We are going to try to clarify some common doubts about this vulnerability, since it has turned up with some confusing data about whether it was patched or not, what it is called, how it can be exploited and how to protect yourself.
Why Is It Coming Out Now and Without a Patch?
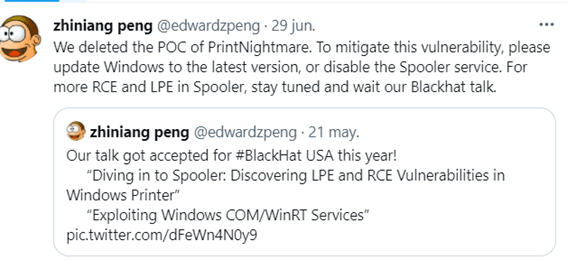
Zhiniang Peng and Xuefeng Li are going to Black Hat this year to show how to exploit vulnerabilities in the Windows print queue. For some reason they published all the details of a vulnerability they initially called CVE-2021-1675 but later confirmed as CVE-2021-34527 and with the ” printNightmare” alias”.

They published the exploit on github and shortly after they regretted it and deleted it. But it was too late and it was copied in many other places with other formats, languages, etc.
Is It Patched?
No. Initially it was thought to be somehow a variant of CVE-2021-1675, patched on June 8th, but no. It’s a different bug. However, having or not the patch influences the decision flow to be more or less vulnerable.
How do they attack me?
You need to have a valid user on the system or on the network (hosted on the domain controller) and at the same time, the domain controller must allow remote printing. These are the basic conditions. From there on, anyone with not too much knowledge can inject a DLL into the server with SYSTEM privileges, which in practice means full control of the whole network.
Am I vulnerable?
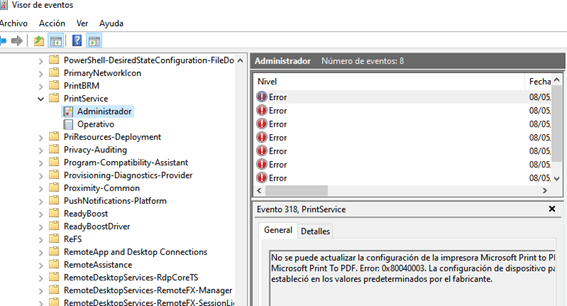
Probably yes. All Windows are potentially vulnerable. There are already exploits of all kinds. It is very easy to exploit. If the print queue is accessible and the patch is not applied, the exploit will work. The print queue is not directly accessible through a port so regulating access through the firewall won’t help (unless you want to block ports 445 and 137 which are more delicate to manage).
If the patch is on a domain controller, and the attacker is in the pre-2000 compatibility group, the exploit will work. “Pre-windows 2000 Compatible Access” is a group that relaxes and adapts certain measures so that 9x systems can run on the controller. This is not as uncommon as it may seem.
If it is not a domain controller, then look at another parameter since the above does not apply. Look at the status of “point and print” and “EnableLUA”. The first one is a one-click printing system, i.e., automatic driver installation if necessary. The second one has to do with UAC and if it is disabled, the exploit will work. It looks much clearer in this decision tree.
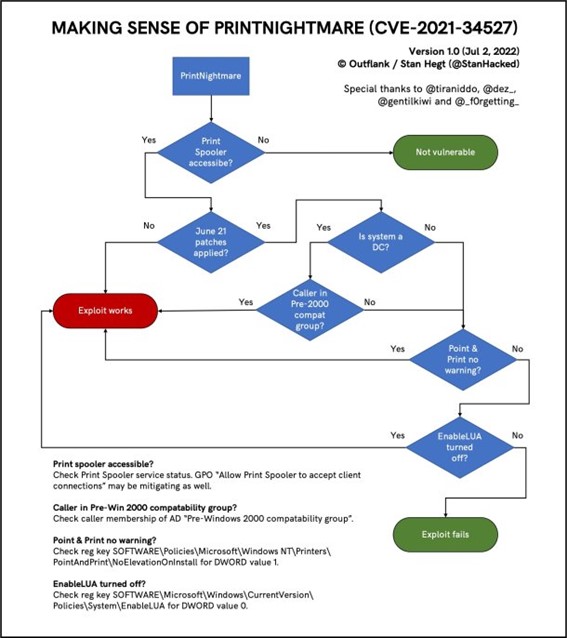
How can I protect myself?
It depends on what you want to sacrifice. If you do not need to print at all, the easiest thing to do is to turn the service off and disable it.
If you need to print locally but do not want anyone to be able to exploit this remotely, you can disable remote printing from the GPO.
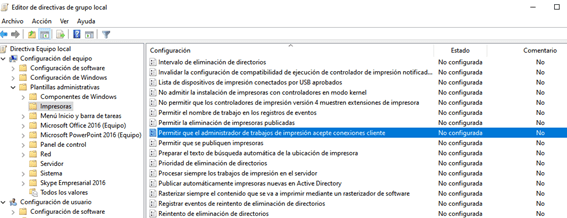
This is achieved by disabling the “Allow Print Spooler to accept client connections”. It is necessary to restart the service.
One thing that is disabled by default but is worth making sure of is point and print:
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
- NoWarningNoElevationOnInstall = 0
- NoWarningNoElevationOnUpdate = 0
What happens if you want to print in all conditions from the outside and the inside? A riskier formula, but one that allows you to operate more freely, is to change the permissions.
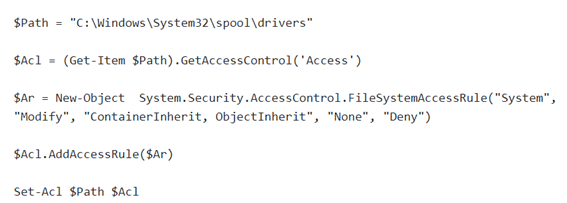
With this hack, the impact is that no more printers can be added to the system, but the exploit will not work, but the bug will still be there. It is risky but seems to be effective. More info here: https://blog.truesec.com/2021/06/30/fix-for-printnightmare-cve-2021-1675-exploit-to-keep-your-print-servers-running-while-a-patch-is-not-available/
How do I know if I am being attacked??
Here Microsoft has published some Microsoft 365 data: https://aka.ms/printspooler-rce-ahq
Here are details on how to detect it with several manufacturers: https://github.com/LaresLLC/CVE-2021-1675
It is also a very good idea to enable the Windows-specific registry: