 It is hard to say something new about Wannacry, (the ransomware itself, not the attack). But it is worth investigating how the attacker worked during last hours before the attack. It does not let us uncover the creator, but for sure makes him a little “more human”, opens up a question about his mother language, location and last hours creating the attack.
It is hard to say something new about Wannacry, (the ransomware itself, not the attack). But it is worth investigating how the attacker worked during last hours before the attack. It does not let us uncover the creator, but for sure makes him a little “more human”, opens up a question about his mother language, location and last hours creating the attack.
Wannacry (the ransomware again, not the attack) is a very easy to reverse malware. No obfuscation, no anti-debugging, not a single mechanism to make life harder for reversers. Aside from the code, some companies have even tried linguistic analysis (it has been widely used recently) to try to know where the author comes from (although it turns out to be from China, “more than often”). Result is usually “maybe English native speaker, maybe not, maybe native Chinese trying to mislead analysis…” who knows. But one thing we may know for sure: he likes football, is not greedy and usually types in Korean language.
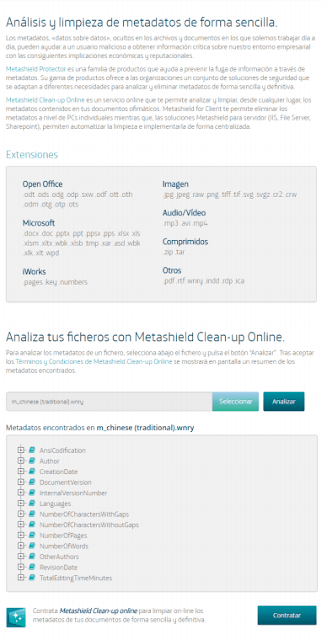
Metadata to the rescue
It has been proved, during recent years, how useful is to analyze and extract metadata and hidden information from files. Data is the new oil.
Not only sensitive information about the user or organization, software, emails, paths… but others like dates, titles, geopositioning, etc. We have heard about spying, politics scandals because of altered documents, insurance frauds…, and everything revealed thanks to metadata.
 |
| https://metashieldclean-up.elevenpaths.com |
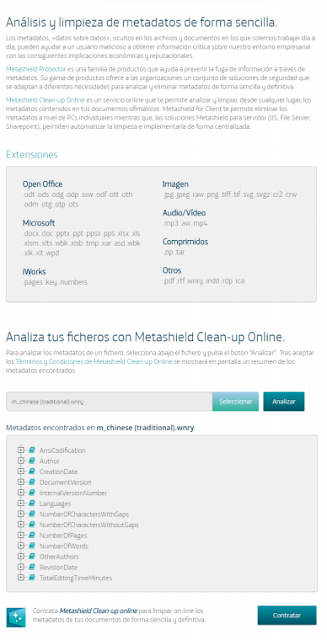
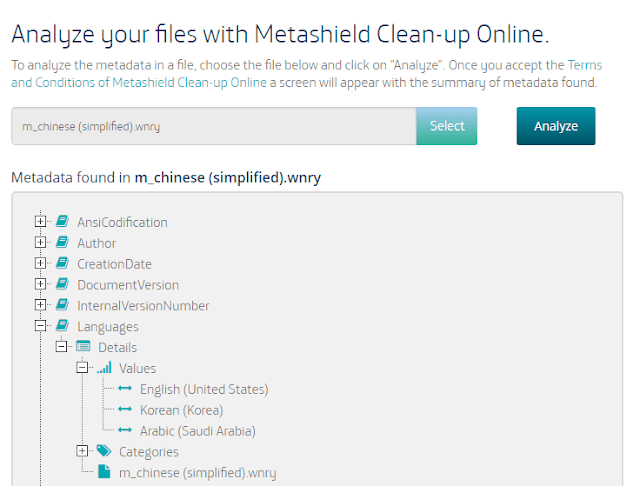
Wannacry 2.0 uses some text files with the instructions to show in a textbox. At first sight, extension WNRY does not mean anything, but they actually are RTF files. And that gives some space to work with metadata. From this analysis using our new tool Metashield Clean-up Online, we could find “Messi” as a user in the system, and, more interestingly, languages, dates and editing times. About Messi, we discovered that some user already mentioned it a few days ago. But let’s go further.
 |
| This is version 1.0, less known that its own evolution |
There was a Wannacry 1.0 version, around March. It only contained a
language file, m.wry, that was a RTF and was available only in English. This file was created 2017/03/04 at 13:33:00, and modified for 2.6 hours until 17:37:00. These are local timezones, wherever in the world the attacker was. The Internal Version Number was 32775. This is a number that Word (or any other RTF creator, although Word specifically uses 5 digits) adds when a RTF file is created, but is not officially properly documented by Microsoft and seems to be unique. But this Wannacry version was unnoticed in a world full of ransomwares. Then Wannacry 2.0 and a wormable attack came through. This was a slightly improved version, with lots of different languages, aside from English. What about their metadata?
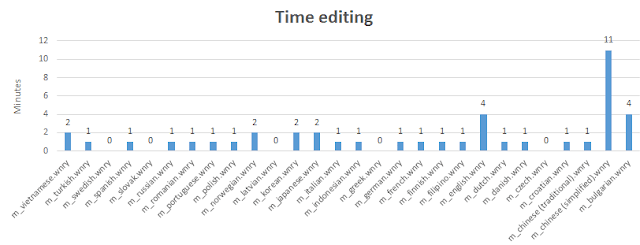
It is at least very interesting to know that the attacker created (in his harddisk, at least, maybe copying it from somewhere else) all the documents between 13:52 and 13:57, just a day before the attack (11/05/2017). Again, this is local time wherever part of the world he was. He opened English file first, at 14:42.
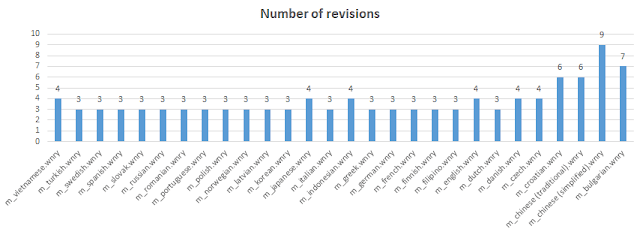
After that, most of the others files were sequentially created (or again, dumped from some zip file or disk) until 15:00. Chinese (traditional) and Chinese (simplified) where the last ones, opened almost 4 hours later, at 18:55. He spent 11 minutes editing the simplified version, but just one minute with traditional. Prior to that, he spent 4 minutes editing English file. Japanese and Vietnamese took him 4 minutes of editing as well. Vietnamese was the last file to open from the first round, maybe because files where alphabetically sorted. It did not even edit Swedish, Latvian, Czech or Greek language files.
Author field for RTF files was set to the word “Messi”, as in WannaCry version 1.0. That means, that is the user name is configured in its Office Word version and probably his Windows user too. He may like football. Internal Version Number was again 32775 which may mean he reused the template.
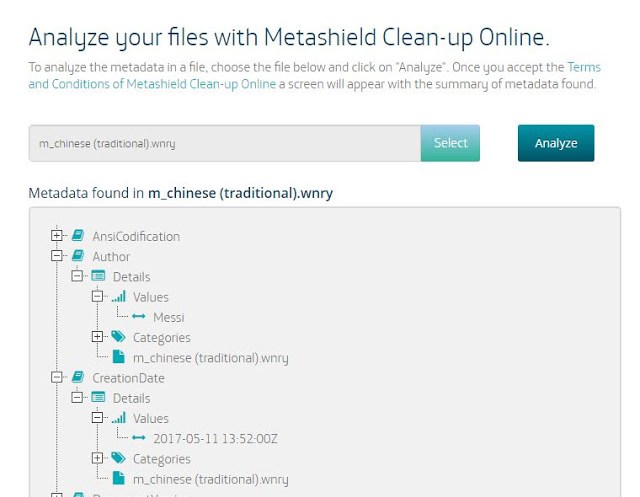 |
| Metashield Clean-up Online |
A very insteresting metadata is language.
All the files, no matter the language they are written in, uses English, Korean and Arabic as metadata “Language”. These are the language that Word expects you to write in, and are filtered trhough Word to RTF files. Why this three? Does he uses all of them? No.
- Arabic is present if you have a specific version of Word (deflangfe is the keyword for “Default language ID for Asian versions of Word“.) It does not mean this language is configured as predeterminded in Word for corrections. It means you use a specific kind of EMEA version of Word, very common. You can tell if your RTF files have adeflang1025 in them.
- Korean is the language in deflang which defines the default language used in the document used with a plain control word. That means, he has Korean and English as default “usual” languages in Word
- English is present because of how Word works. If you set your Word with Korean as deafult language, it will always be set with English as well. Seems like a Word feature.
This is the raw data “inside” the RTF.
rtf1adeflang1025ansiansicpg1252uc2adeff31507deff0stshfdbch31505stshfloch31506stshfhich31506stshfbi0deflang1033deflangfe1042
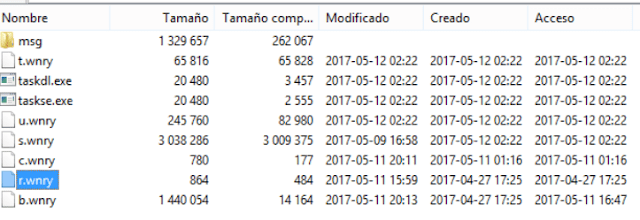
An interesting point is that he uses a zip file that contains the Wannacry ransomware (again, the ransomware itself, not the tool) to inject into the wormable system. This is (in version 2.0 and some versions 1.0) a password protected file (1.0 was wcry@2016, and 2.0 WNcry@2ol7). As we know, from our previous research with Gmtcheck for Android, zip files store the Last Access Time, and Create Date from the (supposed) NTFS filesystem of the attacker, with his own timezone applied. So, the dates in a zip file, are the dates in the attacker timezone. It means that, analyzing the zip, we could deduce the following:
- 2017-04-27 17:25 (attacker local time): The attacker created b.wnry, a BMP for the desktop background and r.wnry, which contains the readme file.
- 2017-05-09 16:57: The attacker creates another zip with tools to connect to Tor Network (and negotiate the ransom). They were downloaded in the attacker filesystem 16:57, 09/05/2017, attacker’s local time. They were zipped and introduced in a new zip as s.wnry.
- 2017-05-10 01:16: The attacker creates in his system c.wnry, which contains onion domains and a wallet.
- 2017-05-11 15:59: Creates r.wnry that contains remove instructions.
- 2017-05-11 16:47: Edits b.wnry.
- 2017-05-11 20:11: Edits c.wnry again.
- 2017-05-11 20:13: Adds b.wnry in the zip and starts its creation (with password).
- 2017-05-12 02:22: Adds the exe files: u.wnry and t.wnry. The attacker zips and sets the password. The payload of the worm is ready. This is a “magic” hour as it is stablished as the time of infection in every affected (infected) system.
Even servers, because is the time stored in the zip file, and when the malware extract its own files, this same value goes with it. That is why this value of “last time accessed” is in every affected system, because it comes directly from the unzipping action that the worm makes.
 |
| A random Windows server affected. The same time and date. |
Since we have no UTC reference, we may create this table. Each line represents a hypothesis: Let us suppose the local time the zip is created (12/05/2017 2:22), occurs in all possible and different GMT timezones. We have added some “facts” that we know happened for sure in a specific UTC time. For example:
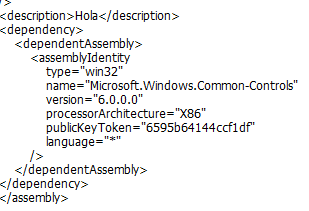
So, let us imagine. If the attacker was in UTC+9 (Korea), as they say, that would be 11/05 17:22 UTC. He created the ransomware, went to sleep (it was 2:22 morning for him, and spent the whole day “working”… ) and 7 hours later (around 12/05 00:00 UTC), the first sample was seen somewhere in the world. Does it make sense? Or maybe, he spent that hours joining the ransomware to the EternalBlue exploit. Or maybe he was a Spanish guy (UTC+2 at the time) and, just when ready, he let the file go and Palo Alto detected it right away… Remember the word “Hola” is embedded in the assembly.
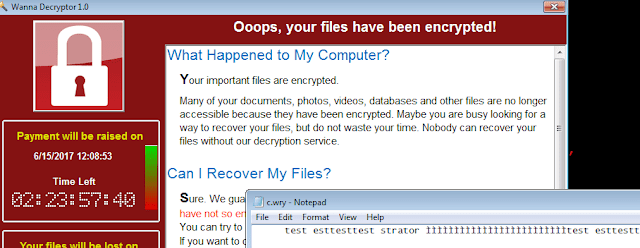
Regarding interesting strings… another from version 1.0, is this “test esttesttest strator” that appears in c.wry, where some .onion and dropbox URLs are… draw your own conclusions.
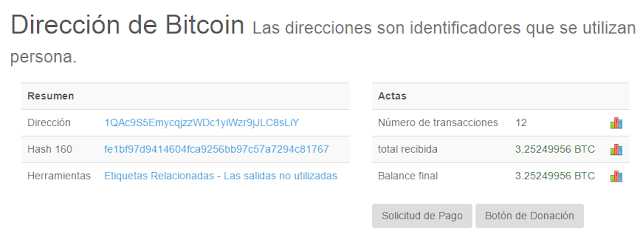
And last but not least. We all know the attacker did not take the money out of the wallets in version 2.0. Too risky, maybe. But just checking the wallets in version 1.0, we can tell he did not get the money from victims of version 1.0, days before the “world attack”. These are just two of the wallets in version 1.0, with transactions from early May… and the money is still there.
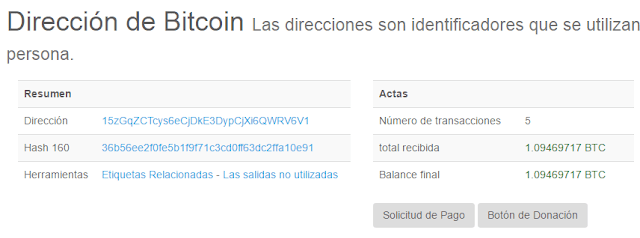 |
| Just two of the wallets in version 1.0, with transactions from early May… and the money is still there |
Conclusions?
Playing attribution is risky.
These times and hours may be legitimate, or directly fake. He may like
or hate Messi. The problem is, since these are all local times, we have not found an UTC reference that enables us to know the precise timezone of the attacker. We may suspect it is UTC +9 (Korea time). However, the real thing is that, we can only make some assumptions.
- The attacker starts the attack the 9th.
- He spends the 10th and 12th creating it, almost for all day long.
- For some reason, he spends more time editing Chinese language files.
- Word is configured with Korean as default languge.
- His timezone may be between UTC+2 and UTC+12
Innovación y laboratorio







Good Post
Vmware Training in Chennai
CCNA Training in Chennai
Angularjs Training in Chennai
Google CLoud Training in Chennai
Red Hat Training in Chennai
Linux Training in Chennai
Rhce Training in Chennai
Vmware Training in Chennai
CCNA Training in Chennai
Angularjs Training in Chennai
Google CLoud Training in Chennai
Red Hat Training in Chennai
Linux Training in Chennai
Rhce Training in Chennai