The fact that Social Engineering has been the easiest method used by the scammers is not new. What we are going to describe in this blog today has been mentioned in some relevant Security reviews and newspapers, but at Elevenpaths, we are still surprised how easy this is happening.
A few months ago, our customers in the Middle East asked us how to overcome the so-called C-level scam (or Business E-Mail Scams as baptised by the FBI or also known as the “Fake President” fraud).
For the most basic scam, the “bad guy” should need to know the following information:
- If a company (let’s call it acme.com) is going through a merger or it has in mind acquiring a company (information obtained over the news, twitter comment insight, general gossip …). Let’s call this company Muntaleyxp.
- C-level members and associated domains of the company (not mandatory). Let’s assume [email protected].
- Financial controllers or under C-level people in the company. Information can be gathered through Linkedin for example. Let’s assume [email protected].
- If the merger or acquisition process is done through a third company, find out one of the most relevant person in this company (let’s call it Kmiop). Let’s assume [email protected].
With this information the scam occurs as described below:
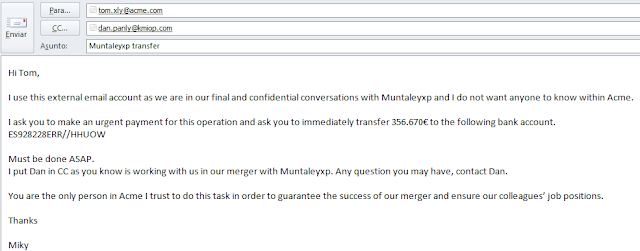
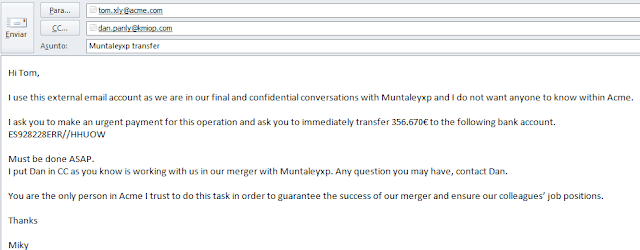
- If the scammer has accessed Miky’s email account though a Trojan for example, it is even easier. But let’s assume it is not the case. If the domain of the company has a letter you can trick such an “l” or “m” … then register a new domain and use it to send the main email. If not, then he/she can use a Gmail account. For example: [email protected]. [email protected].
- Send the email to [email protected] and put [email protected] in CC (it can even be the real domain but ensuring Dan does not receive the email [misspell it] avoiding he will trigger the alarm and hoping Tom will not contact Dan).
- Many variants can be used (such as Dan is also part of the scam [this time do not misspell it] and he will provide the bank account details) to perform the scam, but the general idea is there. The receiver (Tom) will be surprised with such message that he may act and do the transfer!
From Elevenpaths we have five suggestions to overcome this problem:
-
Easiest and obvious one: Pick up the phone and ask the C-Level executive about his/her e-mail.
-
A technical one with its limitations: Try to set-up incoming email rules trying to cover as many misspelling options with C-Level executive names & surnames (with any associated domain), and blocking them. C-Level executive: Miky Wunderbalr (authorised e-mail: [email protected]). niky.wunderbalr, miky.wunderba1r, miky_wunderbalr, miky-wunderbalr, wunderbalr.niky. Along with an e-mail filtering system against identity theft in the Company (acme) properly configured with its associated SPF, DKIM y DMARC registers.
-
A second technical option related to a second/simultaneous factor of authentication: Our Latch product will provide the same concept we used to watch in those Hollywood movies such as Crimson Tide (with Denzel Washington and Gene Hackman) where two keys are needed from different people in order to launch a missile. If we assume “the missile” is the bank transfer itself, then Tom can authorise the transfer and Miky, with his latched account active is also required to do the transfer. Miky will ensure that his latched account is never active during “strange” hours.
-
The costly one: Have a “powerful” cybersecurity insurance covering social Engineering attacks.
-
Any C-level manager should avoid sharing any news about possible company merger or acquisitions.
Just remember: The weakest link is always us!