Zscaler describes a more or less typical SMS infostealer Chinese malware. The improvement here is that they use a Word document icon for the Android malware. That would make the user believe that they are not installing anything, but trying to view a simple document. We searched and found some other malware (probably from the same attacker) posing as an Excel document, and got access to the email where the stolen info is sent to.
Some interesting stuff
The samples we have analyzed use an Excel icon. They are slightly different depending on the sample.
 |
 |
|
|
In this samples, the attacker uses an approach different from the one described by Zscaler that seems to be a little bit more advanced. Malware sends SMS history and contact list to the attackers’ email, but in this case, the password for sending the email (and to check it, too) is not directly in the code, but in a configuration file.
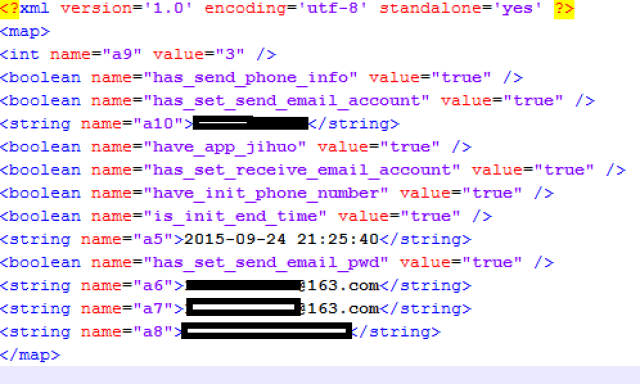 |
| Configuration file for the malware. Password and email included |
We got to get into the mailbox of these mails and confirmed that, indeed, there were real SMS and contacts there. In an account, we found lots of supposed IMSI numbers and the whole SMS collection of the victim.
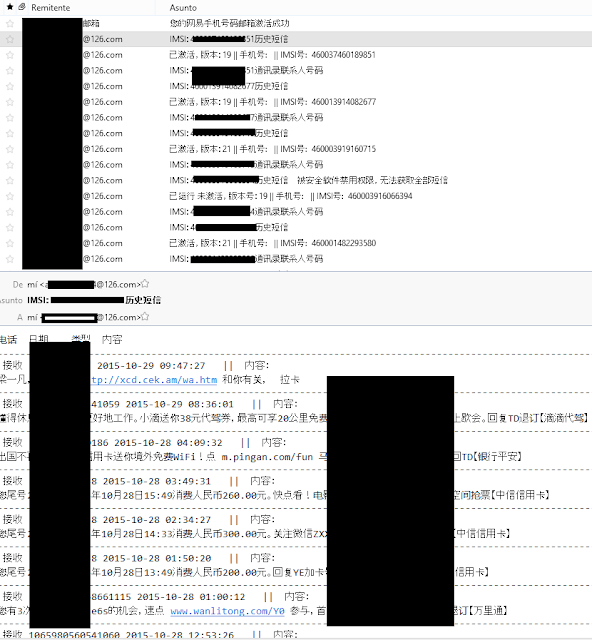 |
| Stolen SMS from the victims |
Zscaler found the “word document” malware was stealing the IMEI, while this one, as can be seen in the image, is identifying the victim by its supposed IMSI. In another account from other sample, we find the contacts list of the victim (name and number).
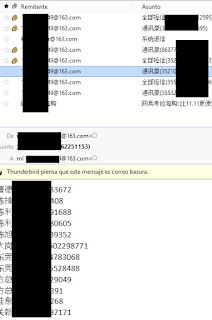 |
| Some of the stolen contacts |
The malware is able to “silent” the phone as well.
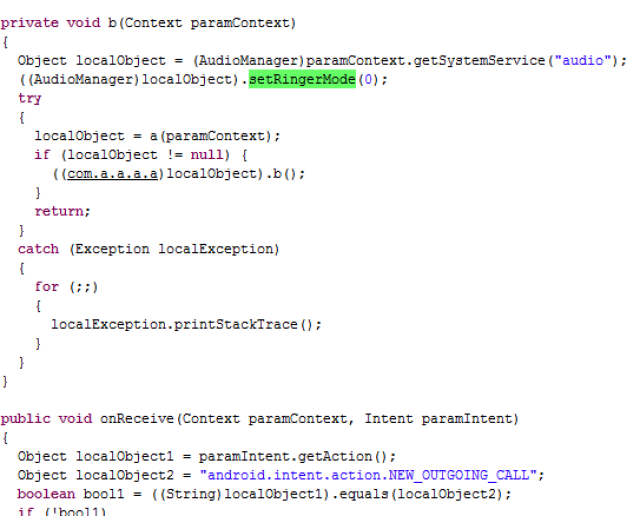 |
| Setting the audio to silence |
As usual, the attacker is a “regular” Google Play developer. He has been uploading apps to Google Play for months, and there are some of them online.
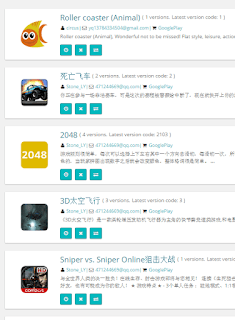 |
| Some apps from the same developer |
Thanks to Tacyt, we can get to know the developer, more than a single app. Most of the apps by this developer are removed, but they are not like this kind of malware described above. SMS stealers would not be able to bypass Google checks. Most of them are clickers, riskware in general or very aggressive adware. One of the few that are still alive is this:
 |
| One of the apps from the same developer still in Google Play. It is not a SMS stealer, but aggresive adware. |
Conclusion
We got to expand and improve the Zscaler research. Same old tricks as used in PC are more and more used in Android again and again, like this “icon decoy” system. It is importan to highlight that this malware has nothing to do with Microsoft, Office, Word or Excel in Android, they just use their icons as something attractive to confuse users.
Juan Manuel Tirado
juanmanual.tirado@11paths.com