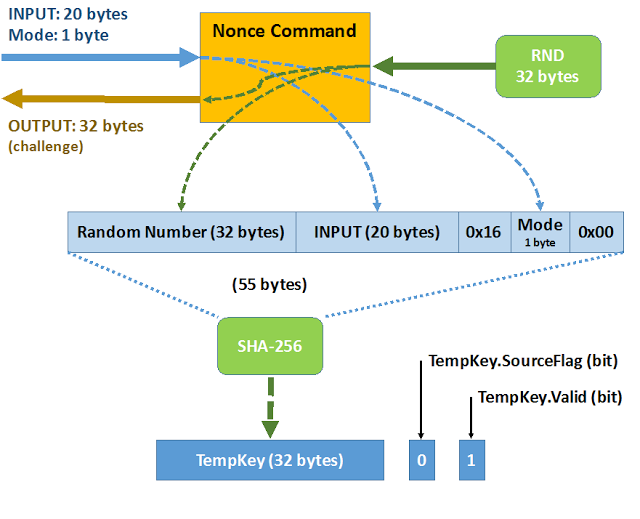
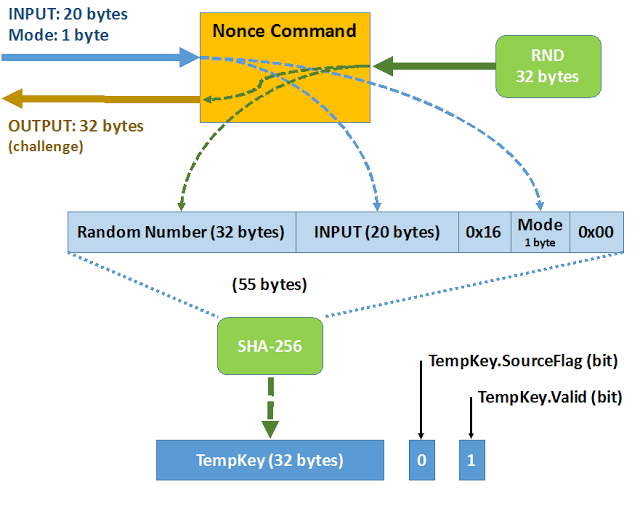
The aim of the Nonce command is to populate the 32-byte internal register, called TempKey, by generating or loading a challenge, which will then be used in later commands.
The Nonce command has three operating modes. 0x00 and 0x01 are the most common modes. In these modes, the Nonce command is invoked, providing it with a number of 20 bytes as an entry, to which it responds by returning a random number of 32 bytes that are generated internally as a challenge.
The 20 received bytes are linked to the random number of 32 bytes, along with three more bytes: 0x16, the mode and 0x00. And based on the set of 55 bytes, the SHA-256 summary, which is stored in the TempKey, is calculated. Additionally, two binary registers are modified:
- TempKey.SourceFlag to 0, meaning random origin.
- TempKey.Valid, to 1, meaning that the TempKey is usable.
In 0x03 mode it is used to directly populate the TempKey, without generating a random number, or the SHA-256 calculation in bypass mode.
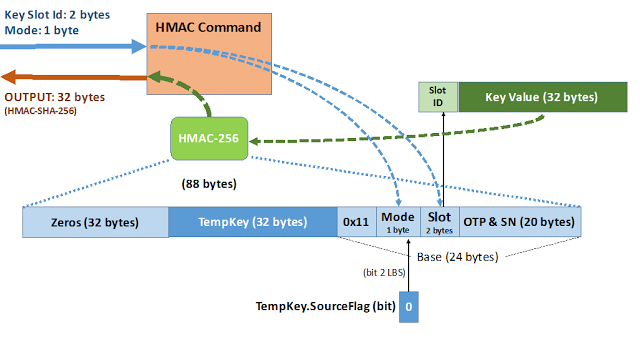
If the Nonce command has finished satisfactorily, setting the TempKey.Valid bit to value 1, it is then possible to invoke the HMAC command.
- Set of 0x00 value 32 bytes.
- Content of 32 bytes from the TempKey.
- Base of 24 bytes determined by the mode of operation.
The HMAC command presents multiple modes of operation, which will determine the content of the OPT zone and the series number (SN) for the device incorporated into the base. It is possible that none of these elements are incorporated, establishing the last 20 bytes of the base at 0x00.
For all communication with the ATSHA204A device, both incoming and outgoing, two CRC cyclical redundancy check bytes will be added to guarantee the integrity of both the command invocation and its response.
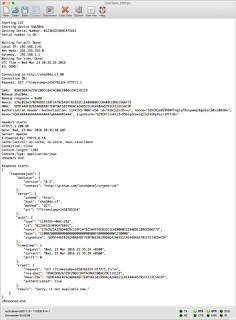
Web PoC
GET /?timestamp=1458647701 HTTP/1.1rn
Authorization: 11PATHS-HMAC-256
id=”EjEjEg==”,
nonce=”LmzzEpRnXvqmvnbOSobGp1VysR/wEpWoMNaY2Miew5g=”, base=”EQACAAAAAAAAAAAAAAAA7gAAAAABIwAA”, signature=”4qnOa5ZGecdzC+DscOSuOhJ64LeB1jTieJATUWPoIZE=”
The web service will be able to verify the authenticity of the IoT device that makes the request, performing the same calculations and comparing the results. To that end, it only needs to know the 32 byte key assigned to the device by its “id”.
“EB0C68BF96E8C26635D3450293D2FC501A63A09924FE90A7BD916AC521FDE0AA“
A simple Script in BASH can be used to test the connection to the web service; this simple script simulates the calculation of the signature the same way as the ATSHA204A would, and makes the web request.
*Related Content:
Cryptographic Security in IoT (I)
Cryptographic Security in IoT (II)