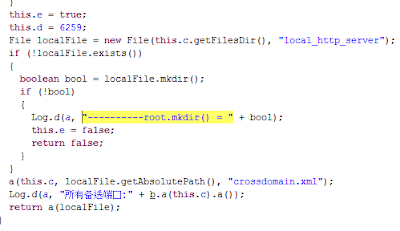
This SDK is called Moplus. Aside its “official features” it sets up a local HTTP server (the well known nanoHttpd), that listens in different ports, depending on the app and SDK version (probably 6259 TCP port). If connected to that port, nothing is served (documentRoot is at data/data/apkNamefileslocal_http_server)… but it allows the attacker to send POST requests with commands.
 |
| Defining the port where the server will listen |
And that is all. Any attacker may send commands to the port via HTTP POST requests with no strong authentication. One of the weakest version only needs the header “remote-addr” to be set to 127.0.0.1. But some others need the referer header to match this.
^http[s]?://[^/]+(.baidu.com|.hao123.com|.hiapk.com|.91.com)(:d+)?(/.*|)$”;
If it works, it will execute the orders and return a JSON with the response (given the right permissions, which most of the spotted apps seem to have).
What commands does it support?
It is very clear with this piece of code:
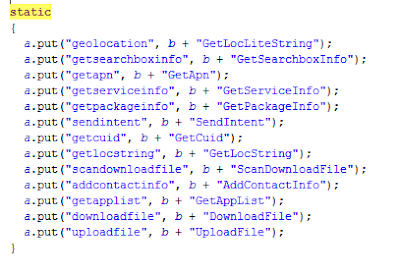 |
| Code with the accepted commands |
It allows downloading files, and uploading anything. From retrieving the lists of apps to inserting new contacts. In rooted devices, any new apk could be installed silently.
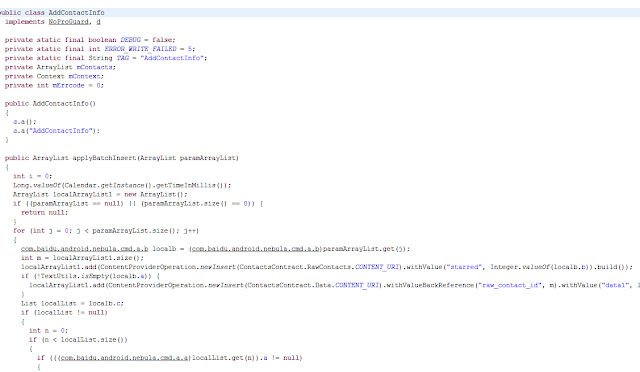 |
| Code to add contacts silently |
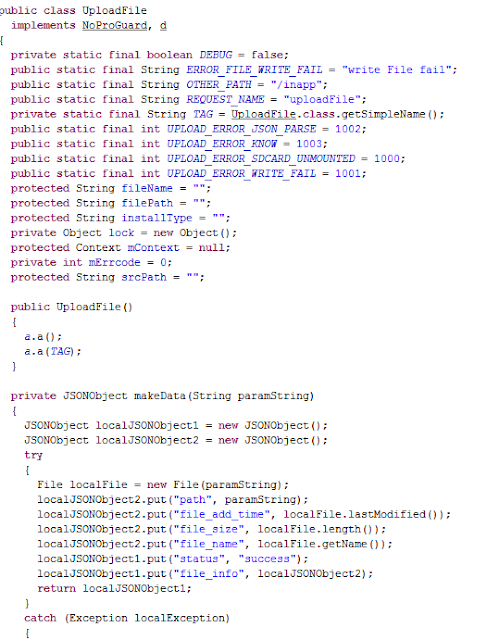 |
| Part of the code to upload files |
Trend Micro contacted Baidu, that has created a new version that removes most of the malicious commands of the list. They are replacing most of the affected apps.
What did we found?
Trend Micro talks about thousands of apps affected. With Tacyt, we found the ones using the SDK and still available in Google Play. Some of them with up to 5 million downloads and not related to Baidu at all.
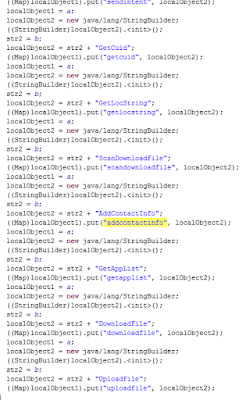 |
| A variation of the code with the commands |
These are some of the packageNames spotted in Google Play (although there will be more, for sure), different from the ones published by Trend Micro (so far):
- com.qiyi.video.market
- com.nd.android.launcher91
- com.ivodani.comicsisland.activity
- com.qyer.android.jinnang
- com.pad.comicsisland.activity
- com.cubic.choosecar
We could not confirm that the commands works the same in all of them. For sure, they contain the offensive code, but maybe with slightly different systems to be able to get in. They should be reversed individually to be sure how to make it work (or if they even work).
One of the easiest that we tested, was the very popular Baidu Maps. Not this one, but a previous version (8.7.0).
In the image, we use this Chrome plugin to inject POST commands. The result (inserting a contact remotelly) is shown. As you can see, Baidu Maps icon is on the top.
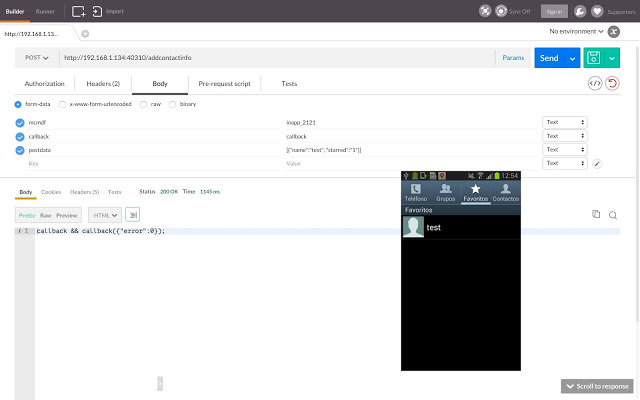 |
| Adding contacts with a POST |
It is worth mentioning that, many of the spotted apks, rely on two different classes.dex files. This means that, once executed, the app may load classes2.dex from its own “main” code, and usually this classes2.dex is the one with the offensive code.
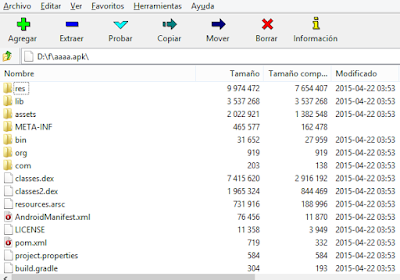 |
| An app containing a second “dex” file |
This is not new. Many malware/adware in Google Play use this trick to try to fool detections. They may download the .dex file from elsewhere, or hold it inside. It is quite interesting finding that, some of the apps were using the “Moplus SDK capabilities” in this second dex file.
Aside, one of the most interesting point is that Mobo Launcher, related to the well known Mobogenie market, counts with this code backdoor as well, and it is very popular even outside China. It has been in Google Play since late 2014. In fact, is the oldest in Google Play with this version of the backdoor, as far as we know.
 |
| Some of the detected apps in Tacyt |
Although we could not get to make it work and actually send a command (not sure why), the nanoHttp service was up, and code to receive commands is there… so there are strongs reasons not to trust this app, and reverse it even deeper to know exactly what is happening and how it works.
Of course, there are a lot of APKS outside Google Play (aptoide, mobogenie…) with this backdoor as well.
The good part is that most of these programs are already detected by several antiviruses, not all of them because of this, but detected, anyway.
Juan Manuel Tirado
[email protected]