Gartner has released a study that classifies the most important companies that offer Data Loss Prevention (DLP) solutions depending on their position, strategy, effectiveness, and market leadership. We have made a little experiment to test if these same companies control metadata leaks in their own services, as a potential sensible data leak point.
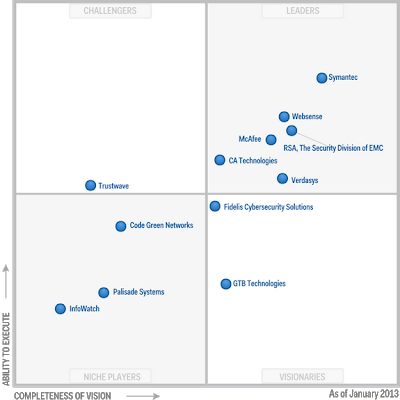
According to the “Magic Quadrant for Content-Aware Data LossPrevention” research made by Gartner in 2014 over 50% of companies will use some kind of DLP-solution to keep their private data safe but only 30% will use a content based solution.
This study made by Gartner determines which are the leader companies when preventing leaking information, establishing as measurement factors to generate leadership indicators as: provided content-aware DLP solutions, DLP-Lite products offered or if they provide a DLP channel to the user so he can clarify doubts about compliments, for instance.
 |
| Data Loss Prevention leading companies, by Gartner |
Do these companies avoid information loss through metadata in their systems? We conducted an analysis of the main web pages of these aforementioned companies that were included in Gartner’s study using MetaShieldForensics. Metashield automatically downloaded and analyzed every document exposed on the corporative webs of the companies.
The following table displays the results. Every single company leaks metadata associated to their public documents that are being exposed on the Internet. Seemingly these documents are not being cleaned and are thereforea potential private information leaking point that is to be taken into account.
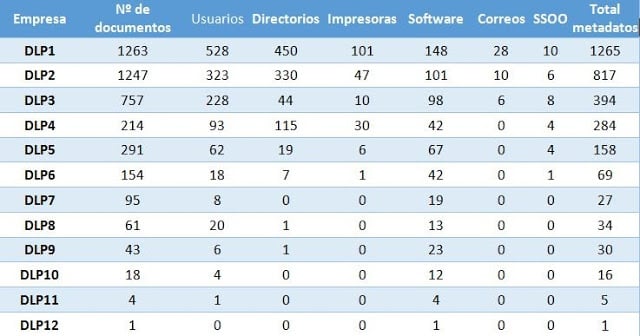 |
|
|
Based on this information we proceded to graph the data showing the amount of information being leaked by the studied DLP companies. Logically the companies that most suffer of information leaks also have more publicly available documents in their web pages.
 |
|
Information leakage exposed by companies that provide DLP tools and services
|
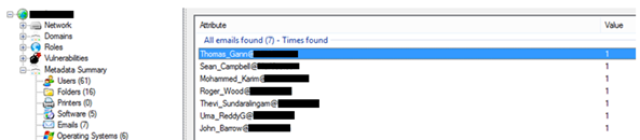
Names or account names followed by internal directories where the documents were created are the most commonly leaked pieces of information. Another usual leak is the the software version being used when generating the document. This group of information is valuable for a potential attack.
Let’s see some details about the leaked information:
- Users and user accounts: The internal usernames and their mail accounts are very noteworthy. This information can help the attacker to forge a more complex and sophisticated attack.
- Paths to internal web services: Some of these provide valuable information about the internal network. For example, one of the documents contained an URL that points to an OpenNMS portal (http://159.36.2.25:8980/opennms/event/…/). OpenNMS is offered by Symantec as a solution for network administrators for controlling critical services in remote machines.
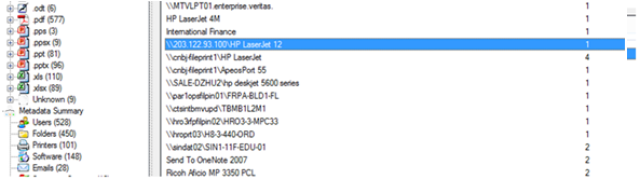
- Internal user directories: The most common directories that are found contain user information in default paths such as “Desktop, My documents…”. For example, “C:Documents and Settingsholly_waggonerM20Documents****** Webpress2004” was detected in one of the DLP companies.
-
Network printers: This is also a very common leak. Network printers that expose information about their exact model and the server they’re associated with (either name or internal IP address).
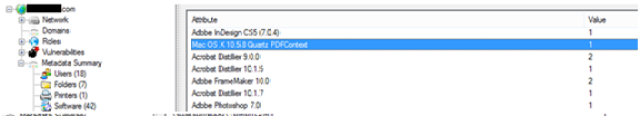
- Software used by the company:It is very common to leak the software being used by the company for generating a document. The most common piece of information refers to PDF documents which are very popular for publications.
- Other metadata that exposes private information: A rather unusual but curious case is custom metadata generated in some documents which can result in a much more relevant leak than one can think at first sight. For example, properties like the subject of a specific email, an attachment or to whom it was sent can expose clues and evidence of internal business strategies like relations between companies or workers.
Conclusions
Metadata may still be widely unregarded when controlling information flow exposed on corporative webpages or simply sharing documents..
Information leak can happen at very different levels and in different ways. Document loss, non-controlled publication and non-intentioned document exposing is indeed a clear example of a problem to be avoided, however document metadata can’t be despised either, specially by a company that offers data loss prevention solutions.
Metadata and information leak shall not be regarded as a singular incident that only provides an attacker a document, an email or sensitive data. It’s also a process that a determined attacker will invest his time into. Depending on the implemented solutions and how protected the company is the attacker will gather all possible information taking advantage of every single leak (as inconsequential as they may seem) for getting to know his target and forging an attack.
The companies that offer solutions against information loss should take it into account in their own products. For example, erasing of metadata is a compulsory task for the Civil Service according to the “Esquema Nacional de Seguridad” (National Security Scheme) and LOPD. MetaShield Protector is a solution that some of them chosed.
Rubén Alonso Cebrián
ruben.alonso@11paths.com