Now, it’s happening again: There are numerous reports in the media about HummingBad, Hummer, and Shedun Reloaded. Do them belong to the same malware family? It all depends which lab is doing the analysis. Three different families or not?
HummingBad
In February, Check Point alerted the market about HummingBad. It followed the same “rules” established by the Brain Test family, which means it introduces a rootkit on the phone, is almost impossible to remove, and installs fraudulent apps automatically. But it was stunningly more sophisticated. It was installed by drive-by-downloads, its content was encrypted, and it used several redundancy methods to ensure infection (including automatic and, if not possible, social engineering). Some of the infrastructure used as a C&C was hxxp://manage.hummerlauncher.com domain, hxxp://cdn.sh-jxzx.com/z/u/apk, hxxp://fget.guangbom.com and hxxp://d2b7xycc4g1w1e.cloudfront.net. And it gets worse. In early July, Check Point researchers attributed HummingBad to a “legitimate” advertising company called Yingmob, responsible as well for the iOS malware called Yispecter that took advantage of its enterprise certificate to install itself and was discovered in late 2015.
Hummer
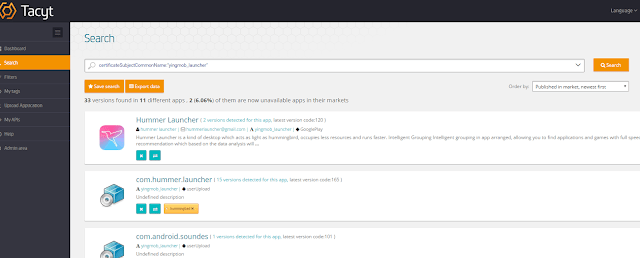
Also in July, Cheetah Mobile wrote about a malware it called Hummer, a new threat different from GhostPush (its own name for Shedun, Kemoge, BrainTest, etc). Although Cheetah Mobile does not explicitly says so, Hummer is HummingBad, as we can easily confirm with Tacyt because, for example, it uses the same infrastructure and rooting file called right_core.apk, which is sometimes embedded and sometimes downloaded.
 |
| A HummingBad/Hummer sample with some of the singular URLs used |
Shedun?
Lookout thinks differently. They claim HummingBad, or Hummer, is the same as Shedun, discovered in November 2015. It maintains Shedun is closely related to the BrainTest/GhostPush family, but it only describes the HummingBad malware as “not new” without any further technical details.
So, is this HummingBad/Shedun an evolution from the same cybercriminal group we connected in our previous report, or does it come from a different group? Let’s take a look.
Our analysis
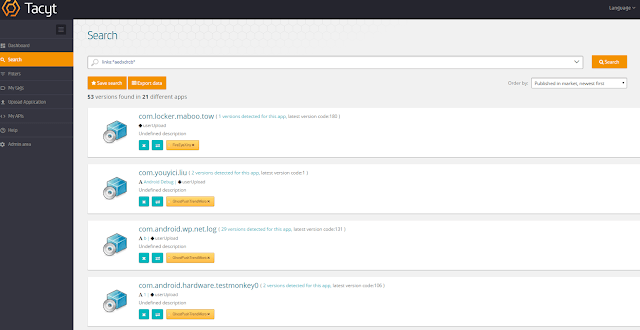
HummingBad, or Hummer, comes from a “legitimate” adware company called Yingmob which, for a while, had its “Hummer Launcher” app on Google Play. Google eventually removed the app in May 2015.
 |
| Hummer Launcher signed with the same certificate as some HummingBad samples |
As we determined using Tacyt, even the aggressive payloads are signed with the same certificate.
From our previous report in October, we saw some very specific behaviors that associated all the malware families. For example, the use of a few particular domains and the presence of some files inside the APK like “sys_channel.ng”.
 |
| One of the particular domains shared by several samples analyzed in October |
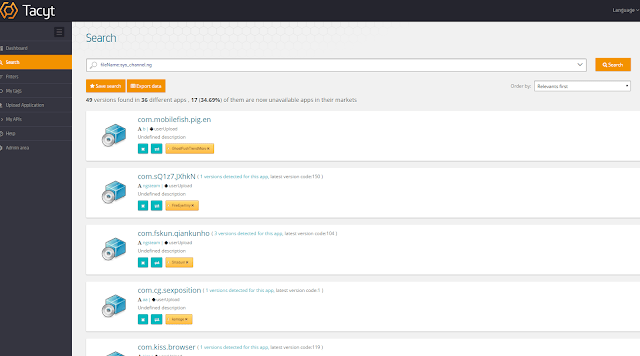 |
| One of the particular file names shared by several samples analyzed in October |
Our analyst team used Tacyt to conclude that there is strong evidence suggesting a relationship between several different reports from different security companies, and confirmed that some of the aggressive apps discovered were on Google Play in early 2015. The evidences suggested that these supposed different families of malware, may be just the same Chinese cybercriminals (because of using the infrastructure, domains, topics, files, etc.) evolving the same idea about serving aggressive ads, rooting the devices, sending commands and installing new packages.
We came to this conclusion because of several similarities that relate the families: domains, dates, permissions, names, certificates, resources, etc. The Chinese group started their activities maybe in late 2014, using the OPDA “brand” and trying to introduce malware on Google Play as well as legitimate apps. Later, they evolved new techniques, from Xinyinhe adware, which seems to be just a variant of Ghost Push, Brain Test to Kemoge, all technically related in some way.
What about HummingBad?
Checking HummingBad’s singularities we determined that it uses a completely different infrastructure with little in common with our previous findings, even though it follows the same philosophy of rooting the device and silently installing apps. We can find no evidence about certificates, files, or any other hint that helped us to tie both families together as we did before. Of course, we may have not found them. For example, HummingBad uses mainly these domains: guangbom.com, hummerlauncher.com, hmapi.com, cscs100.com… They are not shared with previous Chinese families, except hmapi.com, which seems common place for adware and malware. All apps containing this particular domain on Google Play are eventually removed
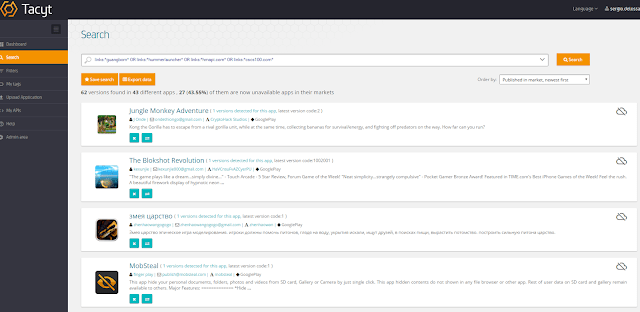 |
| hmapi.com shared between several different aggresive adware or malware samples eventually removed |
As another example, HummingBad uses right_core.apk as a payload, which is either downloaded or embedded.
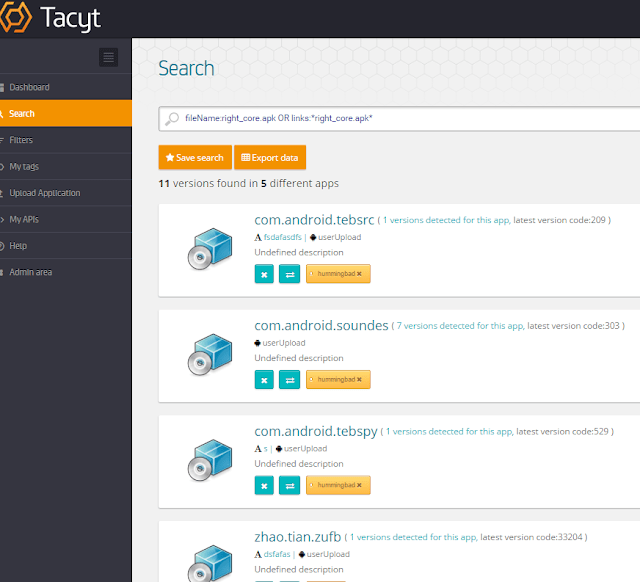 |
| Searching for samples using a specific file downloaded or embedded |
With HummingBad we can only go back to early 2015 with “legitimate” adware samples. With the BrainTest family we can go back to 2014.
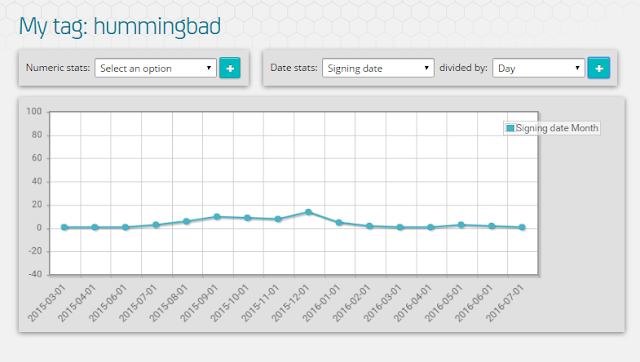 |
|
| Signing date for all the samples we have labeled by our analysts as HummingBad |
Another point of interest is that it appears that Brain Test was not very interested in tracking their ads with UMENG (the popular Chinese platform), while HummingBad seems to use UMENG in many more samples. The keys do not match in any case.
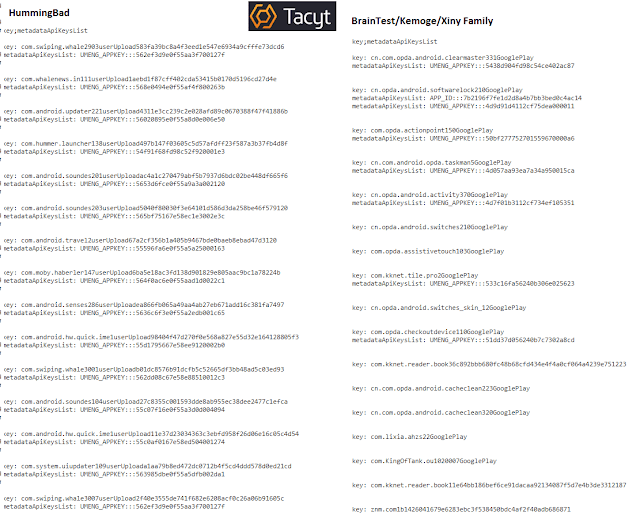 |
| Comparing keys between families |
Philosophy matches but the code, infrastructure, and “history” do not
Shedun and HummingBad seem to operate from the roots of “legitimate” Chinese companies (OPDA and Yingmob), and they may be related in other ways, but the owners, resources and developers appear different. So we can conclude a couple of insights:
- HummingBad is Hummer, but it does not seem to be Shedun/GhostPush/Brain Test itself.
- This is important, because it would mean cybercriminals are learning from each other. It is not just the same group evolving its own product. That is a scary since they will most likely improve technically to gain market share when they have “competitors”.
Attribution is always a risky exercise for every researcher (including us), but we believe HummingBad is not an evolution but is instead another new, dangerous rooting malware that was developed alongside previous malwares (just as there are different ransomware or banking Trojan families with the exact same philosophy). And we also think this malware it here to claim its market share and stay for a while.