Several kind of RATs for Android exist. There are two basic conditions that defines an RAT:
- What and how it is able to control the infected device.
- How the victim receives the commands.
How the victim receives the commands opens a handful of possibilities: HTTP, SMS, jabber protocol, GCM (Google Cloud Messaging)… and now Baidu Cloud Push notifications. Cloud Push is a system where developers can register users. Registered users will receive push notifications in their devices (an special notification in the task bar). This is used in millions of legitimate apps, and Google allows the use of its GCM for free. This system has been abused to push ads in the past. Any developer may create his own CGM, and Baidu has a popular one in China. This time it has been abused to push commands to this botnet. This technique is quite new. So new, the malware has not been detected by antiviruses for months.
What does the RAT do?
It infects the system so is waiting for commands from the Command and Control server, which is a specially crafted Baidu Cloud Push instance. Basically, this picture below summarizes it all.
 |
| Commands that the attacker may send to the device |
It shows the commands the device may get from Baidu. The app counts with every necessary permission to perform the tasks, so the infected user is completely at the attackers disposition.
All the information goes through “/mnt/sdcard/DCIM/Camera/%file_name%” before being uploaded to the Baidu cloud storage (BCS) and removed from the device.
But… this has not only been in alternative markets
Stefanko found the samples in alternative markets, which is, in a way, “expected”. But some of these samples were indeed in Google Play… for more than a month. With more than 50.000 downloads, the victims may still be under the control of the attacker.
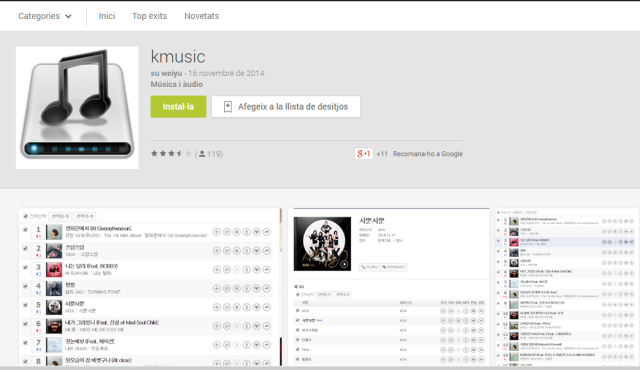 |
| One of the RATs, available in Google Play |
Thanks to Tacyt (although we did not found these samples on time…) we now know that some different samples with the same behavior were available in Google Play from, at least, November 2014. Some samples, under a certain developer, were signed during November 2014, and were available in Google Play since December. The apps were available in the main market until late January, when Google removed them. It seems that some others were available from September until late January as well, under some other fake account. These apps are still in lots of other markets.The developer seems to be from South Korea.
He has been using different names and emails: “zhengcaiai”, “devzhemin520”, “su weiyu”… This domain belongs to the attacker as well: http://devzhemin.dothome.co.kr.
What about antiviruses?
The samples were not detected about five months ago, when it all started.
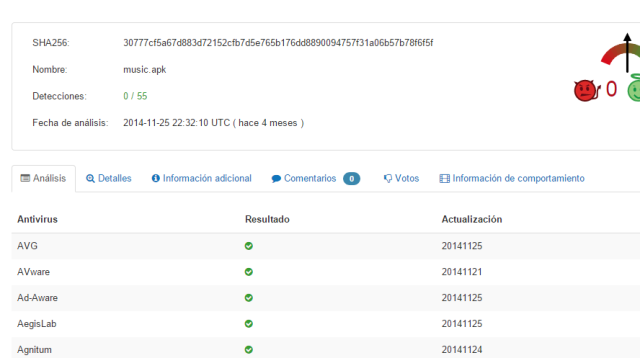 |
| One of the RATs not being detected |
Until March 17th approximately, it was fully undetected. ESET and Avira have been the first ones detecting them.
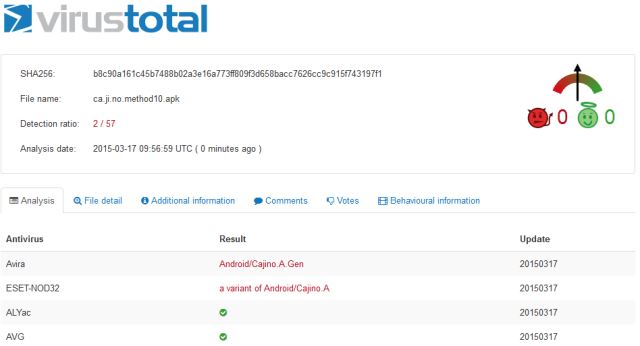 |
| Some of the first engines detecting the samples |
A few days later, some others have created a signature, but still not all the big players.
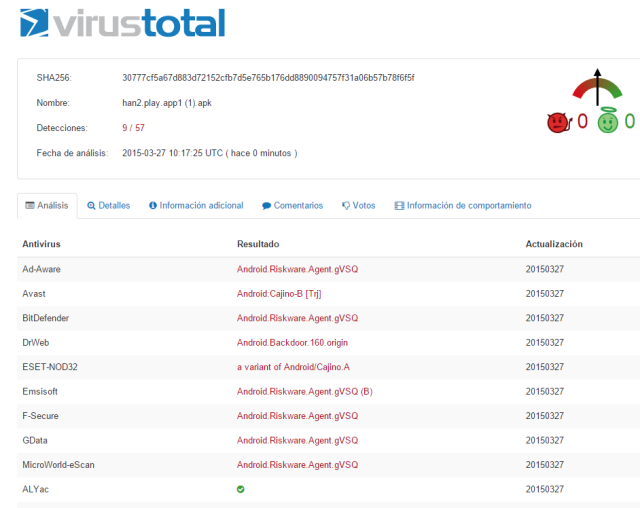 |
| Some more engines detect the samples |
They have named it “cajino” RAT because of the packageName that Stefanko found. They all started with ca.ji.no.method[*] and a number. But the attacker has also used han[*].play.app structure for naming the apps in Google Play.
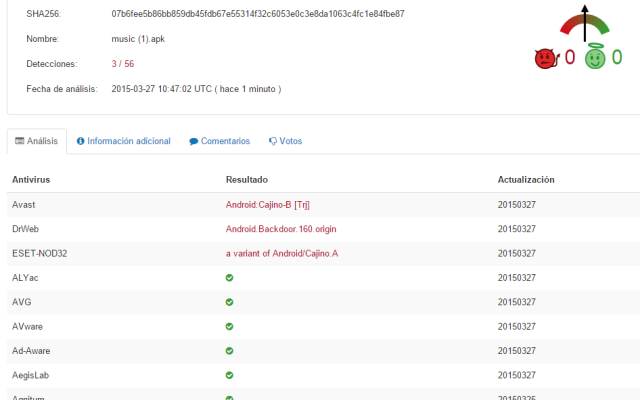 |
| Newer versions are less detected |
For newer versions, the only ones catching them are Avast, DrWeb and ESET, the ones that created the original signatures. This perfectly shows the notion of “quality signatures” that protects the user from future versions as much as possible.
Conclusions
RATs are not “rare” in Android world, but they are not usual, either. Aside from the conclusions of the ESET researcher, the important issues to point out here are:
- New methods to communicate have been used.
- Apps have been undetected for researches/antiviruses for almost six months.
- The attacker has been in Google Play (best place ever for attackers) for more than a month.
- And it will still get more victims, because the app is still in a lot of different markets.
Is not usual to have “RATs” in Google Play. One of the last news were the detection of Dendroid, a RAT system designed to evade Google Play filters, a year ago.
Some different hashes (aside from the ones ESET found) are:
- 7a131e44d731995e51b7e439082273abbbf02602
- 48412835d0855c565f213242b0db7a26480fcc2e
- 4c9e505f1132528c68091fa32bb1844d7cbd2687
- 31a645973554b7c83cc0bd6fb7709ec12937c962
The attacker is distributing (aside from other markets) the apk from here: hxxp://guangzhouhan1.dothome.co.kr/music.apk, so it may change in any minute.