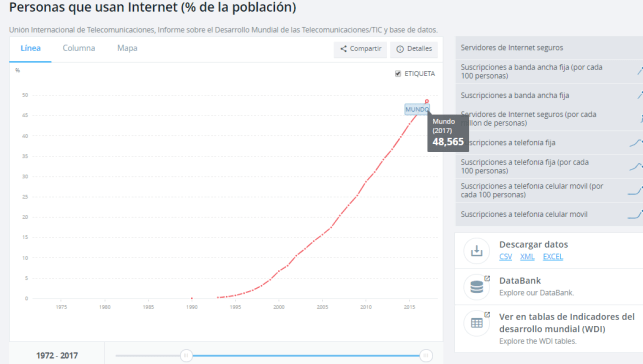
New privilege escalation flaw in Linux
Security researchers at Qualys have discovered seven flaws in Canonical’s Snap software packaging and deployment system used in operating systems that use the Linux kernel. The most severe of these vulnerabilities, listed as CVE-2021-44731 and reportedly receiving a CVSSv3 of 7.8, is a privilege escalation flaw in the snap-confine function, used internally by the snapd tool to build the execution environment for snap applications. Successful exploitation could allow any unprivileged user to gain root privileges on the vulnerable host. The flaw was communicated to vendors and open-source distributions as soon as it was discovered last October, leading to a coordinated patch release process on 17 February. Qualys technicians have also developed an exploit for this issue that allows full root privileges to be obtained on default Ubuntu installations. The other six vulnerabilities identified are: CVE-2021-3995, CVE-2021-3996, CVE-2021-3997, CVE-2021-3998, CVE-2021-3999, CVE-2021-44730.
Conti ransomware operators take over TrickBot operations
Researchers at Advanced Intelligence have published a report indicating that the TrickBot malware has transferred its management to the Conti ransomware operators. AdvIntel’s experts have analysed the background of TrickBot, noting a historically close relationship with the ransomware and its subsequent rise to prominence. Conti has relied, among other factors, on maintaining a code of conduct among its operators, which has allowed it to thrive and remain active in the face of other ransomware groups that have been dismantled by various law enforcement operations. Experts suggest that TrickBot gradually became a subsidiary of Conti’s operators, as they were the only ones to use it in their operations. Also, by the end of 2021, Conti finally absorbed multiple TrickBot developers and operators. However, it is worth noting that since TrickBot’s networks are reportedly being easily detected, Conti operators have begun to replace it with the BazarBackDoor malware, which is under its development and is used to gain initial access to its victims’ networks.
Cobalt Strike distributed on vulnerable MS-SQL servers
Analysts at ASEC have discovered a new campaign where vulnerable Microsoft SQL (MS-SQL) servers that are exposed to the internet are being attacked by malicious actors with the goal of distributing Cobalt Strike on compromised hosts. The attacks targeting MS-SQL servers include attacks on the environment where the vulnerability has not been patched, brute-force attacks and dictionary attacks against mismanaged servers. First, the malicious actor scans port 1433 to check if MS-SQL servers are open to the public, and then carries out brute-force or dictionary attacks against the administrator account to try to log in. Different malware such as Lemon Duck allow scanning of this port and propagate in order to move laterally in the internal network. The attacks culminate in the decryption of the Cobalt Strike executable, followed by its injection into the legitimate Microsoft Build Engine (MSBuild) process, which has been exploited in the past by malicious actors to deploy remote access trojans and credential-stealing malware. Finally, it is worth noting that the version of Cobalt Strike running on MSBuild.exe comes with additional settings to evade detection by security software.
All the details: https://asec.ahnlab.com/en/31811/